Más contenido relacionado
La actualidad más candente (20)
Ajs 4 a
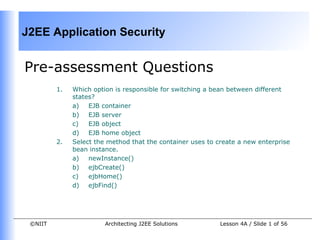
- 1. J2EE Application Security
Pre-assessment Questions
1. Which option is responsible for switching a bean between different
states?
a) EJB container
b) EJB server
c) EJB object
d) EJB home object
2. Select the method that the container uses to create a new enterprise
bean instance.
a) newInstance()
b) ejbCreate()
c) ejbHome()
d) ejbFind()
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 1 of 56
- 2. J2EE Application Security
Pre-assessment Questions
1. Which method of a BMP entity bean allows passing reference of an EJB
object to other entity beans?
a) ejbCreate()
b) ejbPostCreate()
c) ejbLoad()
d) ejbStore()
2. Which transaction attribute enables an EJB container to start a new
transaction before running the method of a bean when the client of the
bean is not associated with a transaction?
a) Supports
b) Mandatory
c) Never
d) Required
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 2 of 56
- 3. J2EE Application Security
Pre-assessment Questions
• Which method is invoked whenever a message arrives from the client in
the message-driven bean lifecycle?
a) setMessageDrivenContext()
b) newInstance()
c) onMessage()
d) ejbCreate()
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 3 of 56
- 4. J2EE Application Security
Solutions to Pre-assessment Questions:
1. a) EJB container
2. a) newInstance()
3. b) ejbPostCreate()
4. d) Required
5. c) onMessage()
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 4 of 56
- 5. J2EE Application Security
Objectives
In this lesson, you will learn to:
• Identify various security threats to enterprise applications
• Identify the various security techniques in Java 2 Security Model
• Authenticate users while accessing J2EE application
• Implement security using Java Cryptography Extensions (JCE)
• Authorize applications in J2EE, declaratively and programmatically
• Implement firewalls
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 5 of 56
- 6. J2EE Application Security
Security Threat Assessment
• Threat assessment involves identifying the potential sources of security threats
to application data and their consequences in application's performance.
• Enterprise applications remain vulnerable to security attacks without proper
threat assessment.
• Threat analysis is a part of the risk assessment process undertaken by J2EE
architects to determine the vulnerability of an application and the value of
information that will be lost because of breach in security.
• To assess security threats, J2EE architects should:
• Identify and assess security threats during the designing phase of an
application
• Identify the sources of security threats, frequency of security threats, and
their impacts on the enterprise applications.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 6 of 56
- 7. J2EE Application Security
Security Threat Assessment (Contd.)
• Role of Architects in Risk Assessment
• Threat analysis is part of the risk assessment process undertaken by J2EE
architects to design secure enterprise applications.
• Threat analysis involves identifying the potential sources of threats.
• The risk assessment task undertaken by the architects must cover an
analysis of the threats, vulnerabilities in application design, and the threat
consequences to application data and resources.
• Prioritization of Security Initiatives
• Detailed threat analysis helps architects to prioritize security
initiatives and plan corrective measures to address the
vulnerabilities.
• Determining the frequency of the threats and their impact on the
overall system help architects to undertake preventive measures for
the areas in the applications, which are most likely to be attacked.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 7 of 56
- 8. J2EE Application Security
Security Threat Assessment (Contd.)
• Problems in Threat Analysis are:
• Undervalued benefits
• The main reason for J2EE architects to ignore or pay less
importance to the application's threat analysis process is that its
benefits are not always apparent to the management.
• Results of the analysis must be practically implemented to
highlight the advantages of performing threat analysis.
• There should be regulatory measurements that must make it
mandatory for J2EE architects to perform threat analysis while
designing J2EE applications.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 8 of 56
- 9. J2EE Application Security
Security Threat Assessment (Contd.)
