How Online Financial Fraud Targets Users' Bank Accounts
•
2 recomendaciones•1,030 vistas
Hacking banks is difficult..which is why hackers are targeting customers...
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Grift horse money stealing trojan takes 10m android users for a ride

Grift horse money stealing trojan takes 10m android users for a ride
The Whys and Wherefores of Web Security – by United Security Providers

The Whys and Wherefores of Web Security – by United Security Providers
Destacado
Destacado (6)
History of the British Museum’s buildings over the past 260 years

History of the British Museum’s buildings over the past 260 years
Similar a How Online Financial Fraud Targets Users' Bank Accounts
Similar a How Online Financial Fraud Targets Users' Bank Accounts (20)
New Malicious Attacks on Mobile Banking Applications

New Malicious Attacks on Mobile Banking Applications
CrossTalk - The Art of Cyber Bank Robbery - Stealing your Money Through Insid...

CrossTalk - The Art of Cyber Bank Robbery - Stealing your Money Through Insid...
Trylogic- Cyber security by Vikalp Sharma- FDP Presentation July 9 2020

Trylogic- Cyber security by Vikalp Sharma- FDP Presentation July 9 2020
Discuss similarities and differences between and Trojan.docx

Discuss similarities and differences between and Trojan.docx
Discuss similarities and differences between and Trojan.docx

Discuss similarities and differences between and Trojan.docx
Symantec Website Security Threat Report 2014 - RapidSSLOnline

Symantec Website Security Threat Report 2014 - RapidSSLOnline
Más de Prayukth K V
Más de Prayukth K V (20)
State of the internet of things (IoT) market 2016 edition

State of the internet of things (IoT) market 2016 edition
Drones and the Internet of Things: realising the potential of airborne comput...

Drones and the Internet of Things: realising the potential of airborne comput...
Último
Call Us ➥9319373153▻Call Girls In North Goa

Call Us ➥9319373153▻Call Girls In North GoaCall girls in Goa, +91 9319373153 Escort Service in North Goa
Enjoy ➥8448380779▻ Call Girls In Sector 18 Noida Escorts Delhi NCR

Enjoy ➥8448380779▻ Call Girls In Sector 18 Noida Escorts Delhi NCRStunning ➥8448380779▻ Call Girls In Hauz Khas Delhi NCR
Último (20)
International Business Environments and Operations 16th Global Edition test b...

International Business Environments and Operations 16th Global Edition test b...
8447779800, Low rate Call girls in Rohini Delhi NCR

8447779800, Low rate Call girls in Rohini Delhi NCR
8447779800, Low rate Call girls in Shivaji Enclave Delhi NCR

8447779800, Low rate Call girls in Shivaji Enclave Delhi NCR
8447779800, Low rate Call girls in Kotla Mubarakpur Delhi NCR

8447779800, Low rate Call girls in Kotla Mubarakpur Delhi NCR
(Best) ENJOY Call Girls in Faridabad Ex | 8377087607

(Best) ENJOY Call Girls in Faridabad Ex | 8377087607
NewBase 19 April 2024 Energy News issue - 1717 by Khaled Al Awadi.pdf

NewBase 19 April 2024 Energy News issue - 1717 by Khaled Al Awadi.pdf
Enjoy ➥8448380779▻ Call Girls In Sector 18 Noida Escorts Delhi NCR

Enjoy ➥8448380779▻ Call Girls In Sector 18 Noida Escorts Delhi NCR
Church Building Grants To Assist With New Construction, Additions, And Restor...

Church Building Grants To Assist With New Construction, Additions, And Restor...
Memorándum de Entendimiento (MoU) entre Codelco y SQM

Memorándum de Entendimiento (MoU) entre Codelco y SQM
Independent Call Girls Andheri Nightlaila 9967584737

Independent Call Girls Andheri Nightlaila 9967584737
Japan IT Week 2024 Brochure by 47Billion (English)

Japan IT Week 2024 Brochure by 47Billion (English)
Global Scenario On Sustainable and Resilient Coconut Industry by Dr. Jelfina...

Global Scenario On Sustainable and Resilient Coconut Industry by Dr. Jelfina...
How Online Financial Fraud Targets Users' Bank Accounts
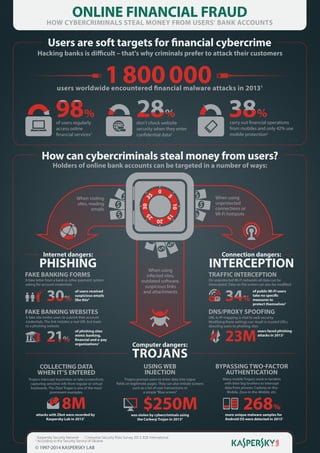
- 1. ONLINE FINANCIAL FRAUD HOW CYBERCRIMINALS STEAL MONEY FROM USERS’ BANK ACCOUNTS Users are soft targets for financial cybercrime Hacking banks is difficult – that's why criminals prefer to attack their customers 1 800 000 98% 28% 38% users worldwide encountered financial malware attacks in 20131 of users regularly access online financial services2 don’t check website security when they enter confidential data2 carry out financial operations from mobiles and only 42% use mobile protection2 How can cybercriminals steal money from users? Holders of online bank accounts can be targeted in a number of ways: 5 30 3 5 0 25 10 1 5 When visiting sites, reading emails When using unprotected connections or Wi-Fi hotspots 20 Internet dangers: PHISHING FAKE BANKING FORMS A fake letter from a bank or other payment system asking for account credentials 30% of users received suspicious emails like this2 Connection dangers: When using infected sites, outdated software, suspicious links and attachments 21% TRAFFIC INTERCEPTION On unprotected Wi-Fi networks all data can be intercepted. Data on the screen can also be modified 34% of public Wi-Fi users take no specific measures to protect themselves2 DNS/PROXY SPOOFING FAKE BANKING WEBSITES A fake site invites users to submit their account credentials. The link imitates a real URL but leads to a phishing website of phishing sites mimic banking, financial and e-pay organizations1 INTERCEPTION URL to IP mapping is vital to web security. Modifying these settings can result in trusted URLs directing users to phishing sites users faced phishing attacks in 20131 Computer dangers: TROJANS 23M COLLECTING DATA WHEN IT’S ENTERED USING WEB INJECTION BYPASSING TWO-FACTOR AUTHENTICATION Trojans intercept keystrokes or take screenshots, capturing sensitive info from regular or virtual keyboards. The Zbot Trojan is one of the most prominent examples. Trojans prompt users to enter data into rogue fields on legitimate pages. They can also imitate screens such as a list of user transactions or a simple “Blue screen” Many mobile Trojans work in tandem with their big brothers to intercept data from phones: Carberp-in-theMobile, Zeus-in-the-Mobile, etc. attacks with Zbot were recorded by Kaspersky Lab in 20131 was stolen by cybercriminals using the Carberp Trojan in 20133 8M 1 3 $250M Kaspersky Security Network 2 Consumer Security Risks Survey 2013, B2B International According to the Security Service of Ukraine © 1997-2014 KASPERSKY LAB 268% more unique malware samples for Android OS were detected in 20131
