Sondaggio smart meter
•
0 recomendaciones•249 vistas
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Delve Labs - Upcoming Security Challenges for the Internet of Things

Delve Labs - Upcoming Security Challenges for the Internet of ThingsFrederic Roy-Gobeil, CPA, CGA, M.Tax.
We began to see renewed innovation in the threat actor space in mid to late 2018. This trend has continued to surface in 2019. Threat actors (black hat hackers) have increasingly leveraged prior attacks, data collection and mining, and likely AI to create a new type of highly targeted, very sophisticated cyber attacks. Explore this new threat technique, prevention and detection strategies, and some of the most effective strategies to balance compliance and customer requirements with practical cyber security. 2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...

2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...Internetwork Engineering (IE)
Presentation on the analysis of cybersecurity capacity building, finding a clear impact of capacity building on a reduction in end user problems and enhanced use by individuals, governments, and business.Presentation to GFCE 2019 in Addis Ababa, Ethiopia

Presentation to GFCE 2019 in Addis Ababa, EthiopiaOxford Martin Centre, OII, and Computer Science at the University of Oxford
Más contenido relacionado
La actualidad más candente
Delve Labs - Upcoming Security Challenges for the Internet of Things

Delve Labs - Upcoming Security Challenges for the Internet of ThingsFrederic Roy-Gobeil, CPA, CGA, M.Tax.
We began to see renewed innovation in the threat actor space in mid to late 2018. This trend has continued to surface in 2019. Threat actors (black hat hackers) have increasingly leveraged prior attacks, data collection and mining, and likely AI to create a new type of highly targeted, very sophisticated cyber attacks. Explore this new threat technique, prevention and detection strategies, and some of the most effective strategies to balance compliance and customer requirements with practical cyber security. 2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...

2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...Internetwork Engineering (IE)
Presentation on the analysis of cybersecurity capacity building, finding a clear impact of capacity building on a reduction in end user problems and enhanced use by individuals, governments, and business.Presentation to GFCE 2019 in Addis Ababa, Ethiopia

Presentation to GFCE 2019 in Addis Ababa, EthiopiaOxford Martin Centre, OII, and Computer Science at the University of Oxford
La actualidad más candente (20)
Cybersecurity for Control Systems: Current State and Future Vision pt.1

Cybersecurity for Control Systems: Current State and Future Vision pt.1
Delve Labs - Upcoming Security Challenges for the Internet of Things

Delve Labs - Upcoming Security Challenges for the Internet of Things
The top challenges to expect in network security in 2019 survey report 

The top challenges to expect in network security in 2019 survey report
2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...

2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...
Cyber Training: Developing the Next Generation of Cyber Analysts

Cyber Training: Developing the Next Generation of Cyber Analysts
Agile and Open C4ISR Systems - Helping the Military Integrate, Innovate and S...

Agile and Open C4ISR Systems - Helping the Military Integrate, Innovate and S...
Automated diagnosis of attacks in internet of things using machine learning a...

Automated diagnosis of attacks in internet of things using machine learning a...
PAS: Leveraging IT/OT - Convergence and Developing Effective OT Cybersecurity

PAS: Leveraging IT/OT - Convergence and Developing Effective OT Cybersecurity
Presentation to GFCE 2019 in Addis Ababa, Ethiopia

Presentation to GFCE 2019 in Addis Ababa, Ethiopia
Wireless Vulnerability Management: What It Means for Your Enterprise

Wireless Vulnerability Management: What It Means for Your Enterprise
Destacado (9)
La misurazione elettronica nell'attività di vendita: le opportunità offerte d...

La misurazione elettronica nell'attività di vendita: le opportunità offerte d...
Similar a Sondaggio smart meter
NIST's work underpins most of today's top science and technology challenges, such as cyber-security, biometrics, voting equipment standards, and nanotechnology, just to name an important few.
~ Sherwood Louis "Sherry" Boehler. Former Member of the U.S. House of Representatives from New York and Chairman of the House Science and Technology Committee
President Donald Trump - Cybersecurity - National Institute of Standards and ...

