Cicret Bracelet Doccument
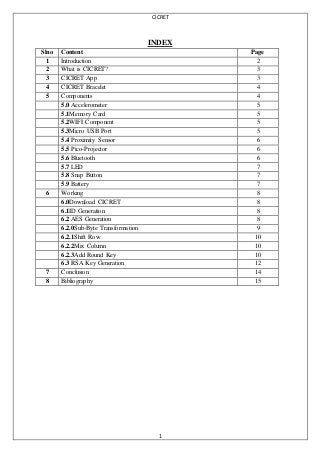
- 1. CICRET 1 INDEX Slno Content Page 1 Introduction 2 2 What is CICRET? 3 3 CICRET App 3 4 CICRET Bracelet 4 5 Components 4 5.0 Accelerometer 5 5.1Memory Card 5 5.2WIFI Component 5 5.3Micro USB Port 5 5.4 Proximity Sensor 6 5.5 Pico-Projector 6 5.6 Bluetooth 6 5.7 LED 7 5.8 Snap Button 7 5.9 Battery 7 6 Working 8 6.0Download CICRET 8 6.1ID Generation 8 6.2 AES Generation 8 6.2.0Sub-Byte Transformation 9 6.2.1Shift Row 10 6.2.2Mix Column 10 6.2.3Add Round Key 10 6.3 RSA Key Generation 12 7 Conclusion 14 8 Bibliography 15
- 2. CICRET 2 INTRODUCTION We are living in a world where the security of data has the upmost priority of all. The world around us is evolving each and every single minute. Social networking is the powerful aspect now. People want their life to be easy and needs a smooth movement towards the future. The developers took this into account to create the next revolution technology – CICRET. CICRET is the developed based on the cloud technology. Cicret is the technology of the future. Cicret consists of 2 parts. 1 is the application part and the other is a wearable bracelet. The Cicret App is the only intuitive, secure and free solution for those who want to chat, share and exchange safely with no chance of being traceable. The app is an innovative encrypted technology providing anonymity and full control on all contents you have shared, even after sending them. It allows you to give all your personal information always with you, on your arm. The idea came from the opinion that the cloud system is not safe and there is no other place to protect your digital privacy than yourself. Cicret is the next level technology that’s easy to adapt to human environment and it would make Google Glass a primitive technology in the year 2015 when its expected to be released.
- 3. CICRET 3 WHAT IS CICRET CICRET is the combination of two parts 1) CICRET APP 2) CICRET BRACELET It’s the combination of two products with a single idea: to give you the control. CICRET APP The CICRET is the only intuitive, secure and free solution for those who want to chat, share and exchange safely with no chance of being traceable. It’s an innovative encrypted technology providing anonymity and full control on all contents you have shared, even after sending them. The CICRET app available on Android. Features: Timer : Define the life time of your outbox contents, by the duration or by the number of views. Edit : Remotely adjust whatever you sent. Delete : Remotely erase whatever you wrote. Exchange whatever you want with whoever you want (Pictures, Videos, Document, Notes, Audio etc…) Stores a file on your computer and remotely gets it back on your smart phone via CICRET Only those to whom you gave your ID, CICRET can contact you and vice versa. Data access at anywhere at any time.
- 4. CICRET 4 CICRET BRACELET With the Cicret Bracelet,you can make your skin your new touchscreen. Read your mails, play your favourite games, answer your calls, check the weather, find your way…Do whatever you want onyour arm. COMPONENTS The CICRET bracelet is the aggregation of many components: Accelerometer Memory Card ROM Processor Vibrator Micro USB port Battery Proximity Sensor (Long Range) Pico Projector Bluetooth Wifi Component LED Snap Button
- 5. CICRET 5 ACCELEROMETER Accelerometers are used to detect and monitor vibration in rotating machinery. Accelerometers are used in tablet computers and digital cameras so that images on screens are always displayed upright. Accelerometers are used in drones for flight stabilisation. In smart phones the display gets tilted automatically to adjust to users view due to the working of the accelerometer. In CICRET, when the bracelet is shook twice, it gets activated and when shooked again puts it in a sleep mode. MEMORY CARD A memory card or flash card is an electronic flash memory data storage device used for storing digital information. These are commonly used in many electronic devices, including digital cameras, mobile phones, laptop computers, MP3 playersand video game consoles, Tablets. Most of these can be diminutive, re-recordable, and can retain data without power. 16 to 32GB is currently available for CICRET. WIFI COMPONENT The wifi component enables connection between the smart phone and the CICRET bracelet as long as there is an internet connection available for the two devices. MICRO USB PORT CICRET bracelet has a micro USB port to connect to the system for data transfer between the system and the bracelet. Exchange of information’s could include images, music, document etc
- 6. CICRET 6 PROXIMITY SENSOR (LONG RANGE) Is a sensor able to detect the presence of nearby objects without any physical contact. A proximity sensor often emits an electromagnetic field or a beam of electromagnetic radiation (infrared, for instance), and looks for changes in the field or return signal. The object being sensed is often referred to as the proximity sensor's target. Different proximity sensor targets demand different sensors. The picoprojector projects the interface to our arm. When you place your finger on your interface, it stops one of the 8 long range PROXIMITY SENSOR. The SENSOR sends back the information to the processor place in the CICRET bracelet. BLUETOOTH When internet connection is unavailable the CICRET app and bracelet can be connected via Bluetooth and also the Bluetooth can be used to exchange data/information to other devices. PICOPROJECTOR It’s technology that applies the use of an image projector in an handheld device. It is a response to the emergence/development of compact portable devices such as mobile phones, personal digital assistants, and digital cameras, which have sufficient storage capacity to handle presentation materials but little space to accommodate an attached display screen. Handheld projectors involve miniaturized hardware and software that can project digital images onto any nearby viewing surface LED The LED is used to show notifications and is used to show the working of a process. SNAP BUTTON The snap button is a power switch that turns the CICRET bracelet on and off.
