Introduction to Unix-like systems (Part I-IV)
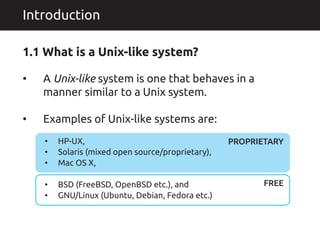
- 1. A Unix-like system is one that behaves in a manner similar to a Unix system. Examples of Unix-like systems are: � � Introduction 1.1 What is a Unix-like system? HP-UX, Solaris (mixed open source/proprietary), Mac OS X, BSD (FreeBSD, OpenBSD etc.), and GNU/Linux (Ubuntu, Debian, Fedora etc.) � � � � � PROPRIETARY FREE
- 2. Introduction The Open Group, an industry standards consortium, owns the UNIX trademark. Dennis Ritchie, one of the original creators of Unix, expressed his opinion that Unix-like systems such as Linux are de facto Unix systems. � � 1.1 What is a Unix-like system? (cont’d)
- 3. Unix filesystem and shell (I) 2.1 Unix system structure A computer system consists of hardware and systems software (OS) that together provide a working environment for running general purpose application programs. Hardware Kernel Shell & utilities User space
- 4. Different UNIX variants have different implementations of different subsystems. Unix filesystem and shell (I) 2.2 Kernel subsystems Process management Memory management Filesystem Network stack (TCP/IP)
- 5. � � � A process is a running instance of a program. At any given point in time, the CPU is operating within the execution context of a specific process. The process manager is responsible for process scheduling, context-switching, inter-process communication etc. Process management Unix filesystem and shell (I) 2.2 Kernel subsystems (cont’d)
- 6. � � Memory manager Unix filesystem and shell (I) 2.2 Kernel subsystems (cont’d) Responsible for controlling process access to the hardware memory resources. Memory virtualization separates logical memory from physical memory. Provides each process with a uniform address space. Protects the address space of each process from corruption by other processes. � �
- 7. � � � Manages access to data and metadata of the files, and organizes the available space of the device(s) which contain it. A Unix file is an information container structured as a sequence of bytes. Most Unix-like systems support several filesystems. Filesystem Unix filesystem and shell (I) 2.2 Kernel subsystems (cont’d)
- 8. Network stack (TCP/IP) Unix filesystem and shell (I) 2.2 Kernel subsystems (cont’d) Unix-like operating systems are known for rich Ethernet networking support. Unix implements the TCP/IP protocol stack. The Berkeley sockets API provides a high level interface to the TCP/IP stack. � � �
- 9. Unix filesystem and shell (I) 2.3 The shell A command line interface to the operating system. Used to execute other programs, manage files and processes. Users typically interact with a Unix shell using a terminal emulator, e.g., xterm or OS X Terminal. Graphical user interfaces for Unix are sometimes referred to as graphical shells. � � � �
- 10. Unix filesystem and shell (I) 2.4 Simple command examples pwd ls adduser top mkdir ps who df cd Print name of current/working directory List directory contents Add a user to the system Display processes Make directories Report a snapshot of the current processes Show who is logged on Report file system disk space usage Change directory
- 11. Unix filesystem and shell (I) 2.5 Shell scripting A shell script is a regular text file that conatains shell or Unix commands. Useful for automating tasks and storing command sequences for later execution. Makes life easier for the user. Some shell scripts run at system startup or shutdown. The /etc/init.d directory contains shell scripts used to start, stop, or restart system daemons. � � � �
- 12. Unix filesystem and shell (I) 2.6 Options and parameters $ ls -l /bin Parameters are pieces of information (e.g., a file name) that the command needs in order to do its job. Flags (or options) are typically composed using a hyphen (-) followed by one or more letters. A flag instructs the shell to perform the command in a particular way.
- 13. man: whatis: Display entries from Unix online documentation. example: man mkdir Displays a single line information about a command. Unix filesystem and shell (I) 2.7 Getting help $ whatis ifconfig ifconfig (8) - configure a network interface
- 14. Unix filesystem and shell (I) 2.7 Getting help (cont’d) $ man mkdir MKDIR(1) USER COMMANDS MKDIR(1) NAME mkdir - make a directory SYNOPSIS mkdir [ -p ] dirname... DESCRIPTION mkdir creates directories. Standard entries,`.',for the directory itself, and `..' for its parent, are made automat- ically. The -p flag allows missing parent directories to be created as needed. With the exception of the set-gid bit, the current umask(2V) setting determines the mode in which directories are created. The new directory inherits the set-gid bit of the parent directory. Modes may be modified after creation by using chmod(1V). mkdir requires write permission in the parent directory. SEE ALSO chmod(1V), rm(1), mkdir(2v), umask(2V)
- 15. Each user owns some quota of the total disk space for storage of personal files, mail etc. This portion of the filesystem is visible only to its owner. Users are identified by a unique number, called user id. � � Unix filesystem and shell (II) 3.1 Security fundamentals A multi-user system is one that allows concurrent access by multiple users of a computer.
