Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6A6
•
0 recomendaciones•140 vistas
Laptop recovery story of How the Absolute recovery team recovered a stolen Dell Latitude laptop from Albuquerque USA. Visit: http://www3.absolute.com/lojackforlaptops/ to recover and track your stolen laptops or mac.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Más contenido relacionado
Destacado (8)
Presentatie vanbuurt ICT, Microsoft Office Specialist bijeenkomst 10 december...

Presentatie vanbuurt ICT, Microsoft Office Specialist bijeenkomst 10 december...
Más de Absolute LoJack
Más de Absolute LoJack (10)
Laptop Theft Recovery Case from Absolute Software – Case Number 8E0D2

Laptop Theft Recovery Case from Absolute Software – Case Number 8E0D2
Laptop Theft Recovery Cases from Absolute Software – Case Number 7I7D8

Laptop Theft Recovery Cases from Absolute Software – Case Number 7I7D8
Dell XPS Laptop Theft Recovery Case from Absolute Software – Case Number 8B2H0

Dell XPS Laptop Theft Recovery Case from Absolute Software – Case Number 8B2H0
Smartphone Theft Recovery Cases from Absolute Software – Case Number 9E1Z5

Smartphone Theft Recovery Cases from Absolute Software – Case Number 9E1Z5
Laptop Theft Recovery Cases from Absolute Software – Case Number 8G2Z9

Laptop Theft Recovery Cases from Absolute Software – Case Number 8G2Z9
Laptop Theft Recovery Cases from Absolute Software – Case Number 8G1E6

Laptop Theft Recovery Cases from Absolute Software – Case Number 8G1E6
Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9

Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9
Laptop Theft Recovery Cases from Absolute Software – Case Number 8C5A7

Laptop Theft Recovery Cases from Absolute Software – Case Number 8C5A7
Laptop Theft Recovery Cases from Absolute Software – Case Number 7I5B2

Laptop Theft Recovery Cases from Absolute Software – Case Number 7I5B2
Último
Último (20)
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6A6
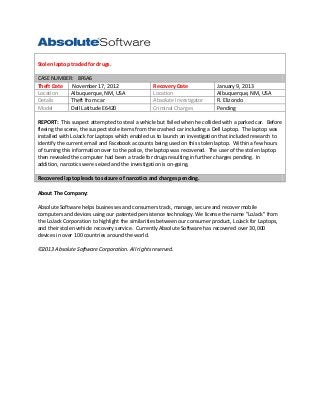
- 1. Stolen laptop traded for drugs. CASE NUMBER: 8F6A6 Theft Date November 17, 2012 Location Albuquerque, NM, USA Details Theft from car Model Dell Latitude E6420 Recovery Date Location Absolute Investigator Criminal Charges January 9, 2013 Albuquerque, NM, USA R. Elizondo Pending REPORT: This suspect attempted to steal a vehicle but failed when he collided with a parked car. Before fleeing the scene, the suspect stole items from the crashed car including a Dell Laptop. The laptop was installed with LoJack for Laptops which enabled us to launch an investigation that included research to identify the current email and Facebook accounts being used on this stolen laptop. Within a few hours of turning this information over to the police, the laptop was recovered. The user of the stolen laptop then revealed the computer had been a trade for drugs resulting in further charges pending. In addition, narcotics were seized and the investigation is on-going. Recovered laptop leads to seizure of narcotics and charges pending. About The Company: Absolute Software helps businesses and consumers track, manage, secure and recover mobile computers and devices using our patented persistence technology. We license the name "LoJack" from the LoJack Corporation to highlight the similarities between our consumer product, LoJack for Laptops, and their stolen vehicle recovery service. Currently Absolute Software has recovered over 30,000 devices in over 100 countries around the world. ©2013 Absolute Software Corporation. All rights reserved.
