slideshow 2
•Descargar como PPT, PDF•
1 recomendación•238 vistas
Denunciar
Compartir
Denunciar
Compartir
Más contenido relacionado
La actualidad más candente
La actualidad más candente (18)
Internet and url by marivic s. manlagnit jmames ict coordinator

Internet and url by marivic s. manlagnit jmames ict coordinator
Similar a slideshow 2
Intro. to internet architecture& protocol by zubair yaseen&yameen shakir

Intro. to internet architecture& protocol by zubair yaseen&yameen shakirUniversity of Education
Similar a slideshow 2 (20)
Intro. to internet architecture& protocol by zubair yaseen&yameen shakir

Intro. to internet architecture& protocol by zubair yaseen&yameen shakir
GSBA - IT Orientation Program by Prof. Amit Chandra

GSBA - IT Orientation Program by Prof. Amit Chandra
Último
Último (20)
Designing IA for AI - Information Architecture Conference 2024

Designing IA for AI - Information Architecture Conference 2024
Scanning the Internet for External Cloud Exposures via SSL Certs

Scanning the Internet for External Cloud Exposures via SSL Certs
"Debugging python applications inside k8s environment", Andrii Soldatenko

"Debugging python applications inside k8s environment", Andrii Soldatenko
TrustArc Webinar - How to Build Consumer Trust Through Data Privacy

TrustArc Webinar - How to Build Consumer Trust Through Data Privacy
TeamStation AI System Report LATAM IT Salaries 2024

TeamStation AI System Report LATAM IT Salaries 2024
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
The Ultimate Guide to Choosing WordPress Pros and Cons

The Ultimate Guide to Choosing WordPress Pros and Cons
H2O.ai CEO/Founder: Sri Ambati Keynote at Wells Fargo Day

H2O.ai CEO/Founder: Sri Ambati Keynote at Wells Fargo Day
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)

Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
WordPress Websites for Engineers: Elevate Your Brand

WordPress Websites for Engineers: Elevate Your Brand
Powerpoint exploring the locations used in television show Time Clash

Powerpoint exploring the locations used in television show Time Clash
slideshow 2
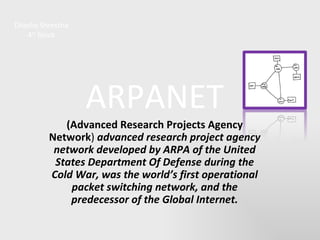
- 1. Dilasha Shrestha 4 th block ARPANET (Advanced Research Projects Agency Network ) advanced research project agency network developed by ARPA of the United States Department Of Defense during the Cold War, was the world’s first operational packet switching network, and the predecessor of the Global Internet.