- 16. Unix filesystem and shell (II) 3.1 Security fundamentals (cont’d) � � � A set of users can form a group. Each user is a member of one or more groups. Groups enable users to share material with other users. Like users, every group has a unique identifier, called group id. Groups
- 17. Unix filesystem and shell (II) 3.1 Security fundamentals (cont’d) � � Any Unix-like operating system has a special user called root (or sometimes superuser). The root user can access every file on the system and interfere with the activity of running user programs. The root user
- 18. Can a given file be read or written to by a particular user? What users can run a specific program? Can a user terminate a running process? � � Unix filesystem and shell (II) 3.1 Security fundamentals (cont’d) Users and groups are used to determine if file or process operations can be performed.
- 19. Unix filesystem and shell (II) 3.2 Unix file hierarchy Files and directories are organized in a hierarchical tree structure. In Unix, all files and directories appear under the root directory "/". / (root) /bin /home /usr /home /bin /lib /ls /local /lc
- 20. Unix filesystem and shell (II) 3.3 Working directory Every running process has a current working directory. A nickname for the current working directory of a process is “.” (a single period). The pwd (present working directory) command displays your current working directory. � � �
- 21. Unix filesystem and shell (II) 3.4 File path (relative vs. absolute paths) To identify a specific file, the operating system uses a pathname, which consists of slashes alternating with a sequence of directory names that lead to the file. If the first item in the pathname is a slash, the pathname is said to be absolute. Its starting point is the root directory. If the first item is a directory name or filename, the path is said to be relative. Its starting point is the current directory. � � �
- 22. Unix filesystem and shell (II) 3.5 The file abstraction Unix follows the mantra: “everything is a file.” As mentioned earlier, a Unix file is simply a sequence of bytes. Unix files may have one of the following types: Regular file Directory Symbolic link Block-oriented device file Character-oriented device file Pipe and named pipe (also called FIFO) Socket � � � � � � �
- 23. Unix filesystem and shell (II) 3.6 Directories A directory is a list of files with associated information. Every user has a home directory. (/home/<username>) � � Creation date Attributes etc. � � �
- 24. Unix filesystem and shell (II) 3.7 Tilde expansion Most shells support the ~ operator (called tilde). ~ expands to my home directory ~user expands to user’s home directory Useful since home directory locations vary between different machines. � � � � ~/file /home/<username>/file ~alice/file2 /home/alice/file2
- 25. Unix filesystem and shell (II) cat 3.8 The cat, more and less commands Copies the contents of a file to the terminal. When invoked with a list of file names, it concatenates them. Use the -n flag to show line numbers. more/less more shows file contents, one page at a time. less allows both forward and backward navigation. Programs of this sort are called pagers.
- 26. Unix filesystem and shell (II) 3.9 Common utilities pwd ls adduser top mkdir rmdir ps who df cd vi nano rm mv cp touch wc file mount umount date echo tar passwd kill nice &
- 27. Unix filesystem and shell (III) 4.1 File permissions Unix file permissions 01 02 04 01 02 04 01 02 04 suid sgid sticky read write execute user group others
- 28. Example: Unix filesystem and shell (III) 4.1 File permissions (cont’d) read write execute user group others 01 0404 0101 02 04 557 A common method for representing Unix permissions is using octal (base-8) notation. With three-digit octal notation, each numeral represents a different component of the permission set: user, group, and others respectively.
- 29. Unix filesystem and shell (III) 4.2 Directory permissions Similar to ordinary file permissions. Read means that the process may read directory contents. Write means that the process can add/remove files. Execute permission on a directory means you can cd to that directory and access its files. � � � �
- 30. Unix filesystem and shell (III) 4.3 Reading ls output -rwxr--r-- 1 root root 4096 Sep 10 21:11 foo Permissions for User (Owner) of file Directory flag; 'd' if a directory, '-' if a normal file etc. Permissions for Group Permissions for Other owner group filenamelink count file size The ls command shows the permissions and group associated with files when used with the -l option:
- 31. Unix filesystem and shell (III) 4.4 Manipulating file attributes chown � Used to change file owner. chgrp � Used to change file group. chmod � Used to change file permissions.