President Donald Trump - Cybersecurity - National Institute of Standards and ...Clifton M. Hasegawa & Associates, LLC
Become the best version of most in-demand cybersecurity experts with the best cybersecurity certifications to guide OT security frameworks. Foresee cybersecurity threats as a specialized OT security professional and gain big!
Read more: https://shorturl.at/jsuGSDeep Dive into Operational Technology Security - USCSI®.pdf

Deep Dive into Operational Technology Security - USCSI®.pdfUnited States Cybersecurity Institute (USCSI®)
Similar a Sondaggio smart meter (20)
Protecting Utilities from Risk - Iain Morton, Tyco Integrated Security

Protecting Utilities from Risk - Iain Morton, Tyco Integrated Security
Tigerspike - Cybersecurity and Mobility in the Energy Industry

Tigerspike - Cybersecurity and Mobility in the Energy Industry
Machine Learning -Based Security Authentication for Wireless Multimedia Network

Machine Learning -Based Security Authentication for Wireless Multimedia Network
Powering up the shocking truth about cyber security in the energy industry - ...

Powering up the shocking truth about cyber security in the energy industry - ...
SECURING FUTURE CONNECTIVITY: An Extensive Analysis on 5G Network Security

SECURING FUTURE CONNECTIVITY: An Extensive Analysis on 5G Network Security
President Donald Trump - Cybersecurity - National Institute of Standards and ...

President Donald Trump - Cybersecurity - National Institute of Standards and ...
IRJET- A Survey on Privacy Preserving Communication Protocol for IoT Applicat...

IRJET- A Survey on Privacy Preserving Communication Protocol for IoT Applicat...
Deep Dive into Operational Technology Security - USCSI®.pdf

Deep Dive into Operational Technology Security - USCSI®.pdf
Pat Pather- Cyber Security Unchartered: Vigilance, Innovation and Adaptability

Pat Pather- Cyber Security Unchartered: Vigilance, Innovation and Adaptability
Más de canaleenergia
Más de canaleenergia (20)
Pass M0S 420 kv per le sottostazioni della rete elettrica di Trasmissione

Pass M0S 420 kv per le sottostazioni della rete elettrica di Trasmissione
All compatible: la nuova tecnologia dei convertitori di frequenza

All compatible: la nuova tecnologia dei convertitori di frequenza
Ottimizzazione dei consumi di energia con interruttori di bassa tensione

Ottimizzazione dei consumi di energia con interruttori di bassa tensione
L'automazione motore dell'innovazione e della competitività

L'automazione motore dell'innovazione e della competitività
Último
Último (20)
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...

Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Apidays Singapore 2024 - Modernizing Securities Finance by Madhu Subbu

Apidays Singapore 2024 - Modernizing Securities Finance by Madhu Subbu
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
A Beginners Guide to Building a RAG App Using Open Source Milvus

A Beginners Guide to Building a RAG App Using Open Source Milvus
Navi Mumbai Call Girls 🥰 8617370543 Service Offer VIP Hot Model

