August 2012 cyber attacks timeline part I
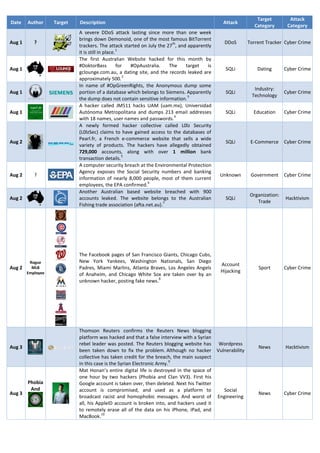
- 1. Target Attack Date Author Target Description Attack Category Category A severe DDoS attack lasting since more than one week brings down Demonoid, one of the most famous BitTorrent Aug 1 ? th DDoS Torrent Tracker Cyber Crime trackers. The attack started on July the 27 , and apparently 1 it is still in place. The first Australian Website hacked for this month by #DoktorBass for #OpAustralia. The target is Aug 1 SQLi Dating Cyber Crime gclounge.com.au, a dating site, and the records leaked are 2 approximately 500. In name of #OpGreenRights, the Anonymous dump some Industry: Aug 1 portion of a database which belongs to Siemens. Apparently SQLi Cyber Crime 3 Technology the dump does not contain sensitive information. A hacker called JM511 hacks UAM (uam.mx), Universidad Aug 1 Autónoma Metropolitana and dumps 213 email addresses SQLi Education Cyber Crime 4 with 18 names, user names and passwords. A newly formed hacker collective called L0lz Security (L0lzSec) claims to have gained access to the databases of Pearl.fr, a French e-commerce website that sells a wide Aug 2 SQLi E-Commerce Cyber Crime variety of products. The hackers have allegedly obtained 729,000 accounts, along with over 1 million bank 5 transaction details. A computer security breach at the Environmental Protection Agency exposes the Social Security numbers and banking Aug 2 ? Unknown Government Cyber Crime information of nearly 8,000 people, most of them current 6 employees, the EPA confirmed. Another Australian based website breached with 900 Organization: Aug 2 accounts leaked. The website belongs to the Australian SQLi Hacktivism 7 Trade Fishing trade association (afta.net.au). The Facebook pages of San Francisco Giants, Chicago Cubs, Rogue New York Yankees, Washington Nationals, San Diego Account Aug 2 MLB Padres, Miami Marlins, Atlanta Braves, Los Angeles Angels Sport Cyber Crime Employee Hijacking of Anaheim, and Chicago White Sox are taken over by an 8 unknown hacker, posting fake news. Thomson Reuters confirms the Reuters News blogging platform was hacked and that a false interview with a Syrian rebel leader was posted. The Reuters blogging website has Wordpress Aug 3 News Hacktivism been taken down to fix the problem. Although no hacker Vulnerability collective has taken credit for the breach, the main suspect 9 in this case is the Syrian Electronic Army. Mat Honan’s entire digital life is destroyed in the space of one hour by two hackers (Phobia and Clan VV3). First his Phobia Google account is taken over, then deleted. Next his Twitter And account is compromised, and used as a platform to Social Aug 3 News Cyber Crime broadcast racist and homophobic messages. And worst of Engineering all, his AppleID account is broken into, and hackers used it to remotely erase all of the data on his iPhone, iPad, and 10 MacBook.
