Information regarding Virtual Private Networks (VPNs)
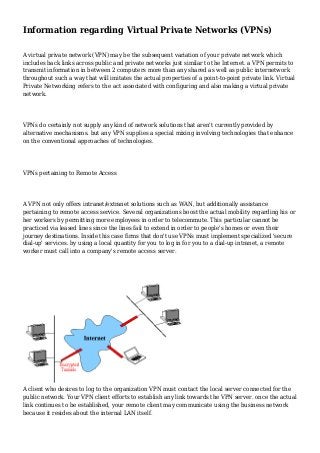
- 1. Information regarding Virtual Private Networks (VPNs) A virtual private network (VPN) may be the subsequent variation of your private network which includes back links across public and private networks just similar to the Internet. a VPN permits to transmit information in between 2 computers more than any shared as well as public internetwork throughout such a way that will imitates the actual properties of a point-to-point private link. Virtual Private Networking refers to the act associated with configuring and also making a virtual private network. VPNs do certainly not supply any kind of network solutions that aren't currently provided by alternative mechanisms. but any VPN supplies a special mixing involving technologies that enhance on the conventional approaches of technologies. VPNs pertaining to Remote Access A VPN not only offers intranet/extranet solutions such as WAN, but additionally assistance pertaining to remote access service. Several organizations boost the actual mobility regarding his or her workers by permitting more employees in order to telecommute. This particular cannot be practiced via leased lines since the lines fail to extend in order to people's homes or even their journey destinations. Inside this case firms that don't use VPNs must implement specialized 'secure dial-up' services. by using a local quantity for you to log in for you to a dial-up intranet, a remote worker must call into a company's remote access server. A client who desires to log to the organization VPN must contact the local server connected for the public network. Your VPN client efforts to establish any link towards the VPN server. once the actual link continues to be established, your remote client may communicate using the business network because it resides about the internal LAN itself.
- 2. VPNs for Internetworking A VPN remote access architecture's extension provides a whole remote network to join the actual nearby network. a server-server VPN connection joins a pair of networks to form an extended intranet or even extranet rather than any client-server connection. VPNs Inside the Firewall To implement limited usage of individual subnets about the private network, intranets use VPN technology. in this mode, VPN clients hook approximately a new VPN server that acts as becoming a gateway in order to computers at the particular rear of it on the subnet. However, it will take benefits of the security features and handiness of VPN technology. VPN Technologies When deploying VPNs more than the Internet, the 2 main considerations are security along with performance. The Particular transmission control protocol and also the Internet weren't premeditated with these concerns within mind, simply because customers as well as programs originally failed to call for security measures or performance. VPNs give anyone the following functions to ensure to protect data: 1] Authentication: It makes sure that the information originates at the origin which it claims 2] Access control: It restricts unauthorized customers from gaining admission to the network 3] Confidentiality: This prevents anybody via studying as well as copying information since it travels across the World wide web 4] Information integrity: The idea ensures that nobody tampers with information since it travels across the Internet To validate customers on a VPN and manage use of network resources, different password-based techniques and also challenge-response systems, for example challenge handshake authentication protocol (CHAP) and remote authentication dial-in user services (RADIUS), as well as hardwarebased tokens along with digital certificates may be used. the safety associated with corporate details as it travels through the particular VPN can be guarded by encrypting the actual data. Private networks are created by using leased hard-wired connections between sites. Via a new single
