(Spring 2013) Signature Authentication Consistency Across Devices
•
0 recomendaciones•1,175 vistas
The purpose of this study is to determine the consistency of signatures and the reliability of verification across various devices. These devices include an iPad (with finger and stylus) and digitizers (back-lit and non-back-lit) for the purpose of electronic consent. This study was conducted using two to four (varied for each device and person) signatures per team member and then cross-comparing every combination of signature to determine the stability of using the algorithm across various devices with a given threshold.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
OPTIMIZED FINGERPRINT COMPRESSION WITHOUT LOSS OF DATAProposed workblessy up...

OPTIMIZED FINGERPRINT COMPRESSION WITHOUT LOSS OF DATAProposed workblessy up...feature software solutions pvt ltd
Más contenido relacionado
Similar a (Spring 2013) Signature Authentication Consistency Across Devices
OPTIMIZED FINGERPRINT COMPRESSION WITHOUT LOSS OF DATAProposed workblessy up...

OPTIMIZED FINGERPRINT COMPRESSION WITHOUT LOSS OF DATAProposed workblessy up...feature software solutions pvt ltd
Similar a (Spring 2013) Signature Authentication Consistency Across Devices (20)
Comparative Study of Machine Learning Algorithms for Sentiment Analysis with ...

Comparative Study of Machine Learning Algorithms for Sentiment Analysis with ...
Disparity Estimation by a Real Time Approximation Algorithm

Disparity Estimation by a Real Time Approximation Algorithm
Improving Analogy Software Effort Estimation using Fuzzy Feature Subset Selec...

Improving Analogy Software Effort Estimation using Fuzzy Feature Subset Selec...
A Novel Hybrid Voter Using Genetic Algorithm and Performance History

A Novel Hybrid Voter Using Genetic Algorithm and Performance History
Shape and Level Bottles Detection Using Local Standard Deviation and Hough Tr...

Shape and Level Bottles Detection Using Local Standard Deviation and Hough Tr...
COMPARATIVE ANALYSIS OF MINUTIAE BASED FINGERPRINT MATCHING ALGORITHMS

COMPARATIVE ANALYSIS OF MINUTIAE BASED FINGERPRINT MATCHING ALGORITHMS
Paper 58 disparity-of_stereo_images_by_self_adaptive_algorithm

Paper 58 disparity-of_stereo_images_by_self_adaptive_algorithm
PREDICTION BASED LOSSLESS COMPRESSION SCHEME FOR BAYER COLOUR FILTER ARRAY IM...

PREDICTION BASED LOSSLESS COMPRESSION SCHEME FOR BAYER COLOUR FILTER ARRAY IM...
OPTIMIZED FINGERPRINT COMPRESSION WITHOUT LOSS OF DATAProposed workblessy up...

OPTIMIZED FINGERPRINT COMPRESSION WITHOUT LOSS OF DATAProposed workblessy up...
Application of Genetic Algorithm in Software Testing

Application of Genetic Algorithm in Software Testing
Parameter Optimisation for Automated Feature Point Detection

Parameter Optimisation for Automated Feature Point Detection
PERFORMANCE EVALUATION OF FUZZY LOGIC AND BACK PROPAGATION NEURAL NETWORK FOR...

PERFORMANCE EVALUATION OF FUZZY LOGIC AND BACK PROPAGATION NEURAL NETWORK FOR...
Más de International Center for Biometric Research
An Investigation into Biometric Signature Capture Device Performance and User...

An Investigation into Biometric Signature Capture Device Performance and User...International Center for Biometric Research
Advances in testing and evaluation using Human-Biometric sensor interaction m...

Advances in testing and evaluation using Human-Biometric sensor interaction m...International Center for Biometric Research
(2010) Fingerprint recognition performance evaluation for mobile ID applications

(2010) Fingerprint recognition performance evaluation for mobile ID applicationsInternational Center for Biometric Research
Más de International Center for Biometric Research (20)
An Investigation into Biometric Signature Capture Device Performance and User...

An Investigation into Biometric Signature Capture Device Performance and User...
Best Practices in Reporting Time Duration in Biometrics

Best Practices in Reporting Time Duration in Biometrics
Advances in testing and evaluation using Human-Biometric sensor interaction m...