• Problems in Threat Analysis are (Contd.):
• Measurement challenges
• The difficulty of precisely measuring the benefits of threat
analysis in monetary terms often leads to its under appreciation.
• Management is more focused on the activities of the architects
from the monetary viewpoint.
• As the threat analysis process cannot determine the amount of
money that can be saved, this process gets ignored.
• Focus on vulnerabilities
• Vulnerabilities of the enterprise applications are often
determined in more precise and measurable terms than the
threat analysis results.
• Architects designing secure applications need to use the results
of the threat analysis and vulnerabilities determination together
to design effective security measures.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 9 of 56
- 10. J2EE Application Security
Security Threat Assessment (Contd.)
• Major Activities in Threat Analysis
• Major activities to be performed by J2EE architects in threat analysis
include:
• Threat identification:
• Identifies the sources, which can cause harm to the
resources of the applications and data.
• Measurement:
• Measures the probabilities of security threats and their
impact on the application's resources and data.
• Threat probabilities and impacts can be measured either
qualitatively or quantitatively.
• Determine strategy:
• Determines an effective strategy to counter security
threats to the applications depending upon the
probabilities of their occurrence.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 10 of 56
- 11. J2EE Application Security
Java 2 Security Model
• Java 2 security model provides an amendment of the access controls over
prior security models.
• The Java 2 security model enables an end user to download, install, and run
the applications from the Internet by granting the access permissions for the
required actions.
• Common Security Concepts
• Security is the major factor to determine how only authorized end users
can access the resources of a network, and prevent malicious end users
from accessing the same.
• You provide security to a network environment by implementing various
security techniques, such as cryptography, digital signatures, digital
certificates, and Secure Socket Layer (SSL).
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 11 of 56
- 12. J2EE Application Security
Java 2 Security Model (Contd.)
• Common Security Concepts (Contd.)
• Cryptography
• Cryptography is the mechanism of sending and receiving messages
over a network in a secure format.
• Data is send from the sender to the receiver and vice-versa in an
encrypted format.
• Key is a fundamental element in cryptography, which is used in
combination with an algorithm to determine how the message is
encrypted.
• An algorithm defines a process and its range of possible outcomes,
but the key determines which of this probability is the actual result
for a particular occurrence.
• Cryptography can be categorized into:
• Symmetric cryptography
• Asymmetric cryptography
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 12 of 56
- 13. J2EE Application Security
Java 2 Security Model (Contd.)
• Common Security Concepts (Contd.)
• Symmetric Cryptography
• Symmetric cryptography is also known as conventional, single-key,
or secret key cryptography.
• Symmetric cryptography uses the same key for both the
encryption and decryption of data.
• The key in secret key cryptography is termed as the secret key.
• The following figure shows the working of symmetric cryptography
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 13 of 56
- 14. J2EE Application Security
Java 2 Security Model (Contd.)
• Common Security Concepts (Contd.)
• Asymmetric Cryptography
• Asymmetric cryptography is a technique that uses the
public/private key pairs for the encryption and decryption of
messages.
• Asymmetric cryptography is used when you do not want to restrict
the data.
• Any end user can encrypt the data using the public key, which is
provided using a digital certificate.
• However, an end user containing the private key can only decrypt
the data.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 14 of 56
- 15. J2EE Application Security
Java 2 Security Model (Contd.)
• Common Security Concepts (Contd.)
• Asymmetric Cryptography
• The following figure shows the working of asymmetric
cryptography:
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 15 of 56
- 16. J2EE Application Security
Java 2 Security Model (Contd.)
• Common Security Concepts (Contd.)
• Digital Signatures
• Digital signature is an encrypted text to authenticate the sender of
a message or a document.
• Digital signature is created using the asymmetric encryption
technique.
• Digital Signature Algorithm (DSA) is an algorithm to generate
digital signatures.
• Digital Certificates
• Digital certificate is a signed statement, which contains
information, such as the name of its holder, a serial number, and a
public key.
• In asymmetric cryptography, public key is distributed to anyone
who requests for it, by means of a digital certificate, but the
private key is kept secure.