Navi Mumbai Call Girls 🥰 8617370543 Service Offer VIP Hot Model
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Sondaggio smart meter
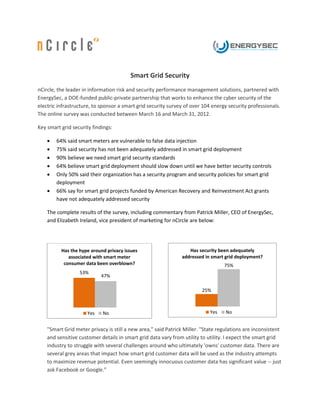
- 1. Smart Grid Security nCircle, the leader in information risk and security performance management solutions, partnered with EnergySec, a DOE-funded public-private partnership that works to enhance the cyber security of the electric infrastructure, to sponsor a smart grid security survey of over 104 energy security professionals. The online survey was conducted between March 16 and March 31, 2012. Key smart grid security findings: 64% said smart meters are vulnerable to false data injection 75% said security has not been adequately addressed in smart grid deployment 90% believe we need smart grid security standards 64% believe smart grid deployment should slow down until we have better security controls Only 50% said their organization has a security program and security policies for smart grid deployment 66% say for smart grid projects funded by American Recovery and Reinvestment Act grants have not adequately addressed security The complete results of the survey, including commentary from Patrick Miller, CEO of EnergySec, and Elizabeth Ireland, vice president of marketing for nCircle are below: Has the hype around privacy issues Has security been adequately associated with smart meter addressed in smart grid deployment? consumer data been overblown? 75% 53% 47% 25% Yes No Yes No "Smart Grid meter privacy is still a new area," said Patrick Miller. "State regulations are inconsistent and sensitive customer details in smart grid data vary from utility to utility. I expect the smart grid industry to struggle with several challenges around who ultimately 'owns' customer data. There are several grey areas that impact how smart grid customer data will be used as the industry attempts to maximize revenue potential. Even seemingly innocuous customer data has significant value -- just ask Facebook or Google.”
- 2. Patrick Miller noted, "Smart meters vary widely in Do smart meter installations have sufficient security controls to capability and many older meters were not designed to protect against false data injection? adequately protect against false data injection. It doesn't help that some communication protocols used by the 61% smart meter infrastructure don't offer much protection against false data injection either. Together, these facts 39% highlight a much larger potential problem with data integrity across the smart grid infrastructure. Because our nation relies on the smart grid to deliver robust and reliable power, we need to make sure that all systems that process usage data, especially those that make autonomous, self-correcting, self-healing decisions, assure Yes No data integrity." "A false data injection attack is another example of technology advancing faster than security controls,” said Elizabeth Ireland. “This is a problem that has been endemic in the evolution of security and it's a key reason for the significant cyber security risks we face across many facets of critical infrastructure. Installing technology without sufficient security controls presents serious risks to our power infrastructure and to every power user in the U.S." "Security has been addressed to varying degrees in many smart grid deployments, however it is going to be a Are smart grid security standards moving fast enough to keep pace challenge to keep pace with the constantly changing with smart grid deployment? security landscape," said Patrick Miller. "The analog and mechanical devices installed in most utilities were designed for a very different maintenance model than newer digital 72% equipment being designed and installed today." Elizabeth Ireland noted, "It's pretty clear that information security professionals in the energy industry are 28% uncomfortable with standards currently available for smart grid technology. Defining and implementing meaningful security standards is always a challenge but without standards, adoption of critical security controls across the Yes No smart grid industry is likely to be uneven at best."
- 3. Do you think we need smart grid Does your organization have a specific security standards and security program and security policies 89% policies? for smart grid deployment? 49% 51% 11% Yes No Yes No What part of smart grid infrastructure is most vulnerable to cyber attack? 41% 29% 20% 10% Smart meters Metering infrastructure including transport networks Utility energy management systems Energy management, such as phasor measurement units According to Patrick Miller, CEO of EnergySec, "The enormous range of technology in the smart grid presents many points of potential vulnerability, and we are moving at the speed of light to insert even more technology 'shims' into the existing network structures of the smart grid. This ever-increasing rate of complexity and hyper-embedded technology will be very difficult to secure." "The complexity of SCADA technology combined with the range of results from survey respondents on this issue indicates that we don't have any single section of the smart grid fully secured," said Elizabeth Ireland, vice president of marketing for nCircle. "It's not surprising that energy industry security professionals deem metering infrastructure as the highest area of risk. Individual partners in any complex supply chain often have very limited visibility into the security for the entire process."
- 4. How should the security risks associated with the smart grid affect deployment plans? 64% 33% 4% No change from current plans; full steam ahead Deployment should slow down until we have better security controls We don’t need a smart grid at all Should regulatory oversight for smart Have the American Recovery and grid distribution be transitioned to Reinvestment Act of 2009 grants the Federal government? awarded to smart grid projects adequately addressed security? 60% 66% 40% 34% Yes No Yes No "The modernized grid encompasses new digital components all the way from the toaster to the turbine,” noted Patrick Miller. “It spans local, state and federal regulatory lines. In an environment where innovation is paramount, a federal one-size-fits-all approach may significantly slow down progress. On the other hand, potential inconsistencies in regulatory approaches may introduce complexity and risk smart grid landscape. Either model, whether state or federally regulated, comes with pros and cons. I see the regulatory oversight of the smart grid as one of our biggest smart grid challenges with the least obvious solution." “It’s likely that the division of opinion on regulatory oversight reflects, at least to some degree, fundamental political beliefs” said Elizabeth Ireland. “Some security professionals probably see government regulation in industry as beneficial, and some feel we should minimize the role of government in industry as much as possible. The majority of energy security professionals surveyed believe the energy industry will police itself.”
