[Infographic]]Managing Assets and Endpoints
•
0 recomendaciones•1,695 vistas
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
The borders of enterprise network infrastructure are porous at best. It’s too late to close them, and it’s probably best that you don’t. Cloud services, mobility, and technology adopted by lines-of-business (also known as shadow IT) may erode much of the control you once had over your infrastructure, but your business is using these technologies for a reason. They get the job done.
What you need to do is gain as much visibility and management as possible over these networks and services. The Borderless Enterprise enables this transformation.
These slides - based on the webinar featuring Shamus McGillicuddy, research director at Enterprise Management Associates (EMA), Doug Roberts, director of products at Fluke Networks, and Mike Pennacchi, owner and lead network analyst at Network Protocol Specialists - cover:
- How enterprise IT organizations are succeeding with these new technologies
- Real-world examples of how IT can be an enabler and a partner in this new era
- Insights from new EMA research on the borderless enterprise
The Borderless Enterprise: Adapting Network Management to Mobility, Cloud, & ...

The Borderless Enterprise: Adapting Network Management to Mobility, Cloud, & ...Enterprise Management Associates
Más contenido relacionado
La actualidad más candente
The borders of enterprise network infrastructure are porous at best. It’s too late to close them, and it’s probably best that you don’t. Cloud services, mobility, and technology adopted by lines-of-business (also known as shadow IT) may erode much of the control you once had over your infrastructure, but your business is using these technologies for a reason. They get the job done.
What you need to do is gain as much visibility and management as possible over these networks and services. The Borderless Enterprise enables this transformation.
These slides - based on the webinar featuring Shamus McGillicuddy, research director at Enterprise Management Associates (EMA), Doug Roberts, director of products at Fluke Networks, and Mike Pennacchi, owner and lead network analyst at Network Protocol Specialists - cover:
- How enterprise IT organizations are succeeding with these new technologies
- Real-world examples of how IT can be an enabler and a partner in this new era
- Insights from new EMA research on the borderless enterprise
The Borderless Enterprise: Adapting Network Management to Mobility, Cloud, & ...

The Borderless Enterprise: Adapting Network Management to Mobility, Cloud, & ...Enterprise Management Associates
La actualidad más candente (20)
12 Game Changing Ways to Mobilize Teaching and Learning

12 Game Changing Ways to Mobilize Teaching and Learning
Cyber Tech Israel 2016: Get Your Head in the Cloud

Cyber Tech Israel 2016: Get Your Head in the Cloud
Accelerating Innovation Through Enterprise Mobility

Accelerating Innovation Through Enterprise Mobility
Human Centric Innovation - Driving Digital Transformation - Co-creation

Human Centric Innovation - Driving Digital Transformation - Co-creation
End-User Computing Insights: A study of digital maturity

End-User Computing Insights: A study of digital maturity
Gerenciamento de dispositivos móveis com Intune e SCCM

Gerenciamento de dispositivos móveis com Intune e SCCM
Three Keys to Building a Secure Mobile Infrastructure in Government Environments

Three Keys to Building a Secure Mobile Infrastructure in Government Environments
Remote Work Readiness Part 1: VDI and Remote Desktop Services (RDS)

Remote Work Readiness Part 1: VDI and Remote Desktop Services (RDS)
The Borderless Enterprise: Adapting Network Management to Mobility, Cloud, & ...

The Borderless Enterprise: Adapting Network Management to Mobility, Cloud, & ...
Primend Pilvekonverents - Mobiilne ettevõte mobiilsete andmetega

Primend Pilvekonverents - Mobiilne ettevõte mobiilsete andmetega
Manage Risk by Protecting the Apps and Data That Drive Business Productivity

Manage Risk by Protecting the Apps and Data That Drive Business Productivity
Destacado
Destacado (15)
WHITE PAPER▶ Protecting VMware Environments with Backup Exec 15

WHITE PAPER▶ Protecting VMware Environments with Backup Exec 15
Dridex: All You Need To Know About This Persistent Financial Trojan

Dridex: All You Need To Know About This Persistent Financial Trojan
Symantec Netbackup Delivering Performance Value Through Multiple De-duplicati...

Symantec Netbackup Delivering Performance Value Through Multiple De-duplicati...
WHITE PAPER▶ Blueprint for Optimized Duplication with Backup Exec 15

WHITE PAPER▶ Blueprint for Optimized Duplication with Backup Exec 15
The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...