- 7. CICRET 7 BATTERY CICRET uses a battery that is to provide 8 hours of lifetime continuously.
- 8. CICRET 8 WORKING The working of CICRET could be explained in 5 steps. STEP 1: Download CICRET STEP 2: ID Generation STEP 3: AES Key Generation STEP 4: RSA Key Generation STEP 5: Encrypted Communication These 5 steps are explained in detail below to fully understand the proper working of the CICRET. STEP 1 :DOWNLOAD CICRET The CICRET application is available on android play store. Downloading and installation process is as easy as any app. STEP 2 :ID GENERATION As the app gets started for the first time, it asks for user password. When the user password is entered and is recognized as the key. STEP 3 :AES KEY GENERATION The AES stands for Advanced Encryption Standard. This standard was established by the US NIST(National Institute of Standards and Technologies). AES is based on Rjindael Cipher. In CICRET,we use AES-256 encryption. The AES 256 has the following peculiarities: Key Length : 8 Block Size : 32 Bytes Number of Rounds : 14 AES-256 means that there could be 2256 possible keys. A PC that uses 255keys per second needs 149 billion years to break AES 256. A single round in AES-256 consist of 4 stages. 1. Sub-Bytes Transformation 2. Shift Row 3. Mix Columns 4. Add Round Key The AES algorithm operations are performed on a two dimension array of bytes called States.
- 9. CICRET 9 AES Encryption The above figure shows the encryption of the AES 128. Here plain text of 128 bits are copied to a 4x4 bytes matrix states. A key of M bytes are expanded and added with the states. Based on the type of AES used, here we use AES-128, we perform 10 rounds of encryption. Where
- 10. CICRET 10 each round would perform the 4 stages (as mentioned above) based on the number of rounds. The number of rounds are based on the type of AES used. AES-128 : 10 Rounds AES-256 : 14 Rounds As in the figure showed above, the AES key is expanded each round and is added during the stage – Add Round Key. W represents the word and the parameters specify the word number.
- 11. CICRET 11 W[0,3] – Word 0 to Word 3. The figure below shows the key expansion during each round. STAGE 1 :Add Round Key In this method, the key is added with the state S to produce a new state S’.
- 12. CICRET 12 STAGE 2 :Sub-Byte Transformation In Sub-Byte Transformation, byte by byte transformation takes place. Each byte in S(row,column) is transformed to S’ (row,column) using S-Box Table. The S-Box Table diagram is shown below. In the table above we can see that the hexadecimal 53is replaced with ED. The figure bellows provides a bit more detailed understanding about Sub Byte Transformation.
- 13. CICRET 13 STAGE 3 :Shift Row Here in this method, circular left shift happens based on the row number. STAGE 4 :Mix Column In this method the matrix is multiplied with a column and the result is stored in another column in S’.
- 14. CICRET 14 In AES-256 encryption each method is executed 14 rounds one by one to complete the encryption. To decrypt the content we need the same key and we need to inverse the encryption process. Decryption without the key is practically impossible. The example for AES encryption is shown below: Here we can see that the message: “GOOD MORNING” is encrypted with the key – 123 and the encrypted message generated based on its algorithm is: /gxCvp1k7zQYnYV7MnBoLG1EjxOmLw7cUVrVxUdwQu8=
- 15. CICRET 15 STEP 4 : RSA KEY GENERATION RSA is stands for the names of the 3 persons who designed it :Rivest, Shamir, Adleman. RSA is the first public key cryptosystem and is widely in use for secure data transmission. RSA follows asymmetric cryptography, which means that we use 2 keys for encryption and decryption. The 2 keys are: 1) Public Key 2) Private Key A Public Key which may be known by anybody, can be used to encrypt messages and to verify signatures. The private key is known only to the recipient to decrypt the message and create signatures. Digital Signature In CICRET, a unique RSA key is generated each time you add a contact and you exchange with the server.
- 16. CICRET 16 Conclusion CICRET is the technology that would revolutionize the way we use and interact with applications. It is the safest way to exchange information and provides a firm set of data security encryption and decryption methods that’s. It would replace Google Glass and wouldn’t be surpassed for another 2-3 years.
- 17. CICRET 17 BIBLIOGRAPHY http://www.cicret.com/wordpress/ http://en.wikipedia.org/wiki/Advanced_Encryption_Standardwww.cicret.com http://en.wikipedia.org/wiki/RSA_(cryptosystem)www.cicret.com http://en.wikipedia.org/wiki/Public-key_cryptography https://www.youtube.com/watch?v=9J7GpVQCfms https://www.youtube.com/watch?v=vBum40uRTxc http://www.cicret.com/wordpress/?p=17836 https://www.lri.fr/~fmartignon/documenti/systemesecurite/5-AES.pdf http://aesencryption.net/