- 3. corporate consumer these connections are usually devoted to the traffic. Inside order to end up being able to extend that concept towards the Internet, the spot exactly where the traffic through users passes over exactly the same connection, a new tunnel is produced by utilizing a number of protocols. Tunneling delivers senders to embed information throughout IP packets which hide your underlying switching along with routing infrastructure with the Web from both senders and receivers. With exactly the particular same time, these encapsulated information may be protected by simply making use of encryption techniques coming from outsiders. Tunnels consist of two kinds of finish points. They are both an individual personal computer or a LAN using a security gateway. only two combinations of these end points are used throughout designing VPNs. one is most likely in order to be LAN-to-LAN tunneling, which in turn is really a security gateway present each as well as every end point and serves as the interface involving the tunnel and the private LAN, although one other is a client-to-LAN tunnel, the kind usually set up for a mobile user who wishes to connect to the corporate LAN. the mobile user creates the particular tunnel about his end so as to always be able to exchange traffic using the corporate network. There tend to be 4 different protocols are needed to produce VPNs more than the particular Internet: point-to-point tunneling protocol (PPTP), layer-2 forwarding (L2F), layer-2 tunneling protocol (L2TP), as well as IP security protocol (IPSec). Point-to-Point Tunneling Protocol (PPTP) Point-to-Point protocol (PPP) may always be the most popular protocol with regard to remote access towards the Internet. PPTP is situated around the functionality regarding PPP to offer remote access in which can be tunneled via your Web to some destination site. Simply By employing a modified version in the generic routing encapsulation (GRE) protocol, PPTP encapsulates PPP packets, that provide flexibility for you to PPTP to become able to handling protocols apart from IP. PPTP relies on the authentication mechanisms inside PPP―namely password authentication protocol (PAP) and also CHAP due for you to the dependence on PPP. For You To encrypt information PPTP utilizes PPP, but Microsoft additionally supplies a stronger encryption technique known as Microsoft point-to-point encryption (MPPE) with regard to use in inclusion to PPTP. Layer-2 Forwarding (L2F) Like PPTP, L2F has been developed like a protocol regarding tunneling traffic through users to their corporate sites. L2F tunneling can be impartial upon IP; it is capable of perform using frame relay as well as asynchronous transfer mode (ATM). Similar To PPTP, L2F makes use of PPP with regard to authentication of the remote user. L2F allows tunnels to guide a lot much more than 1 connection.
- 4. For authentication of the dial-up user L2F makes use of PPP, however in addition, it need support coming from TACACS+ and RADIUS authentication. L2F defines connections within a new tunnel and allow the tunnel to guide greater than 1 link in a time. You will find two ranges of user authentication, 1st from the ISP prior to setting up the particular tunnel, then once the connection can be set up in the corporate gateway. While L2TP is actually a layer-2 protocol involving OSI, it provides users the same flexibility as PPTP with regard to handling protocols for example IPX and also NetBEUI. Layer-2 Tunneling Protocol (L2TP) To offer dial-up access L2TP utilizes PPP that could be tunneled through the World wide web to some site. L2TP has its own very own tunneling protocol. L2TP transport will be defined for any number of packet switching media including X.25, frame-relay and also ATM. L2TP makes use of IPSec's encryption solutions to strengthen the particular encryption with the data it handles. It utilizes PPP pertaining to dial-up links. L2TP includes the particular PAP as well as CHAP authentication mechanisms inside PPP. PPTP, L2F and also L2TP almost all do not really include encryption or even processes for managing the cryptographic keys required for encryption within their specifications. Pertaining To encryption and crucial management throughout IP environment L2TP regular recommends that IPSec end up being used. IP Safety Protocol (IPSec) IPSec provides authentication or even encryption of every IP packet or use each operations about the packet for sender. 2 different methods utilized by IPSec pertaining to packet authentication along with encryption are called modes. in transport mode only the transport-layer segment associated with an IP packet is actually authenticated or encrypted. Your tunnel node approach, entire IP packet is actually authenticated or encrypted. For IP environment IPSec is best VPN remedy as it consists associated with security measures such as authentication, encryption as well as important management inside its standards set. If you are trying to privately browse the particular web, share files, and also access streaming media, then fundamental essentials VPN providers you may need to consider. These kind of services will cipher your current downloads, uploads, emails, messages, as well as manipulate your IP address to ensure that you may be effectively untraceable.IPSec can be built to handle only IP packets.