IP Address: A Unique ID for Devices on a Network
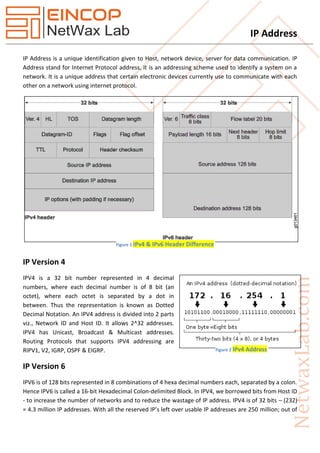
- 1. IP Address IP Address is a unique identification given to Host, network device, server for data communication. IP Address stand for Internet Protocol address, it is an addressing scheme used to identify a system on a network. It is a unique address that certain electronic devices currently use to communicate with each other on a network using internet protocol. IP Version 4 IPV4 is a 32 bit number represented in 4 decimal numbers, where each decimal number is of 8 bit (an octet), where each octet is separated by a dot in between. Thus the representation is known as Dotted Decimal Notation. An IPV4 address is divided into 2 parts viz., Network ID and Host ID. It allows 2^32 addresses. IPV4 has Unicast, Broadcast & Multicast addresses. Routing Protocols that supports IPV4 addressing are RIPV1, V2, IGRP, OSPF & EIGRP. IP Version 6 IPV6 is of 128 bits represented in 8 combinations of 4 hexa decimal numbers each, separated by a colon. Hence IPV6 is called a 16-bit Hexadecimal Colon-delimited Block. In IPV4, we borrowed bits from Host ID - to increase the number of networks and to reduce the wastage of IP address. IPV4 is of 32 bits – (232) = 4.3 million IP addresses. With all the reserved IP’s left over usable IP addresses are 250 million; out of Figure 2 IPv4 Address Figure 1 IPv4 & IPv6 Header Difference
- 2. IP Address which 10% are in use. The class B addresses are already exhausted, whereas class A and C IP addresses are still available; but officially by 2008 all IP addresses are dieing. Since IPV6 provides us with more number of addresses when compared to IPV4 i.e., IPV6 supports 2128(about 3.4×1038) addresses, or approximately 5×1028 addresses for each of the 6.5 billion people alive today. IPv4 Classes IP Addresses can be classified into five classes A, B, C, D and E. Each class consists of a contiguous subset of the overall IPv4 address range. Figure 3 IPv6 Address Figure 5 Available Network & Host Bit in IP Classes Figure 4 IP Range in Different Classes
- 3. IP Address Class A Class A addresses are IP addresses that are assigned to network devices, such as computers, and include all addresses in which the first bit of the first octet is set to 0 (zero). This includes all values from 00000001 to 01111111, or 1 to 127. For Class A networks, the first octet represents a network ID that is defined in the address by a subnet mask. The network ID is not allowed to have all its bits set to 0 or all bits set to 1. The 127 network ID is excluded from this address class. Thus, 126 possible Class A networks are available to organizations around the world. With only 126 Class A networks, owning one puts you in an exclusive club. You can no longer acquire a network block of addresses, and when possible, IANA gets them back from the registered owners. Getting addresses back allows IANA to redistribute addresses in a more efficient and temporary manner. Class B Class B addresses are IP addresses that are assigned to network devices, such as computers, and include all addresses in which the first two bits of the first octet are 10. This includes all values from 10000000 to 10111111, or 128 to 191. The definition of the Class B network is represented with a subnet mask, but the Class B network ID is made up of the values in the first two octets. Unlike Class A networks, all network IDs in this range are available for use. Class C Class C addresses are IP addresses that are assigned to network devices, such as computers, and include all addresses in which the first three bits of the first octet are set to 110. This includes all values from 11000000 to 11011111, or 192 to 223. The default subnet mask for Class C networks defines the first three octets as the network ID for these networks. Like with Class B networks, all the network IDs are available for use on networks. This is the last of the network classes that will be used for network devices on a TCP/IP network. Figure 6 IP Address Class A Figure 7 IP Address Class B Figure 8 IP Address Class C
- 4. IP Address Class D Class D network addresses are not assigned to devices on a network. These addresses are used for special-purpose, multicast applications (such as video and audio-streaming applications). These addresses all need to be registered with IANA to be used globally. Addresses in this class have the first bits of the first octet set to 1110, yielding addresses in the first octet ranging from 11100000 to 11101111, or 224 to 239. These addresses are not defined by a normal subnet mask; instead, each address is used for a specific purpose. And because each address is individually used, it uses a 255.255.255.255 mask. Class E If Class D is special, Class E addresses are even more special. There is no defined use for this address class. Officially, it is listed as reserved for usage and testing by IANA and the Internet Research Task Force (IRTF). In fact, as of RFC3330 in 2002, Class E was updated to “reserved for future use.” Class E comprises absolutely all valid addresses with 240 or higher in the first octet. The first bits of the first octet is 1111, which yields addresses from 11110000 to 11111110 — or technically, 11111111 — which, in decimals, are 240 to 254 — or 255. Because this address class is not being used for address allocation, you cannot know what the network ID, which defines the valid addresses in a range. So the inclusion of 255 at the end of the range is moot because this address range is not available for you to use. All you need to know is that by definition Class E includes all valid addresses higher than Class D. IP Addressing There are four forms of IP addressing, each with its own unique properties. 