A New Breed of Identity Management
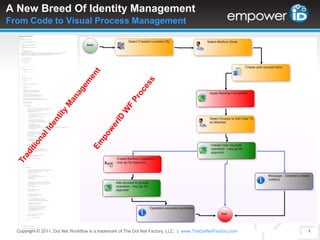
- 1. A New Breed Of Identity ManagementFrom Code to Visual Process Management EmpowerID WF Process Traditional Identity Management Copyright © 2011. Dot Net Workflow is a trademark of The Dot Net Factory, LLC. |www.TheDotNetFactory.com 1
- 2. User Manager: Role-Based User Provisioning and Delegated Administration
- 3. Introducing User ManagerWorkflow Automation of User Lifecycle Management According to the Gartner Group, organizations can save 300% with automated user provisioning The Challenge During good and bad economic times there is an increase in employee turnover. Provisioning user accounts and granting access across multiple systems is a costly and time consuming process. Quickly and efficiently deprovisioning access when and employee leaves the organization is even more time consuming and error prone, often exposing an organization to security vulnerabilities. EmpowerID Solution User Manager is a workflow and role-based solution that automates provisioning access for new employees and deprovisioning access when they change positions or leave the organization. Copyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 3
- 4. A request is submitted as a ticket to the helpdesk requesting accounts and access for the new employee The helpdesk has a large backlog of tickets which delays creation of the accounts and postpones employee productivity common ratio for large companies – 1 helpdesk admin/6000 users! In the meantime, the user cannot access resources they need to perform their job – e.g. email, file shares, printers, etc... The helpdesk must search in each system to verify name uniqueness Eventually the accounts are created and access is granted Process Challenges: Manual provisioning requires the involvement of multiple IT staff and a high level of organizational knowledge IT is unable to detect security changes in AD and other systems No automated removal of application and system access Lack of a good audit trail to attest to why access was granted and who approved Copyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 4 When Will I Get Access? Typical Process Before EmpowerID
- 5. 5 Provisioning Routine UserAdministration Change Locations New Project Forgot Password Relationship Ends Password Expires PasswordManagement Deprovisioning Relationship Begins Promotion USERLIFECYCLE Copyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com Identity Lifecycle ManagementManage the Lifecycle of a Person and Their Accounts
- 7. Automates provisioning and deprovisioning with workflow
- 8. Synchronizes user information between systems and provides self-service edit
- 9. Synchronizes passwords and enables self-service reset and unlock (Password Manager)
- 10. Self-service new account registration workflows with approvals
- 11. Delegates role-based administration of people and their accounts
- 12. Achieves continuous compliance through constant enforcement of policiesPerson 6
- 15. Automated deprovisoning of user accounts prevents accumulation of privileges over time and ensures that access is revoked when an employee leaves the organizationCopyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 7 Resource Entitlements Automatic Provisioning and Deprovisioning of Accounts and Resources
- 16. Copyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 8 Resource EntitlementsRole-Based Resource Provisioning and Deprovisioning Resource Entitlements for Contractors in New York Resource Entitlements are policies that automate provisioning, moving, disabling, and deprovisioning resources automatically based upon user Role and Location changes. Automating the initial provisioning of resources when a new Person is created as well as their ongoing management. Resource Entitlements for Standard Employees in Sydney
- 17. Attribute values such as job title, address, company, department, and others can be applied via Role and Location-based policies As users change role or location, these policy-based values are applied and synchronized to connected directories based upon pre-established flow rules Policy-based assignment can dramatically reduce the amount of effort spent manually entering and keeping directory information accurate Accurate information increases the value of your corporate directory as a collaboration tool Copyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 9 Role-Based Attribute Value Assignment Automate maintenance of accurate directory information
- 18. Copyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 10 Policy-Based Attribute ValuesRole-Based Attribute Assignment Policy-Based Attributes for Contractors in New York Policy-based attribute values are policies that automate the maintenance of any directory values that can be defined by Role and Location. Any attribute value of a Person can be assigned by policy and maintained automatically when Role or Location changes. Attribute values will update connected directories based upon attribute flow rules. Policy-Based Attributes for Standard Employees in Sydney
- 20. All changes to group membership are logged and tracked - both changes made within EmpowerID and in the native directory
- 21. Automated role-based group management prevents the accumulation of group membership over timeCopyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 11 Role-Based Dynamic Group Membership Automate maintenance of group membership
- 23. Enable user profile self-service across multiple directories with workflow approvals
- 24. Automatically detect and synchronize directory changes using flexible attribute flow rules
- 25. User interfaces for SharePoint, Windows WPF, and the web
- 26. Only white pages solution built on the Windows Workflow Foundation
- 27. Role-based security for fine-grained control over visibility even in multi-organization configurationsMetadirectoryWeb-Based Corporate White Pages & Self-Service 12
- 28. User Experience: Resource ManagerIndustry’s Only Unified Management Console Copyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 13
- 29. User Experience: Service Catalog Copyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 14
- 30. User Experience: My Workspace Copyright © 2011. empowerID is a trademark of The Dot Net Factory, LLC. |www.empowerid.com 15