The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...
The Forrester Wave™: Enterprise Mobile Management Q3 2014

The Forrester Wave™: Enterprise Mobile Management Q3 2014
Get Your Head in the Cloud: A Practical Model for Enterprise Cloud Security

Get Your Head in the Cloud: A Practical Model for Enterprise Cloud Security
TECHNICAL BRIEF▶ NDMP Backups with Backup Exec 2014

TECHNICAL BRIEF▶ NDMP Backups with Backup Exec 2014
Top Seven Risks of Enterprise Mobility - How to protect your business

Top Seven Risks of Enterprise Mobility - How to protect your business
Similar a [Infographic]]Managing Assets and Endpoints
Similar a [Infographic]]Managing Assets and Endpoints (20)
the new workspace: freedom to work whenever, wherever, on any device

the new workspace: freedom to work whenever, wherever, on any device
kaspersky presentation for palette business solution June 2016 v1.0.

kaspersky presentation for palette business solution June 2016 v1.0.
Introduction to Symantec Endpoint Management75.pptx

Introduction to Symantec Endpoint Management75.pptx
Solve Employee Experience, Security, and Silo Problems with HCL BigFix Workspace

Solve Employee Experience, Security, and Silo Problems with HCL BigFix Workspace
Telecommunications Working from home Security and remote working ca

Telecommunications Working from home Security and remote working ca
Mobile Convention Amsterdam 2014 - Microsoft - Maarten Sonneveld

Mobile Convention Amsterdam 2014 - Microsoft - Maarten Sonneveld
2° Sessione - Workspace ONE la soluzione semplice e sicura per il lavoro nell...

2° Sessione - Workspace ONE la soluzione semplice e sicura per il lavoro nell...
Is workforce mobility presenting new technology challenges?

Is workforce mobility presenting new technology challenges?
Government and Education Webinar: How the New Normal Could Improve your IT Op...

Government and Education Webinar: How the New Normal Could Improve your IT Op...
Citrix Flexcast + Assessment Approach Lunch & Learn

Citrix Flexcast + Assessment Approach Lunch & Learn
Más de Symantec
Más de Symantec (20)
Symantec Enterprise Security Products are now part of Broadcom

Symantec Enterprise Security Products are now part of Broadcom
Symantec Webinar | National Cyber Security Awareness Month: Fostering a Secur...

Symantec Webinar | National Cyber Security Awareness Month: Fostering a Secur...
Symantec Webinar | National Cyber Security Awareness Month: Protect IT

Symantec Webinar | National Cyber Security Awareness Month: Protect IT
Symantec Webinar | National Cyber Security Awareness Month: Secure IT

Symantec Webinar | National Cyber Security Awareness Month: Secure IT
Symantec Webinar | National Cyber Security Awareness Month - Own IT

Symantec Webinar | National Cyber Security Awareness Month - Own IT
Symantec Webinar: Preparing for the California Consumer Privacy Act (CCPA)

Symantec Webinar: Preparing for the California Consumer Privacy Act (CCPA)
Symantec Webinar | How to Detect Targeted Ransomware with MITRE ATT&CK

Symantec Webinar | How to Detect Targeted Ransomware with MITRE ATT&CK
Symantec Webinar | Security Analytics Breached! Next Generation Network Foren...

Symantec Webinar | Security Analytics Breached! Next Generation Network Foren...
Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...

Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...
Symantec Webinar | Tips for Successful CASB Projects

Symantec Webinar | Tips for Successful CASB Projects
Symantec Webinar: What Cyber Threats Are Lurking in Your Network?

Symantec Webinar: What Cyber Threats Are Lurking in Your Network?
Symantec Best Practices for Cloud Security: Insights from the Front Lines

Symantec Best Practices for Cloud Security: Insights from the Front Lines
Symantec - The Importance of Building Your Zero Trust Program on a Solid Plat...

Symantec - The Importance of Building Your Zero Trust Program on a Solid Plat...
Symantec Webinar | Redefining Endpoint Security- How to Better Secure the End...