1. Unicast: The most common concept of an IP address is in unicast addressing, available in both IPv4 and IPv6. It normally refers to a single sender or a single receiver, and can be used for both sending and receiving. Usually, a unicast address is associated with a single device or host, but it is not a one-to-one correspondence. Some individual PCs have several distinct unicast addresses, each for its own distinct purpose. Sending the same data to multiple unicast addresses requires the sender to send all the data many times over, once for each recipient. 2. Broadcast: In IPv4 it is possible to send data to all possible destinations ("all-hosts broadcast"), which permits the sender to send the data only once, and all receivers receive a copy of it. In the IPv4 protocol, the address 255.255.255.255 is used for local broadcast. In addition, a directed (limited) broadcast can be made by combining the network prefix with a host suffix composed entirely of binary 1s. For example, the destination address used for a directed broadcast to
- 5. IP Address devices on the 192.0.2.0/24 network is 192.0.2.255. IPv6 does not implement broadcast addressing and replaces it with multicast to the specially-defined all-nodes multicast address. 3. Multicast: A multicast address is associated with a group of interested receivers. In IPv4, addresses 224.0.0.0 through 239.255.255.255 (the former Class D addresses) are designated as multicast addresses. IPv6 uses the address block with the prefix ff00::/8 for multicast applications. In either case, the sender sends a single datagram from its unicast address to the multicast group address and the intermediary routers take care of making copies and sending them to all receivers that have joined the corresponding multicast group. 4. Anycast: Like broadcast and multicast, anycast is a one-to-many routing topology. However, the data stream is not transmitted to all receivers, just the one which the router decides is logically closest in the network. Anycast address is an inherent feature of only IPv6. In IPv4, anycast addressing implementations typically operate using the shortest-path metric of BGP routing and do not take into account congestion or other attributes of the path. Anycast methods are useful for global load balancing and are commonly used in distributed DNS systems. Automatically Assigned Addresses There are several IP addresses that are automatically assigned when you setup a home network. These default addresses are what allow your computer and other network devices to communicate and broadcast information over your network. Below is the most commonly assigned network addresses in a home network. 192.168.1.0 0 is the automatically assigned network address. 192.168.1.1 1 is the commonly used address used as the gateway. 192.168.1.2 2 is also a commonly used address used for a gateway. 192.168.1.3 - 254 Addresses beyond 3 are assigned to computers and devices on the network. 192.168.1.255 255 is automatically assigned on most networks as the broadcast address. If you have ever connected to your home network, you should be familiar with the gateway address or 192.168.1.1, which is the address you use to connect to your home network router and change its settings. Getting an IP Address By default the router you use will assign each of your computers their own IP address, often using NAT to forward the data coming from those computers to outside networks such as the Internet. If you need to register an IP address that can be seen on the Internet, you must register through InterNIC or use a web host that can assign you addresses.
- 6. IP Address Anyone who connects to the Internet is assigned an IP address by their Internet Service Provider (ISP) who has registered a range of IP addresses. Modifications to IP Addressing IP blocking and firewalls Firewalls perform Internet Protocol blocking to protect networks from unauthorized access. They are common on today's Internet. They control access to networks based on the IP address of a client computer. Whether using a blacklist or a whitelist, the IP address that is blocked is the perceived IP address of the client, meaning that if the client is using a proxy server or network address translation, blocking one IP address may block many individual computers. IP address translation Multiple client devices can appear to share IP addresses: either because they are part of a shared hosting web server environment or because an IPv4 network address translator (NAT) or proxy server acts as an intermediary agent on behalf of its customers, in which case the real originating IP addresses Figure 9 Process for getting IP
- 7. IP Address might be hidden from the server receiving a request. A common practice is to have a NAT hide a large number of IP addresses in a private network. Only the "outside" interface(s) of the NAT need to have Internet-routable addresses. Most commonly, the NAT device maps TCP or UDP port numbers on the side of the larger, public network to individual private addresses on the masqueraded network. In small home networks, NAT functions are usually implemented in a residential gateway device, typically one marketed as a "router". In this scenario, the computers connected to the router would have private IP addresses and the router would have a public address to communicate on the Internet. This type of router allows several computers to share one public IP address.