• You can obtain digital certificates from a Certificate Authority (CA).
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 16 of 56
- 17. J2EE Application Security
Java 2 Security Model (Contd.)
• Common Security Concepts (Contd.)
• Secure Socket Layer
• Secure Socket Layer (SSL) is a protocol developed by Netscape to
perform reliable, end-to-end, and secure transactions over the
Internet.
• The upper layers consist of the SSL Handshake Protocol, the SSL
Change Cipher Spec Protocol, and the SSL Alert Protocol.
• The lower layer has the SSL Record Protocol.
• The three upper layer protocols manage the SSL exchanges.
• The SSL Record Protocol provides security services to the upper
layer protocols.
• In SSL server authentication, a client confirms a server’s identity
using SSL-enabled client software, which uses the public-key
cryptography techniques.
• An encrypted SSL connection between a client and a server
provides confidentiality to the transmitted data.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 17 of 56
- 18. J2EE Application Security
Java 2 Security Model (Contd.)
• Security Restriction on Applets
• Security can be violated while transmitting data over a network.
• Java includes applet programs that are downloaded from a network and
run within a Java-enabled Web browser.
• An applet that is developed and stored in the same system is called
local applet.
• An applet, which is developed in one computer system and stored in a
remote computer over the Internet, is called remote applet.
• The architectural design of a Java applet is based on the sandbox model
designed in Java 1.0 version.
• The sandbox model of Java ensures the security of Java code when an
applet runs.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 18 of 56
- 19. J2EE Application Security
Java 2 Security Model (Contd.)
• Security Restriction on Applets (Contd.)
• Reading, Writing, or Deleting Files
• The various operations that an untrusted applet cannot perform
are:
• Reading, writing, renaming, and deleting files on the client file
system.
• Creating a directory and listing the contents of the directory.
• Retrieving information about a file, such as type and size.
• Accepting network connections on any port of the client
computer.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 19 of 56
- 20. J2EE Application Security
Java 2 Security Model (Contd.)
• Security Restriction on Applets (Contd.)
• Accessing System Properties
• A client is allowed to read the properties that are loaded in an
appletviewer by setting the required property to true in the
~/.hotjava/properties file, which is located in the home directory.
• Applets are not allowed to access certain system properties of a
client, such as java.home, java.class.path, user.name,
user.home, and user.dir.
• You cannot hide the system properties of an applet that are loaded
in a Java-enabled browser.
• However, you can hide the system properties of an applet in an
appletviewer by redefining the ~/.hotjava/properties file.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 20 of 56
- 21. J2EE Application Security
Java 2 Security Model (Contd.)
• Security Restriction on Applets (Contd.)
• Opening a Socket Connection
• Applets are allowed to open a socket only with the originating host
from which the applets have been downloaded.
• The originating host can be the host from where the HTML page is
loaded or the host specified in the codebase parameter of the
applet tag.
• An applet throws a security exception if you try to open a socket
from a host other than the originating host.
• An applet is restricted from creating or accessing threads or thread
groups outside of the thread group in which it is running.
• Therefore, applets are restricted from modifying any thread
attributes too.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 21 of 56
- 22. J2EE Application Security
Java Security APIs
• Java provides a set of Application Programming Interface (API) for providing
security while transmitting data over a network.
• Java Cryptography Extensions
• Java Cryptography Extensions (JCE) provides implementation for
encrypting data, generating a key, and generating Message
Authentication Code (MAC) algorithms.
• Various components of the JCE API are:
• Password-based encryption (PBE) techniques
• Key agreement
• Symmetric bulk encryption algorithms, such as DES, IDEA, and
RES
• Symmetric stream encryption algorithms, such as RC4
• Asymmetric encryption algorithms, such as RSA
• MAC algorithms
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 22 of 56
- 23. J2EE Application Security
Java Security APIs (Contd.)
• Java Cryptography Extensions (Contd.)