Symantec Webinar | Redefining Endpoint Security- How to Better Secure the End...
Symantec Webinar Using Advanced Detection and MITRE ATT&CK to Cage Fancy Bear

Symantec Webinar Using Advanced Detection and MITRE ATT&CK to Cage Fancy Bear
Último
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Último (20)
Top 10 Most Downloaded Games on Play Store in 2024

Top 10 Most Downloaded Games on Play Store in 2024
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Top 5 Benefits OF Using Muvi Live Paywall For Live Streams

Top 5 Benefits OF Using Muvi Live Paywall For Live Streams
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
[Infographic]]Managing Assets and Endpoints
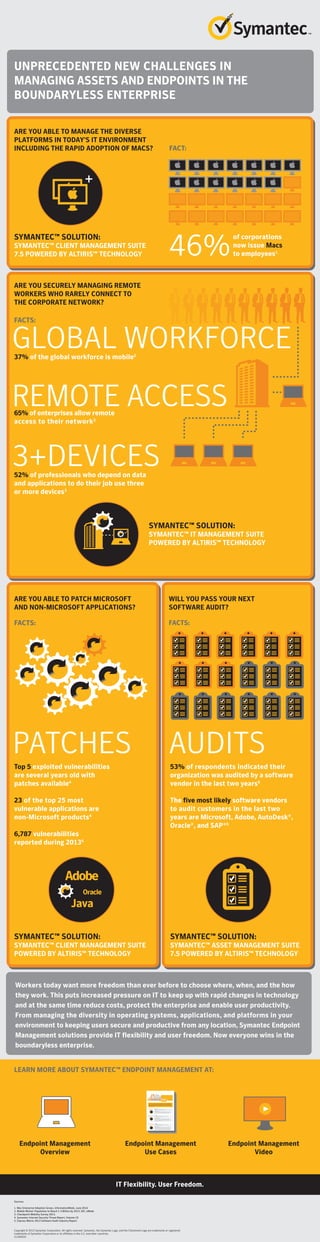
- 1. Adobe Java Oracle UNPRECEDENTED NEW CHALLENGES IN MANAGING ASSETS AND ENDPOINTS IN THE BOUNDARYLESS ENTERPRISE ARE YOU ABLE TO MANAGE THE DIVERSE PLATFORMS IN TODAY'S IT ENVIRONMENT INCLUDING THE RAPID ADOPTION OF MACS? FACT: SYMANTEC™ SOLUTION: SYMANTEC™ CLIENT MANAGEMENT SUITE 7.5 POWERED BY ALTIRIS™ TECHNOLOGY 46% of corporations now issue Macs to employees1 ARE YOU SECURELY MANAGING REMOTE WORKERS WHO RARELY CONNECT TO THE CORPORATE NETWORK? SYMANTEC™ SOLUTION: SYMANTEC™ IT MANAGEMENT SUITE POWERED BY ALTIRIS™ TECHNOLOGY GLOBAL WORKFORCE FACTS: 37% of the global workforce is mobile2 65% of enterprises allow remote access to their network3 52% of professionals who depend on data and applications to do their job use three or more devices3 REMOTE ACCESS 3+DEVICES ARE YOU ABLE TO PATCH MICROSOFT AND NON-MICROSOFT APPLICATIONS? Top 5 exploited vulnerabilities are several years old with patches available4 23 of the top 25 most vulnerable applications are non-Microsoft products4 6,787 vulnerabilities reported during 20134 PATCHES SYMANTEC™ SOLUTION: SYMANTEC™ CLIENT MANAGEMENT SUITE POWERED BY ALTIRIS™ TECHNOLOGY FACTS: WILL YOU PASS YOUR NEXT SOFTWARE AUDIT? 53% of respondents indicated their organization was audited by a software vendor in the last two years5 The five most likely software vendors to audit customers in the last two years are Microsoft, Adobe, AutoDesk®, Oracle®, and SAP®5 AUDITS FACTS: SYMANTEC™ SOLUTION: SYMANTEC™ ASSET MANAGEMENT SUITE 7.5 POWERED BY ALTIRIS™ TECHNOLOGY Workers today want more freedom than ever before to choose where, when, and the how they work. This puts increased pressure on IT to keep up with rapid changes in technology and at the same time reduce costs, protect the enterprise and enable user productivity. From managing the diversity in operating systems, applications, and platforms in your environment to keeping users secure and productive from any location, Symantec Endpoint Management solutions provide IT flexibility and user freedom. Now everyone wins in the boundaryless enterprise. LEARN MORE ABOUT SYMANTEC™ ENDPOINT MANAGEMENT AT: IT Flexibility. User Freedom. Endpoint Management Overview Endpoint Management Use Cases Endpoint Management Video Sources: 1. Mac Enterprise Adoption Grows, InformationWeek, June 2014 2. Mobile Worker Population to Reach 1.3 Billion by 2015: IDC, eWeek 3. Checkpoint Mobility Survey 2013. 4. Symantec Internet Security Threat Report, Volume 19 5. Express Metrix 2013 Software Audit Industry Report Copyright © 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, and the Checkmark Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. 21345035
