(Spring 2013) Biometric Perceptions for Campus Access Control
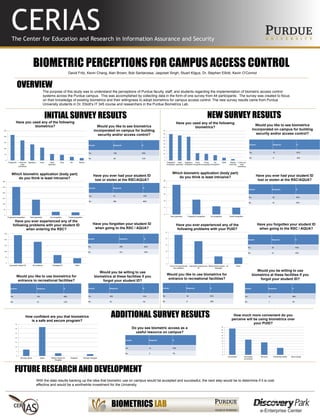
- 1. BIOMETRIC PERCEPTIONS FOR CAMPUS ACCESS CONTROL The purpose of this study was to understand the perceptions of Purdue faculty, staff, and students regarding the implementation of biometric access control systems across the Purdue campus. This was accomplished by collecting data in the form of one survey from 44 participants. The survey was created to focus on their knowledge of existing biometrics and their willingness to adopt biometrics for campus access control. The new survey results came from Purdue University students in Dr. Elliott’s IT 345 course and researchers in the Purdue Biometrics Lab. David Fritz, Kevin Chang, Alan Brown, Bob Santarossa, Jaspreet Singh, Stuart Kilgus, Dr. Stephen Elliott, Kevin O’Connor OVERVIEW INITIAL SURVEY RESULTS NEW SURVEY RESULTS FUTURE RESEARCH AND DEVELOPMENT Answer Response % Yes 400 95% No 20 5% Would you be willing to use biometrics at these facilities if you forgot your student ID? 0 50 100 150 200 250 Fingerprint I have not used biometrics Signature Voice Hand geometry Face Iris Retina Have you used any of the following biometrics? 0 50 100 150 200 250 Improperly swiped ID No problems Damaged ID Other Have you ever experienced any of the following problems with your student ID when entering the RSC? Answer Response % Yes 298 66% No 153 34% Have you forgotten your student ID when going to the RSC / AQUA? Answer Response % Yes 61 14% No 386 86% Have you ever had your student ID lost or stolen at the RSC/AQUA? Answer Response % Yes 396 89% No 48 11% Would you like to see biometrics incorporated on campus for building security and/or access control? Answer Response % Yes 393 88% No 52 12% Would you like to use biometrics for entrance to recreational facilities? 0 50 100 150 200 250 300 Fingerprint recognition Hand geometry Iris recognition Facial recognition Which biometric application (body part) do you think is least intrusive? 0 5 10 15 20 25 30 35 40 45 Fingerprint recognition Hand geometry Signature verification Voice recognition Facial recognition Iris recognition Other Retinal scanning I have not used biometrics Have you used any of the following biometrics? 0 5 10 15 20 25 I have not experienced any problems Improperly swiping your ID Being denied access - ID damaged Other Have you ever experienced any of the following problems with your PUID? 0 5 10 15 20 25 Hand geometry Fingerprint recognition Iris recognition Facial recognition Which biometric application (body part) do you think is least intrusive? 0 2 4 6 8 10 12 14 16 18 20 Convenient Somewhat convenient Not sure Somewhat harder Much harder How much more convenient do you perceive will be using biometrics over your PUID? Answer Response % Yes 35 81% No 8 19% Would you like to see biometrics incorporated on campus for building security and/or access control? 0 5 10 15 20 25 30 35 Strongly Agree Agree Neither Agree nor Disagree Disagree Strongly Disagree How confident are you that biometrics is a safe and secure program? With the data results backing up the idea that biometric use on campus would be accepted and successful, the next step would be to determine if it is cost effective and would be a worthwhile investment for the University. Answer Response % Yes 28 64% No 16 36% Have you ever had your student ID lost or stolen at the RSC/AQUA? Answer Response % Yes 28 64% No 16 36% Have you forgotten your student ID when going to the RSC / AQUA? ADDITIONAL SURVEY RESULTS Answer Response % Yes 36 82% No 8 18% Would you like to use biometrics for entrance to recreational facilities? Would you be willing to use biometrics at these facilities if you forgot your student ID? Answer Response % Yes 43 98% No 1 2% Answer Response % Yes 41 93% No 3 7% Do you see biometric access as a useful resource on campus?