• JCE API
• JCE API provides the support for cryptography using various
javax.crypto package classes and interfaces such as Cipher,
CipherInputStream, CipherOutputStream, KeyAgreement,
KeyGenerator, Mac, SecretKey, SecretKeyFactory, and
SealedObject.
• Cipher class
• Imparts the functionality for encrypting and decrypting of
data.
• After creating the Cipher instance by using the getinstance()
method of cipher class, you can initialize a Cipher object in
any of the modes, ENCRYPT_MODE, DECRYPT_MODE,
WRAP_MODE, and UNWRAP_MODE.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 23 of 56
- 24. J2EE Application Security
Java Security APIs (Contd.)
• Java Cryptography Extensions (Contd.)
• JCE API (Contd.)
• CipherInputStream Class
• The CipherInputStream class represents a secure input
stream used for encrypting and decrypting data.
• It is a FilterInputStream class, which consists of an
InputStream, its subclasses, and a Cipher object.
• You use the read method of the CipherInputStream class to
read the encrypted data from InputStream.
• CipherOutputStream Class
• The CipherOutputStream class represents a secure output
stream used for encrypting and decrypting data.
• It is a FilterOutputStream class, which consists of an
OutputStream, its subclasses, and a Cipher object. You use
the write method of the CipherOutputStream class to write
the encrypted data on the OutputStream.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 24 of 56
- 25. J2EE Application Security
Java Security APIs (Contd.)
• Java Cryptography Extensions (Contd.)
• JCE API (Contd.)
• KeyAgreement Class
• The KeyAgreement class provides functionality for encrypting
and decrypting data using a key agreement protocol.
• A shared secret key is created using the KeyGenerator and
KeyFactory classes. An instance of the KeyAgreement class is
created using the getInstance() method of the
KeyAgreement class.
• KeyGenerator Class
• The KeyGenerator class generates symmetric keys for
symmetric algorithms. You create a key generator by creating
an instance of the KeyGenerator class using the
getInstance() method.
• A key generator generates symmetric keys for an algorithm
using the generateKey() method.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 25 of 56
- 26. J2EE Application Security
Java Security APIs (Contd.)
• Java Cryptography Extensions (Contd.)
• JCE API (Contd.)
• Mac Class
• You use the Mac class to impart functionality of a MAC
algorithm in Java applications.
• MAC algorithm is a cryptographic hash function that accepts a
message and a secret key to generate a fixed-size output.
• J2SE provides the javax.crypto.Mac class to generate a
message.
• You use the getInstance() method of the Mac class to create
an object of the Mac class.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 26 of 56
- 27. J2EE Application Security
Java Security APIs (Contd.)
• Java Cryptography Extensions (Contd.)
• JCE API (Contd.)
• SecretKeyFactory Class
• The SecretKeyFactory class represents a factory for secret
keys.
• Keys are the opaque cryptographic keys that belong to the
java.security.Key package.
• You use the javax.crypto.SecretKeyFactory object to
perform operations on symmetric keys.
• The java.security.KeyFactory object is used to perform
operations on asymmetric keys.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 27 of 56
- 28. J2EE Application Security
Java Security APIs (Contd.)
• Java Cryptography Extensions (Contd.)
• JCE API (Contd.)
• SealedObject Class
• The SealedObject class enables you to create an object and
guard its confidentiality by using a cryptographic algorithm.
• The SealedObject class encapsulates the original object in a
serialized format and encrypts its data using a cryptographic
algorithm, such as DES.
• You decrypt the encrypted data using the correct decryption
key and algorithm and de-serialize it to produce the original
object.
• You can decrypt the encrypted object using the Cipher object
and using the decryption key.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 28 of 56
- 29. J2EE Application Security
Java Security APIs (Contd.)
• JCE-Based Authentication
• You need to perform various steps in implementing JCE-based
authentication, which are:
• Generating a key: Generates a key by creating an instance of
KeyGenerator for DES algorithm. You can use the same key
generator for generating further keys.
• Encrypting the data: Includes creating an object of the Cipher
class using the getInstance() method, and encrypts the
plaintext.