- 2. After the Reuters blogging platform, the ReutersTech Twitter account is hacked on Sunday. The two events appear to be related; in both cases, fake news was posted in Account Aug 4 News Hacktivism relation to the currently ongoing Syrian Civil War. The Hijacking ReutersTech account was hijacked and renamed to 11 ReutersME (ME stands for Middle East). Gizmodo's Twitter account is hacked through former Social Aug 4 employee Mat Honan’s Twitter account, which has been News Cyber Crime 12 Engineering hacked first. JM511 hacks nnottscamra.co.uk, (the website dedicated to the campaign for Real Ale) and dumps 135 records Organization: Aug 4 SQLi Cyber Crime containing usernames. Email addresses and phone Other 13 numbers. In name of Operation India, the personal website of Kapil Sibal (kapilsibalmp.com), India’s Minister of Human Resource Development and Minister of Communications Organization: Aug 6 and Information Technology, is breached by Anonymous, Unknown Hacktivism Political who publish a number of screenshots on the social media website Facebook to demonstrate that they gained access 14 to the site’s backend. PBBans, the community of server admins dedicated to fight Aug 6 ? cheaters is the target of a massive distributed denial-of- DDoS Online Services Cyber Crime 15 service. Anonymous hacks the Indiana Lake City Police Association Law Aug 6 (lakecountysheriff.com) and dumps 152 records with Emails SQLi Hacktivism 16 Enforcement and Street Addresses. The online activist group “Anonymous” shuts down three government websites in retaliation for last week’s Organization: DDoS Hacktivism government shutdown of the popular Ukrainian torrent Copyright tracker Demonoid where users share pirated videos. List of 17 targets include: Organization: Aug 7 DDoS Hacktivism Ukrainian Anti-Piracy Association (apo.kiev.ua); Copyright Ukrainian Agency for Copyright and Related Rights (uacrr.kiev.ua); The National Television and Radio Broadcasting DDoS News Hacktivism Council of Ukraine (nrada.gov.ua) WikiLeaks is under a sustained large scale DDoS attacks Organization: Aug 7 since August 3. The attack is claimed by a group called DDoS Hacktivism 18 Activism @AntiLeaks. Haines City's government website (ci.haines-city.fl.us) is AYYILDIZIIM hacked and taken down. A group calling itself AYYILDIZIIM- Aug 7 -Gen~Reis Unknown Government Cyber Crime Gen~Reis claims the credit for the hacking that redirected 19 visitors to its website, which a Turkish gaming site. On the wake of the attack against Wikileaks, also Organization: Aug 8 ? cabledrum.net, the search engine for cablegate files is the DDoS Hacktivism 20 Activism target of a sustained DDoS attack. Another attack in the name of #OpAustralia. In this round @_ignit3 the target is the Australian Institute of Business Brokers from website (aibb.org.au), that is hacked and has a leak of data Organization: Aug 8 SQLi Hacktivism posted online. The leak contains usernames and encrypted Industry passwords of over 250 people from the websites 21 22 database. In any case AIBB denies the claim. An Arab hacking group called "Remember Emad" claims to have taken control of an Israeli server belonging to Remember Cyber Aug 8 Emad WebGate, an Israeli ISP. The group published lists of Unknown ISP Warfare passwords for Facebook pages, credit card numbers and 23 email addresses belonging to Israelis. Operation Australia continues, and as part of the operation hackers take down with a DDoS attack two important high Law DDoS Hacktivism profile sites: 24 Enforcement Aug 8 Department Of Defense Intelligence and Security: (dsd.gov.au); Law Australian Security Intelligence Organisation DDoS Hacktivism Enforcement (asio.gov.au).