- 32. Unix filesystem and shell (III) 4.4 Manipulating file attributes (cont’d) Symbolic access modes � chmod u, g, o +/- r, w, x $ ls -la -rw-r--r-- 1 root root 0 foo $ chmod +x foo -rwxr-xr-x 1 root root 0 foo $ chmod g-x foo -rwxr--r-x 1 root root 0 foo
- 33. Unix filesystem and shell (III) 4.5 File system internals Process table � � The process table is a data structure in the computer’s main memory that holds information about the processes currently handled by the operating system. Each entry in the process table contains a table of open file descriptors for that process.
- 34. Unix filesystem and shell (III) 4.5 File system internals (cont’d) Open file table � � The open-file table contains an entry for each open file for every process. File descriptors are unique to a process – a file that has been opened by several processes may be assigned different descriptors for each process.
- 35. Unix filesystem and shell (III) 4.5 File system internals (cont’d) pid #10 fd #0 fd #1 fd #2 fd #3 fd #4 status offset etc. pid #11 pid #12 status offset etc. status offset etc. Processtable fd #0 fd #1 fd #2 fd #3 fd #4 fd #5 fd #6 fd #0 fd #1 fd #2 fd #3 fd #4 memory disk or other device Open-file table Actual file entries in v-node table File File
- 36. Unix filesystem and shell (III) 4.6 Commands for file/process information Shows a report of all open files and the processes that opened them. Selects the listing of files for the processes whose ID numbers are in the comma-separated set s. List information about every process now running. lsof lsof -p s ps -e
- 37. Unix filesystem and shell (IV) 5.1 The standard in/out/err Entry 0: Standard input is data (often text) going into a program. Entry 1: Standard output is the stream where a program writes its output. Entry 2: Standard error is typically used by programs to output error messages or diagnostics. The first three entries in the file descriptor table are preset: � � �
- 38. Unix filesystem and shell (IV) 5.2 Devices In Unix, devices are treated just like ordinary files. Entries in the /dev file system are device driver interfaces. Applications interact with the device using standard I/O system calls. /dev/tty represents the terminal for the current process. Some special devices, called pseudo-devices do not correspond to physical devices (e.g. /dev/null). � � � �
- 39. Unix filesystem and shell (IV) 5.3 Redirection Before a command is executed, the input and output can be changed (redirected) from the terminal to a file: Append output: $ ls > file $ date >> file $ cat < file Redirect standard out Redirect standard in
- 40. Unix filesystem and shell (IV) 5.4 Mounting file systems When the system starts, the directory tree corresponds to the file system located on a single disk called the root device. File systems created on other devices are attached to the original directory hierarchy using the mount mechanism. The commands mount and umount are used to mount and unmount devices. � � �
- 41. Unix filesystem and shell (IV) 5.4 Mounting file systems (cont’d) / a b / / a a b b a b / /a/b Device Mount point root device external device
- 42. Unix filesystem and shell (IV) 5.5 Links A directory is a list of files and directories. Each directory entry links to a file on the disk. Two different directory entries can link to the same actual file. Moving a file (changing its location) does not actually move any data around. � � � � Creates a link in new location. Deletes link in old location. � � In same directory or across different directories.�
- 43. 5.5 Links (cont’d) The ln command is used to create a regular link, often called hard link. Symbolic links (soft links) are created using ln -s. The main differences are that: � � � Hard links don’t work across file system boundaries. Hard links only work for regular files, not directories. � � $ ln filename linkname Unix filesystem and shell (IV)
- 44. Unix filesystem and shell (IV) 5.5 Links (cont’d) Hard vs. symbolic links directory entry file contents directory entry directory entry hard linkhard link symbolic link file contents
- 45. The Unix find command is used to locate files. This will search the whole system for any files named foo and display their pathnames. � $ find / -name foo You can specify as many places to search as you wish. $ find /tmp /var/tmp . -name foo Unix filesystem and shell (IV) 5.6 Find utility syntax: find where-to-look what-to-do
- 46. Prints an entry for a directory called './src/misc' (if one exists). find . -path './sr*sc' -path pattern� Find every file under the directory /home owned by the user joe. find /home -user joe -user name� Unix filesystem and shell (IV) 5.6 Find utility (cont’d)
- 47. Search for files which permissions matches the provided expression. find . -perm 664 -perm p� Same as previous except that this will ignore presence of any extra permission bits. This will match a file which has mode 0777, for example. find . -perm -664 Unix filesystem and shell (IV) 5.6 Find utility (cont’d)
- 48. find . -mtime 0 # find files modified between now and 1 day ago # (i.e., within the past 24 hours) find . -mtime -1 # find files modified less than 1 day ago # (i.e., within the past 24 hours, as before) find . -mtime 1 # find files modified between 24 and 48 hours ago find . -mtime +1 # find files modified more than 48 hours ago find . -mmin +5 -mmin -10 # find files modified between # 6 and 9 minutes ago -mmin n -mtime n� Unix filesystem and shell (IV) 5.6 Find utility (cont’d)