• Decrypting the data: Decrypts the encrypted plaintext.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 29 of 56
- 30. J2EE Application Security
Java Security APIs (Contd.)
• JAAS API
• Java Authentication and Authorization Service (JAAS) offer a security
API that provides authentication and authorization services for the
users.
• Authentication is the method of proving the identity to an end user.
• Authorization is the method of determining the security privileges of an
end user for accessing the various network resources.
• The class contained in JAAS API is divided into four categories:
• Common Classes: Subject, Principal, and Credential
• Authentication Class: LoginContext
• Authentication Interfaces: LoginModule, CallbackHandler, and
Callback
• Authorization Classes: Policy, AuthPermission, and
PrivateCredentialPermission
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 30 of 56
- 31. J2EE Application Security
Java Security APIs (Contd.)
• JAAS API (Contd.)
• Common Classes
• The common classes are the classes that are frequently used in
the authentication and authorization process.
• The common classes include the Subject, Principal, and
Credential classes.
• You can use the public Subject() and public Subject(boolean
readPermssion, Set principal, Set publicCredential, Set
privateCredential)constructors to create an instance of the
Subject class.
• You can retrieve the Principal objects associated with a Subject
class by using the methods, public Set getPrincipals() and
public Set getPrincipals(Class cl).
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 31 of 56
- 32. J2EE Application Security
Java Security APIs (Contd.)
• JAAS API (Contd.)
• Common Classes (Contd.)
• A credential is referred to as the security-related attributes that
are possessed by a Subject class.
• Credentials are divided into two categories based on the nature of
data they are storing.
• Private credential stores the sensitive data, such as the private
keys.
• Public credential stores the data to be shared among users, such
as the public key certificates.
• You can retrieve the public credentials associated with a Subject
class using the methods public Set
getPublicCredentials()and public Set
getPublicCredentials(Class cl).
• You can retrieve the private credentials associated with a Subject
class using the methods, public Set getPrivateCredentials()
and public Set getPrivateCredentials(Class cl).
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 32 of 56
- 33. J2EE Application Security
Java Security APIs (Contd.)
• JAAS API (Contd.)
• Authentication Classes
• Authentication classes are used for authenticating a Subject
class.
• The LoginContext class is an authentication class located in the
javax.security.auth.login package, and is used for
authenticating a subject.
• The LoginContext class determines the authentication services
provided to a subject using the LoginModule interface.
• Authentication Interfaces
• Authentication interfaces provide a set of classes that authenticate
a Subject class.
• The LoginModule interface enables you to plug in different
authentication techniques in an application.
• The LoginModule interface uses the CallbackHandler interface to
communicate with a user in order to retrieve authentication
information.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 33 of 56
- 34. J2EE Application Security
Java Security APIs (Contd.)
• JAAS API (Contd.)
• Authorization Classes
• Authorization classes are used to provide access permissions to
various common classes.
• You can use the public AuthPermission(String
permissionName) and public AuthPermission(String
permissionName, String permissionActions) constructors to
create an instance of the AuthPermission class.
• The PrivateCredentialPermission class is used to restrict the
access to private credentials of a Subject.
• You can use thepublic PrivateCredentialPermission(String
permissionName, String permissionActions) constructor to
create an instance of the PrivateCredentialPermission class.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 34 of 56
- 35. J2EE Application Security
Java Security APIs (Contd.)
• JAAS-based Authentication
• The steps that you need to perform for implementing JAAS-based
authentication for authenticating a user or a service are:
• Create an instance of the LoginContext class in an application.
• The LoginContext class refers to the Configuration class in order
to configure the LoginModules for the application.
• Invoke the login() method of the LoginContext class to load
LoginModules for authenticating a subject.
• Retrieve the authentication status to the application by the
LoginContext class.