- 3. Researchers from Kaspersky Lab release the details on Gauss, a dangerous banking malware which is believed to be state-sponsored, and has been deployed in August- Cyber Aug 9 ? September 2011. It is derived from the Stuxnet Platform APT Finance Espionage and is capable of stealing sensitive information from infected Windows computers. List of targets include: 25 Lebanon, Israel, Palestinian Authority, etc. Blizzard Entertainment, the maker of both World of Warcraft and the Diablo series of games, says that its internal security network had been breached. The target is Battle.net, the company's proprietary online gaming service for connecting players in its games. The company said that email addresses and other information for all Battle.net Aug 9 ? ? Online Gaming Cyber Crime players outside China were taken, along with scrambled passwords. While Blizzard said it would be very challenging for the hackers to actually access any accounts or obtain financial information, the company still recommended that 26 its members change their passwords just to be safe. Millions of users could potentially be affected Two Nepalese government websites, the National Information Technology Center (NITC) and the Office of the Prime Minister and Council Minister (nitc.gov.np and opmcm.gov.np respectively), have been compromised and Cyber Aug 9 ? RAT Government injected with malicious code. The aim of this injection is to Espionage install, through successfully exploiting a Java weakness, a backdoor that is also dubbed "Zegost" on the systems of 27 visitors to these websites. OpDemonoid continues. The list of the targets increases and DDoS Military Hacktivism 28 involves: The Ukrainian Ministry of Defense (mil.gov.ua); DDoS Government Hacktivism The Vinnitsa region (dai.vn.ua); Aug 9 DDoS Government Hacktivism The Cabinet of Ministers; The Foreign Intelligence Service of Ukraine DDoS Government Hacktivism (fisu.gov.ua), The Svalyava district (svalyava-vlada.gov.ua). DDoS Government Hacktivism Another example of hackers targeting road signs: Hackers Industry: Aug 9 ? reprogrammed a computerized road sign in Utah and made Unknown Cyber Crime 29 Transportation it flash a homophobic phrase: “GOD HATES GAYS.” The hacker known as Hitcher hacks the HP Training Center Industry: Aug 12 Hitcher (hptrainingcenter.com) and defaces it in name of Defacement Hacktivism 30 Technology OpFreePalestine. Another torrent site, scanbits.org, has fallen victim to hackers who have obtained access to its database and Aug 13 ? grabbed a copy of it totaling over 300mb. Along with the SQLi Torrent Tracker Cyber Crime dump 9000+ user accounts are dumped with full account 31 information, emails, encrypted passwords and more. The National Council of Investigation and Security Law Aug 13 V0dka (nciss.org) is hacked by v0dka, who defaces the website and SQLi Cyber Crime 32 Enforcement dumps 253 email accounts with their full names. Anonymous Hackers team up with a collective known as The Elite Society and a hacker called @DramaSett3r and breach Defacement Government Hacktivism several government websites in Uganda. Targets include: The Prime Minister Website (opm.go.ug); Organization: Defacement Hacktivism Uganda law society (uls.or.ug); Law Aug 14 Ugandan National TV (nTV.co.ug) The country’s Justice Law and Order Society Defacement Government Hacktivism (jlos.go.ug) The sites are defaced in support of Ugandan Lesbian, Gay, Defacement Government Hacktivism 33 Bisexual, Transgender and Intersex (LGBTI) rights. The popular Russian BitTorrent website RUTracker.org is Aug 14 ? 34 Unknown Torrent Tracker Cyber Crime breached and defaced by an unknown group of hackers.
- 4. Trusteer announces to have discovered a sophisticated Man Major in the Browser (MitB) enterprise attack targeting VPN users Industry: Aug 14 ? International at a major international airport hub. Using the Citadel MitB Cyber Crime Transportation Airport Trojan, criminals target employees to steal their credentials 35 for accessing internal airport applications. AT&T is the victim of a distributed denial-of-service attack aimed at its DNS (Domain Name System) infrastructure and Aug 15 ? DDoS TELCO Cyber Crime capable to disrupt data traffic for some of the company's 36 customers. For the second time in two weeks, the blogging platform of the Reuters News