Advances in testing and evaluation using Human-Biometric sensor interaction m...
(2010) Fingerprint recognition performance evaluation for mobile ID applications

(2010) Fingerprint recognition performance evaluation for mobile ID applications
Último
Último (20)
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
TrustArc Webinar - How to Build Consumer Trust Through Data Privacy

TrustArc Webinar - How to Build Consumer Trust Through Data Privacy
The Ultimate Guide to Choosing WordPress Pros and Cons

The Ultimate Guide to Choosing WordPress Pros and Cons
Nell’iperspazio con Rocket: il Framework Web di Rust!

Nell’iperspazio con Rocket: il Framework Web di Rust!
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
Take control of your SAP testing with UiPath Test Suite

Take control of your SAP testing with UiPath Test Suite
How AI, OpenAI, and ChatGPT impact business and software.

How AI, OpenAI, and ChatGPT impact business and software.
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
Gen AI in Business - Global Trends Report 2024.pdf

Gen AI in Business - Global Trends Report 2024.pdf
Merck Moving Beyond Passwords: FIDO Paris Seminar.pptx

Merck Moving Beyond Passwords: FIDO Paris Seminar.pptx
New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
WordPress Websites for Engineers: Elevate Your Brand

WordPress Websites for Engineers: Elevate Your Brand
DevoxxFR 2024 Reproducible Builds with Apache Maven

DevoxxFR 2024 Reproducible Builds with Apache Maven
Leverage Zilliz Serverless - Up to 50X Saving for Your Vector Storage Cost

Leverage Zilliz Serverless - Up to 50X Saving for Your Vector Storage Cost
(Spring 2013) Signature Authentication Consistency Across Devices
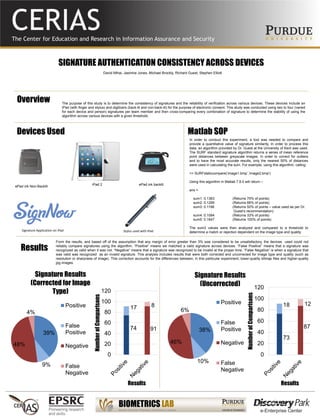
- 1. SIGNATURE AUTHENTICATION CONSISTENCY ACROSS DEVICES The purpose of this study is to determine the consistency of signatures and the reliability of verification across various devices. These devices include an iPad (with finger and stylus) and digitizers (back-lit and non-back-lit) for the purpose of electronic consent. This study was conducted using two to four (varied for each device and person) signatures per team member and then cross-comparing every combination of signature to determine the stability of using the algorithm across various devices with a given threshold. David Mihai, Jasmine Jones, Michael Brockly, Richard Guest, Stephen Elliott Overview Devices Used Matlab SOP Results 73 87 18 12 0 20 40 60 80 100 120 NumberofComparisons Results 38% 10% 46% 6% Signature Results (Uncorrected) Positive False Positive Negative False Negative 74 91 17 8 0 20 40 60 80 100 120 NumberofComparisons Results 39% 9% 48% 4% Signature Results (Corrected for Image Type) Positive False Positive Negative False Negative From the results, and based off of the assumption that any margin of error greater than 3% was considered to be unsatisfactory, the devices used could not reliably compare signatures using the algorithm. “Positive” means we matched a valid signature across devices. “False Positive” means that a signature was recognized as valid when it was not. “Negative” means that a signature was recognized to be invalid at the proper time. “False Negative” is when a signature that was valid was recognized as an invalid signature. This analysis includes results that were both corrected and uncorrected for image type and quality (such as resolution or sharpness of image). This correction accounts for the differences between, in this particular experiment, lower-quality bitmap files and higher-quality jpg images. In order to conduct this experiment, a tool was needed to compare and provide a quantitative value of signature similarity. In order to process this data, an algorithm provided by Dr. Guest at the University of Kent was used. The SURF standard signature algorithm returns a series of mean reference point distances between greyscale images. In order to correct for outliers and to have the most accurate results, only the nearest 50% of distances were used in calculating the sum. For example, using this algorithm, calling: >> SURFstaticcompare(‘image1.bmp’,’image2.bmp') Using this algorithm in Matlab 7.8.0 will return – ans = sum1: 0.1363 (Returns 75% of points) sum2: 0.1295 (Returns 66% of points) sum3: 0.1198 (Returns 50% of points – value used as per Dr. Guest’s recommendation) sum4: 0.1084 (Returns 33% of points) sum5: 0.1647 (Returns 100% of points) The sum3 values were then analyzed and compared to a threshold to determine a match or rejection dependent on the image type and quality. iPad 2 ePad ink backlit Signature Application on iPad Stylus used with iPad ePad ink Non-Backlit