• Retrieve the Subject class along with the Principal objects and
credentials from the LoginContext class on successful
authentication.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 35 of 56
- 36. J2EE Application Security
Implementing Security Using Java
Cryptography Extensions
• Problem Statement
• Certified Carriers is an institute that runs various professional
courses for students. Ron Floyd, the faculty at the institute, is
teaching Java Cryptography Extensions (JCE) to students. Ron
has taught various classes and interfaces in JCE and explained
the process of encryption and decryption to the students. Ron
has given a home assignment to the students to encrypt the
given data, decrypt the same, and display them on the screen.
How do the students perform this task?
• Solution
• To solve the preceding problem, perform the following tasks:
1. Code the application
2. Compile and execute the application
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 36 of 56
- 37. J2EE Application Security
Authentication in J2EE
• Authentication is the process of identifying a user.
• There are other authentication techniques, such as using smart card,
fingerprint reader, and voiceprint reader.
• Web Container Authentication
• Various types of authentication techniques to validate user information
are:
• HTTP Basic Authentication
• HTTP Digest Authentication
• FORM Based Authentication
• HTTPS Authentication
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 37 of 56
- 38. J2EE Application Security
Authentication in J2EE (Contd.)
• Web Container Authentication (Contd.)
• HTTP Basic Authentication
• HTTP Basic Authentication is a technique of authenticating site
users before allowing them access to the protected resources of a
Web site.
• In basic authentication, the server enforces the security through
the Web browser by verifying the username and password supplied
by a Web client.
• HTTP Digest Authentication
• HTTP Digest authentication is an authentication technique where a
site administrator needs to specify the contents that are to be
secured on a Web site, and the site users that can have access to
the content.
• In digest authentication, user information is encrypted before it is
sent to the server.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 38 of 56
- 39. J2EE Application Security
Authentication in J2EE (Contd.)
• Web Container Authentication (Contd.)
• FORM Based Authentication
• Form-based authentication enables you to create a customized
login page for a Web application.
• Form-based authentication is performed using the servlet
specification.
• For transferring the data over a secure connection, the server
must implement SSL.
• Implementation of SSL transfers the data posted through the login
form over a secured connection.
• HTTPS Authentication
• HTTPS stands for HTTP over SSL. HTTPS authentication is used for
authenticating the site users using digital certificates.
• HTTPS authentication uses SSL that provides various security
features such as data encryption, message integrity, and server
authentication.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 39 of 56
- 40. J2EE Application Security
Authentication in J2EE (Contd.)
• EJB Container Authentication
• EJB Container performs the user authentication using a Web container,
which implements the protection domain of Web components.
• EJB Container supports Common Secure Interoperability (CSI) protocol.
• The various roles of EJB Container for authentication are:
• Verifying the identity of an end user that calls the business
method.
• Verifying the deployment information contained in EJB, to check
whether an end user is a member of a role that has granted the
access permission for the business method or not.
• In case of illegal access, the java.rmi.RemoteException is thrown.
• Logging any illegal access.
• Making the information about a role and an end user available to
EJB for applying additional security checks.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 40 of 56
- 41. J2EE Application Security
Authorization in J2EE
• Authorization specifies the rights assigned to an authenticated user to access
the resources of a Web application.
• Using authorization, a Web application distinguishes what data and resources
are to be made available to what type of users.
• Authorization in J2EE is performed using two different techniques:
• Declarative authorization: An end user deploys and configures an
application, which is managed by the container.
• Programmatic authorization: A component embeds and manages the
application.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 41 of 56
- 42. J2EE Application Security
Authorization in J2EE (Contd.)
• Declarative Authorization
• Declarative authorization for a J2EE application is established externally
to a J2EE component.
• A deployment descriptor file describes the security roles for the
components and the permissions required for accessing a component.
• An application component provider specifies the <security-
constraint> element along with the <auth-constraint> sub element
in the deployment descriptor to control the access to a resource
declaratively.
• An application component provider or an application assembler defines
different security roles and methods of a bean interface to restrict the
access to an enterprise bean resource.
• The security roles and methods are declared using the <method-
permission> element in the deployment descriptor.
• You can invoke a method irrespective of a user’s identity by inserting
the unchecked element to the <method-permission> element.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 42 of 56
- 43. J2EE Application Security
Authorization in J2EE (Contd.)
