How a Proxy Server Works
•Descargar como PPTX, PDF•
0 recomendaciones•3,419 vistas
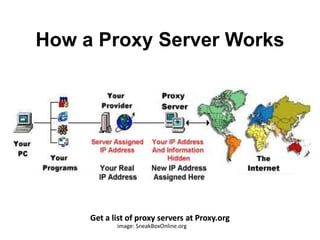
A proxy server routes web requests through an intermediary server to access sites that may be blocked locally. It works by sending requests from a user's computer to the proxy server instead of directly to the destination website, and then the proxy server forwards the request and sends the response back to the user, providing an indirect channel to access blocked content. The document recommends getting a list of proxy servers from Proxy.org and routes traffic to circumvent blocks, while also mentioning the related topic of Tor for anonymous web browsing.
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Destacado
Destacado (20)
Más de Mer Joyce
Más de Mer Joyce (20)
Contention Beyond Social Movements: Activism and its Benefits

Contention Beyond Social Movements: Activism and its Benefits
Hybrid Civil Society: How New and Historic Networks Collaborate for Change

Hybrid Civil Society: How New and Historic Networks Collaborate for Change
21st Century Civil Society: Implications for Open Government

21st Century Civil Society: Implications for Open Government
Último
Último (20)
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
How a Proxy Server Works
- 1. How a Proxy Server Works Get a list of proxy servers at Proxy.orgGet a list of proxy servers at Proxy.orgGet a list of proxy servers at Proxy.orgGet a list of proxy servers at Proxy.orgGet a list of proxy servers at Proxy.orgGet a list of proxy servers at Proxy.org image: SneakBoxOnline.org
- 2. A proxy web site helps you get around a local Internet block by routing your site request around the block. You computer
- 6. Thank You Digital Activism Workshop presented by: Next: Tor