website is hacked and a false posting Aug 15 ? Unknown News Cyber Crime saying Saudi Arabia's Foreign Minister Prince Saud al-Faisal 37 had died is illegally posted on a Reuters journalist's blog. The Saudi Oil Company Saudi Aramco is the victim of a sophisticated Cyber Attack. The company declares that “production has not been affected” and even if the virus affected some computers, it did not penetrate key Shamoon Cyber Aug 15 ? Industry: Oil components of the network, even if the impacts seem Malware Espionage 38 different. Few hours later, more detail appear about Shamoon, what appears to be the latest huge-scale cyber 39 attack in Middle East. 1 http://torrentfreak.com/demonoid-to-suffer-prolonged-downtime-after-ddos-attack-120727/ 2 http://datalossdb.org/incidents/7202-506-email-addresses-and-passwords-dumped-on-the-internet 3 http://ozdc.net/archives.php?aid=2870 4 http://datalossdb.org/incidents/7182-213-email-addresses-with-18-names-user-names-and-passwords-dumped-on-the-internet 5 http://news.softpedia.com/news/Pearl-fr-Hacked-by-L0lzSec-700-000-Accounts-Possibly-Compromised-284722.shtml 6 http://www.bizjournals.com/washington/news/2012/08/02/epa-security-breach-exposes-personal.html 7 http://www.cyberwarnews.info/2012/08/02/australian-fishing-trade-association-afta-hacked-900-accounts-leaked-by- doktorbass/ 8 http://deadspin.com/5931360/new-york-yankees-facebook-page-announces-derek-jeter-to-miss-rest-of-season-due-to-sex- change 9 http://www.theatlanticwire.com/technology/2012/08/reuters-blogs-hacked-fake-story-about-syrian-rebels/55394/# 10 www.wired.com/gadgetlab/2012/08/apple-amazon-mat-honan-hacking/ 11 http://news.cnet.com/8301-1023_3-57486971-93/reuters-twitter-account-hijacked-fake-tweets-sent/ 12 http://www.zdnet.com/gizmodos-twitter-account-hacked-7000002130/ 13 http://ozdc.net/archives.php?aid=2869 14 http://news.softpedia.com/news/Site-of-India-s-Minister-of-Communications-and-IT-Hacked-by-Anonymous-285097.shtml 15 http://news.softpedia.com/news/PBBans-Relocates-Servers-After-Being-Hit-by-DDOS-Attack-285353.shtml 16 http://ozdc.net/archives.php?aid=2872 17 http://www.kyivpost.com/content/ukraine/anonymous-attacks-ukrainian-government-websites-and-threatens-with-further- action-311234.html 18 http://news.softpedia.com/news/WikiLeaks-Taken-Down-by-DDOS-Attack-AntiLeaks-Takes-Credit-285771.shtml 19 http://www.newschief.com/article/20120807/NEWS/208075028/-1/opinion?Title=Website-hacked-staff-working-to-get-it- back-up&tc=ar 20 https://twitter.com/Cabledrummer/status/233030298240155649 21 http://www.cyberwarnews.info/2012/08/08/australian-institute-of-business-brokers-hacked-for-opaustralia/ 22 http://www.computerworld.com.au/article/433131/australian_institute_business_brokers_denies_anonymous_password_breach/ 23 http://www.israelhayom.com/site/newsletter_article.php?id=5349 24 http://www.cyberwarnews.info/2012/08/08/dsd-asio-websites-attacked-by-anonymous-for-opaustralia/ 25 http://www.securelist.com/en/blog/208193767/Gauss_Nation_state_cyber_surveillance_meets_banking_Trojan 26 http://news.yahoo.com/blogs/technology-blog/blizzard-battle-net-gets-hacked-says-members-change-220027322.html 27 http://community.websense.com/blogs/securitylabs/archive/2012/08/08/nepalese-government-websites-compromised-to- serve-zegost-backdoor.aspx 28 http://news.softpedia.com/news/OpDemonoid-Ukrainian-Ministry-of-Defense-Site-Taken-Down-by-Anonymous-285933.shtml 29 http://rt.com/usa/news/utah-road-hackers-sign-389/ 30 http://news.softpedia.com/news/HP-Training-Center-Defaced-by-Hitcher-in-Protest-Against-Israel-286278.shtmlx 31 http://www.cyberwarnews.info/2012/08/13/torrent-site-scanbits-org-hacked-9000-accounts-leaked/ 32 http://cylaw.info/?p=1087 33 http://www.cyberwarnews.info/2012/08/15/uganda-government-under-attack-by-anonymous-for-anti-lgbt/ 34 http://news.softpedia.com/news/RUTracker-Hacked-Displays-Domain-Seized-by-ICE-Message-286486.shtml 35 http://www.trusteer.com/blog/citadel-trojan-targets-airport-employees-with-vpn-attack
- 5. 36 http://www.pcworld.com/businesscenter/article/260940/atandt_hit_by_ddos_attack_suffers_dns_outage.html 37 http://www.reuters.com/article/2012/08/15/net-us-hacking-reuters-saudi-idUSBRE87E0HU20120815 38 http://hackmageddon.com/2012/08/16/another-massive-cyber-attack-in-middle-east/ 39 http://hackmageddon.com/2012/08/17/heres-shamoon/