• Programmatic Authorization
• Programmatic authorization for a J2EE application is established within
an EJB component.
• Programmatic authorization uses methods of the HttpServletRequest
interface to customize security.
• The getUserPrincipal() and isUserInRole() methods are used to
control access to a Web Resource.
• The getCallerPrincipal() and isCallerInRole() methods are used
to control access to an enterprise bean resource.
• An application assembler needs to add the <security-role-ref>
element for each role that you want to insert within the bean.
• The assembler also adds the <security-role> element for the <role-
link> element in each <security-role-ref> element.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 43 of 56
- 44. J2EE Application Security
Implementing Programmatic
Authorization
• Problem Statement
• John, the manager of Global Systems Inc., wants to implement
role-based access to the sensitive resources of his organization.
John wants that only a user with the manager role should be
able to access the manager’s home page. All other users should
be redirected to the visitor’s home page. Chris, the Web
developer at Global Systems, is assigned the task to
authenticate users using form-based authentication
programmatically.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 44 of 56
- 45. J2EE Application Security
Implementing Programmatic
Authorization (Contd.)
• To solve the preceding problem, perform the following tasks:
• Create users using the J2EE Admin Console.
• Create the login form for authentication.
• Create a servlet for authorization.
• Create a managers page using HTML.
• Create a visitors page using HTML.
• Create the J2EE Web application.
• Create the Web component.
• Create a security role.
• Specify the security elements for form-based
authentication.
• Map the security role.
• Deploy the application.
• Test the application.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 45 of 56
- 46. J2EE Application Security
Implementing Firewalls
• A firewall is a software system that enforces an access control policy for
communication between two networks, such as a LAN and the Internet.
• The enforcement of the access control policy is accomplished by either
blocking the network traffic or by permitting the network traffic.
• Types of Firewalls
• Firewalls that you use should be secure and certified by a trusted third
party, such as International Computer Security Association (ICSA).
• ICSA defines three types of firewalls:
• Packet Filter Firewalls
• Stateful Packet Inspection Firewall
• Demilitarized Zone (DMZ) Firewall
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 46 of 56
- 47. J2EE Application Security
Implementing Firewalls (Contd.)
• Types of Firewalls (Contd.)
• Packet Filter Firewall
• Accepts data packets only from a specified list of IP addresses.
• Are prone to IP spoofing and are very complicated to configure.
• Stateful Packet Inspection Firewall
• Examines each part of a data packet to determine whether to
service or reject the request for communication.
• Examines all the incoming communication to verify whether the
communication was requested earlier from within the network. If
no match is found, the incoming request is rejected.
• The communication that matches the previous request proceeds to
the next level of screening where the state of each data packet of
the request is verified.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 47 of 56
- 48. J2EE Application Security
Implementing Firewalls (Contd.)
• Types of Firewalls (Contd.)
• DMZ Firewall
• DMZ firewall allows public access only to the specified protected
area of a network.
• The protected area of network is called DMZ.
• Requests coming from external resources are not allowed to access
the resources of those network zones that are not part of DMZ.
• The creation of DMZ enables strict control over the network
resources you want others to access, and the resources that need
to be restricted from outside access.
• The use of DMZ firewall enables you determine the frequency with
which external users access information from DMZ of your
network, and for how long and how often they access the
particular resources.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 48 of 56
- 49. J2EE Application Security
Implementing Firewalls (Contd.)
• Implementing Secure Network Layout
• Implementing a Single Firewall
• In a single firewall network, all the messages that need to pass
between any system in an internal network and any system on the
rest of the Internet should pass through the firewall.
• The following figure shows the implementation of a single firewall:
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 49 of 56
- 50. J2EE Application Security
Implementing Firewalls (Contd.)
• Implementing Secure Network Layout (Contd.)
• Implementing a Double Firewall and a DMZ
• In a double firewall and DMZ approach, the external firewall
enables the network traffic to pass through the services in DMZ.
