IBM X-Force Exchange Infographic
•
1 recomendación•1,671 vistas
IBM® X-Force® Exchange is a cloud-based, collaborative threat intelligence platform that helps you research the latest global security threats, aggregate actionable intelligence, and collaborate with peers to quickly identify external threats and act on them. To learn more and register for a free 30-day trial of the IBM X-Force Exchange Commercial API, visit http://ibm.co/2elY30M.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
Destacado
Destacado (9)
Pulse 2013 - Mobile strategy and user centered design, an IBM interactive primer

Pulse 2013 - Mobile strategy and user centered design, an IBM interactive primer
Nowhere to Hide: Expose Threats in Real-time with IBM QRadar Network Insights

Nowhere to Hide: Expose Threats in Real-time with IBM QRadar Network Insights
Safeguard Healthcare Identities and Data with Identity Governance and Intelli...

Safeguard Healthcare Identities and Data with Identity Governance and Intelli...
DSS @CERT.LV_ISACA_2013_Conference - IBM X Force Report 2013

DSS @CERT.LV_ISACA_2013_Conference - IBM X Force Report 2013
IBM X-Force: Insights from the 1Q 2015 X-Force Threat Intelligence Quarterly

IBM X-Force: Insights from the 1Q 2015 X-Force Threat Intelligence Quarterly
Attack Autopsy: A Study of the Dynamic Attack Chain

Attack Autopsy: A Study of the Dynamic Attack Chain
IBM X-Force Threat Intelligence: Why Insider Threats Challenge Critical Busin...

IBM X-Force Threat Intelligence: Why Insider Threats Challenge Critical Busin...
Hunting The Shadows: In Depth Analysis of Escalated APT Attacks

Hunting The Shadows: In Depth Analysis of Escalated APT Attacks
Más de IBM Security
Más de IBM Security (20)
Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...

Leaders & Laggards: The Latest Findings from the Ponemon Institute’s Study on...
Bridging the Gap between Privacy and Security: Using Technology to Manage Com...

Bridging the Gap between Privacy and Security: Using Technology to Manage Com...
The Resilient End-of-Year Review: The Top Cyber Security Trends in 2018 and P...

The Resilient End-of-Year Review: The Top Cyber Security Trends in 2018 and P...
Leveraging Validated and Community Apps to Build a Versatile and Orchestrated...

Leveraging Validated and Community Apps to Build a Versatile and Orchestrated...
Accelerating SOC Transformation with IBM Resilient and Carbon Black

Accelerating SOC Transformation with IBM Resilient and Carbon Black
How to Build a Faster, Laser-Sharp SOC with Intelligent Orchestration

How to Build a Faster, Laser-Sharp SOC with Intelligent Orchestration
Orchestrate Your Security Defenses to Optimize the Impact of Threat Intelligence

Orchestrate Your Security Defenses to Optimize the Impact of Threat Intelligence
Your Mainframe Environment is a Treasure Trove: Is Your Sensitive Data Protec...

Your Mainframe Environment is a Treasure Trove: Is Your Sensitive Data Protec...
Meet the New IBM i2 QRadar Offense Investigator App and Start Threat Hunting ...

Meet the New IBM i2 QRadar Offense Investigator App and Start Threat Hunting ...
Understanding the Impact of Today's Security Breaches: The 2017 Ponemon Cost ...

Understanding the Impact of Today's Security Breaches: The 2017 Ponemon Cost ...
How to Improve Threat Detection & Simplify Security Operations

How to Improve Threat Detection & Simplify Security Operations
See How You Measure Up With MaaS360 Mobile Metrics

See How You Measure Up With MaaS360 Mobile Metrics
Último
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Último (20)
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
A Beginners Guide to Building a RAG App Using Open Source Milvus

A Beginners Guide to Building a RAG App Using Open Source Milvus
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
IBM X-Force Exchange Infographic
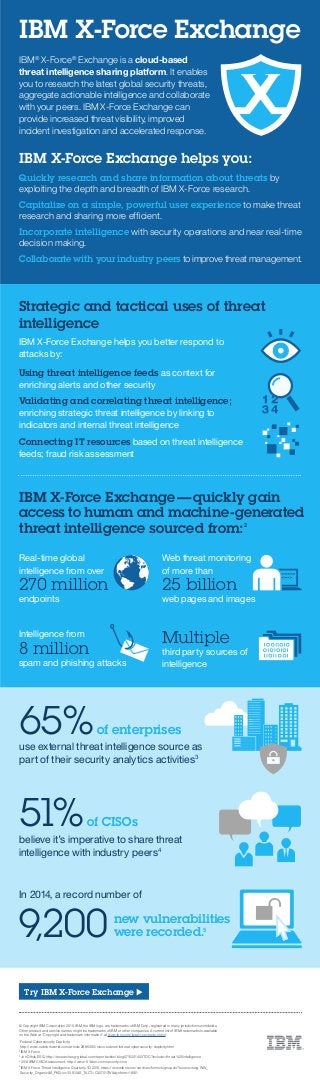
- 1. Real-time global intelligence from over 270 million endpoints IBM X-Force Exchange 65%use external threat intelligence source as part of their security analytics activities3 51%believe it’s imperative to share threat intelligence with industry peers4 of CISOs of enterprises 9,200 In 2014, a record number of new vulnerabilities were recorded.5 IBM® X-Force® Exchange is a cloud-based threat intelligence sharing platform. It enables you to research the latest global security threats, aggregate actionable intelligence and collaborate with your peers. IBM X-Force Exchange can provide increased threat visibility, improved incident investigation and accelerated response. IBM X-Force Exchange helps you: Quickly research and share information about threats by exploiting the depth and breadth of IBM X-Force research. Capitalize on a simple, powerful user experience to make threat research and sharing more efficient. Incorporate intelligence with security operations and near real-time decision making. Collaborate with your industry peers to improve threat management. IBM X-Force Exchange — quickly gain access to human and machine-generated threat intelligence sourced from:2 © Copyright IBM Corporation 2015. IBM, the IBM logo, are trademarks of IBM Corp., registered in many jurisdictions worldwide. Other product and service names might be trademarks of IBM or other companies. A current list of IBM trademarks is available on the Web at “Copyright and trademark information” at www.ibm.com/legal/copytrade.shtml. 1 Federal Cybersecurity Duplicity: http://www.networkworld.com/article/2886360/cisco-subnet/federal-cybersecurity-duplicity.html 2 IBM X-Force 3 Jon Oltsik,ESG, http://research.esg-global.com/reportaction/blog0715201401/TOC?include=threat%20intelligence 4 2014 IBM CISO Assessment, http://www-03.ibm.com/security/ciso 5 IBM X-Force Threat Intelligence Quarterly, 1Q 2015, https://www.ibm.com/services/forms/signup.do?source=swg-WW_ Security_OrganicS_PKG=ov33510S_TACT=C327017Wdynform=18101 Try IBM X-Force Exchange Multiple third party sources of intelligence Web threat monitoring of more than 25 billion web pages and images Intelligence from 8 million spam and phishing attacks Strategic and tactical uses of threat intelligence IBM X-Force Exchange helps you better respond to attacks by: Using threat intelligence feeds as context for enriching alerts and other security Validating and correlating threat intelligence; enriching strategic threat intelligence by linking to indicators and internal threat intelligence Connecting IT resources based on threat intelligence feeds; fraud risk assessment