• A message cannot be passed directly to an internal network in
case of double firewall and is passed through a proxy server
available in the DMZ. The following figure shows the
implementation of a double firewall and DMZ:
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 50 of 56
- 51. J2EE Application Security
Implementing Firewalls (Contd.)
• Pros and Cons of Implementing Firewalls
• You use firewall to protect the resources of a network from
unauthorized use.
• The various advantages of using firewalls are:
• Blocks unwanted incoming data that may contain a hacker attack.
• Hides information about the network by diverting the outgoing
traffic through the firewall rather than the network.
• Checks outgoing traffic to restricted use of Internet and prevents
access to unwanted sites.
• The various disadvantages of using firewalls are:
• Separate networks require a lot of work to configure and
administer the firewall.
• Degrades the performance and scalability of the network.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 51 of 56
- 52. J2EE Application Security
Summary
• In this lesson, you learned that:
• J2EE architects need to identify and assess security threats during the
design phase of an application.
• The risk assessment task undertaken by the architects must cover an
analysis of the threats, vulnerabilities in application design, and the
threat consequences to application data and resources.
• J2EE architects sometimes do a partial threat analysis due to following
reasons:
• Undervalued benefits
• Measurement challenges
• Focus on vulnerabilities
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 52 of 56
- 53. J2EE Application Security
Summary (Contd.)
• The major activities that needs to be performed by J2EE architects in threat
analysis include:
• Threat identification
• Measurement
• Determine strategy
• The security to a network environment can be provided by implementing
various security techniques, such as cryptography, digital signatures, digital
certificates, and Secure Socket Layer (SSL).
• Cryptography is the mechanism of sending and receiving messages over a
network in a secure format. Cryptography can be classified into two types,
symmetric and asymmetric cryptography.
• Digital signature is an encrypted text to authenticate the sender of a
message or a document.
• Digital certificate is a signed statement, which contains information, such as
the name of its holder, a serial number, and a public key.
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 53 of 56
- 54. J2EE Application Security
Summary (Contd.)
• Secure Socket Layer (SSL) is a protocol developed by Netscape to perform
reliable, end-to-end, and secure transactions over the Internet.
• Java Cryptography Extensions (JCE) provides implementation for encrypting
data, generating a key, and generating Message Authentication Code (MAC)
algorithms.
• The various components of the JCE API are:
• Password-based encryption (PBE) techniques
• Key agreement
• Symmetric bulk encryption algorithms, such as DES, IDEA, and RES
• Symmetric stream encryption algorithms, such as RC4
• Asymmetric encryption algorithms, such as RSA
• MAC algorithms
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 54 of 56
- 55. J2EE Application Security
Summary (Contd.)
• The various steps in implementing JCE-based authentication, are:
• Generating a key
• Encrypting the data
• Decrypting the data
• Java Authentication and Authorization Service (JAAS) offer a security API
that provides authentication and authorization services for the users. The
class contained in JAAS API is divided into four categories:
• Common Classes: Subject, Principal, and Credential
• Authentication Class: LoginContext
• Authentication Interfaces: LoginModule, CallbackHandler, and
Callback
• Authorization Classes: Policy, AuthPermission, and
PrivateCredentialPermission
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 55 of 56
- 56. J2EE Application Security
Summary (Contd.)
• Authentication is the process of identifying a user. The various types of
authentication techniques to validate user information are HTTP Basic
Authentication, HTTP Digest Authentication, FORM Based Authentication, and
HTTPS Authentication.
• Authorization specifies the rights assigned to an authenticated user to access
the resources of a Web application. There are two types of authentication
techniques, declarative and programmatic.
• A firewall is a software system that enforces an access control policy for
communication between two networks, such as a LAN and the Internet.
International Computer Security Association (ICSA) defines three types of
firewalls:
• Packet Filter Firewalls
• Stateful Packet Inspection Firewall
• Demilitarized Zone (DMZ) Firewall
©NIIT Architecting J2EE Solutions Lesson 4A / Slide 56 of 56