Symantec Solutions
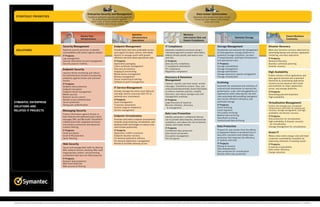
- 1. Enterprise Security and Management Data Center Optimization STRATEGIC PRIORITIES Transform enterprise security and management Optimize and modernize data center by protecting information against resources and reduce information more risks at more points with clear costs and risks visibility and strong control Optimize Minimize Secure Your Ensure Business Infrastructure Information Risk and Optimize Storage Infrastructure Continuity Operations Ensure Compliance Security Management pg 4 Endpoint Management pg 6 IT Compliance pg 4 Storage Management pg 4 Disaster Recovery pg 4 SOLUTIONS Optimize security processes to identify Provide faster and more predictable service Automate compliance processes using a Standardize and automate the management Meet your business recovery objectives by vulnerabilities and protect against attacks. and support of clients, servers, and mobile risk-based approach to protect information, of heterogeneous storage platforms to automating backup and recovery, application IT Projects: devices to manage assets with greater address threats quickly, and reduce costs maximize storage utilization, increase clustering, and data replication. Log management efficiency and drive down operational costs. and risks. IT responsiveness, and lower infrastructure IT Projects: Security information & event management IT Projects: IT Projects: and operational costs. Backup & Recovery Security posture visibility Application packaging Data security compliance IT Projects: Business continuity planning Client certificate management IT compliance automation Storage consolidation Disaster recovery Endpoint Security pg 4 Discovery & inventory PCI compliance Storage management Imaging & provisioning Regulatory compliance Storage optimization High Availability pg 4 Improve threat monitoring and reduce Mobile device management Storage resource & capacity management the administrative burden of protecting Protect mission-critical applications and Remote management Discovery & Retention Storage virtualization endpoints against known and unknown data against planned and unplanned Server monitoring & alerting Management pg 4 threats. downtime by automating application Software & patch management Archiving pg 4 IT Projects: Capture, classify, and store email, instant recovery across physical and virtual Endpoint data protection messages, SharePoint content, files, and Automate the movement and retention of environments on major application, IT Service Management pg 7 unstructured electronically stored information unstructured information to improve the server, and storage platforms. Endpoint encryption Endpoint threat management Actively manage the entire asset lifecycle to enforce retention policies, simplify performance, scale, and manageability of IT Projects: Mobile security and align service resources with ITIL to discovery, and reduce storage costs and applications while reducing the risk and Eliminating planned downtime Network access control optimize your investments. management overhead. costs associated with providing transparent High availability Remote access authentication IT Projects: IT Projects: user access, efficient e-discovery, and SYMANTEC ENTERPRISE Server protection Asset management Legal discovery & response optimized storage. Virtualization Management pg 4 Strong user authentication IT process automation Records retention, discovery, IT Projects: SOLUTIONS AND License usage & compliance & management Email archiving Protect and manage your virtualized infrastructure with tools for backup and RELATED IT PROJECTS Messaging Security pg 5 Service management Email migration recovery, storage management, and high Data Loss Prevention pg 5 File system archiving availability and disaster recovery. Protect information against threats in Endpoint Virtualization pg 7 Medical data archiving IT Projects: both inbound and outbound email, instant Identify and protect confidential informa- SharePoint archiving Data protection for virtualization messages (IM), and Microsoft® SharePoint® Provision and protect endpoint environments tion to prevent data breaches, demonstrate Unstructured data archiving High availability & disaster recovery collaboration with integrated antispam instantly using streaming, virtualization, and compliance, and reduce the risk of external and antivirus protection and advanced desktop broker technologies to reduce costs attacks and insider threats. for virtualization content filtering. and increase productivity. Data Protection Storage management for virtualization IT Projects: IT Projects: IT Projects: Confidential data protection Prepare for and recover from the effects Email encryption Application conflict resolution Data breach prevention of equipment failure or accidental loss of Green IT pg 4 Email & IM protection Endpoint disaster recovery Encryption management data with consistent and reliable data Reduce data center energy costs and meet Spam blocking On-demand application delivery File encryption protection that improves the efficiency corporate sustainability mandates by On-demand application management of systems and staff. improving utilization of existing assets. Web Security pg 5 Remote & portable desktop access IT Projects: IT Projects: Backup & recovery Corporate sustainability Secure and manage Web traffic by filtering Data deduplication Data center efficiency Web malware threats, blocking URLs with Data protection for virtualization Energy reduction inappropriate content, and preventing Remote office data protection confidential data loss over Web protocols. IT Projects: Network data protection Web fraud detection Web security & filtering Copyright © 2011 Symantec Corporation. All rights reserved. Symantec and the Symantec Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. VeriSign is a registered trademark of VeriSign, Inc. Domino is a registered trademark of IBM Corporation. Microsoft and SharePoint are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Other names may be trademarks of their respective owners. 12/10 14104463-4
- 2. Enterprise Security and Management Data Center Optimization STRATEGIC PRIORITIES Transform enterprise security and management Optimize and modernize data center by protecting information against resources and reduce information more risks at more points with clear costs and risks visibility and strong control Optimize Minimize Secure Your Ensure Business Infrastructure Information Risk and Optimize Storage Infrastructure Continuity Operations Ensure Compliance Security Management pg 4 Endpoint Management pg 6 IT Compliance pg 4 Storage Management pg 4 Disaster Recovery pg 4 SOLUTIONS Control Compliance Suite Altiris™ Client Management Suite Control Compliance Suite Veritas CommandCentral™ Storage Backup Exec Protection Center Altiris Deployment Solution Critical System Protection Veritas CommandCentral Storage Change Backup Exec System Recovery Security Information Manager Altiris IT Management Suite Data Loss Prevention Manager NetBackup DeepSight™ Early Warning Services Altiris Server Management Suite Enterprise Vault™ Veritas Storage Foundation™ NetBackup Appliances Managed Security Services Mobile Management MessageLabs Hosted Email Archiving Veritas Storage Foundation Cluster File NetBackup RealTime Security Consulting Services Wise Package Studio™ Protection Suites System Symantec Health Safe Security Consulting Services Security Information Manager Veritas Storage Foundation Scalable File Veritas CommandCentral Disaster Endpoint Security pg 4 VeriSign Public Key Infrastructure Services Workflow Server Recovery Advisor Managed Security Services Storage and Availability Consulting Services Veritas™ Cluster Server Critical System Protection IT Service Management pg 6 Security Consulting Services Veritas Storage Foundation Endpoint Encryption Archiving pg 4 Veritas Volume Replicator Endpoint Protection Altiris IT Management Suite Discovery & Retention Information Management Consulting Endpoint Protection Mobile ServiceDesk Enterprise Vault Management pg 4 Services Hosted Endpoint Protection Workflow MessageLabs Hosted Email Archiving Storage and Availability Consulting Network Access Control Enterprise Vault Symantec Health Safe Services Protection Suites Endpoint Virtualization pg 7 Enterprise Vault Discovery Collector Information Management Consulting Managed Security Services Information Management Consulting Services Endpoint Virtualization Suite High Availability pg 4 Security Consulting Services Services Workspace Corporate/Remote Data Protection pg 5 VeriSign™ Identity Protection Authentication MessageLabs Hosted Email Continuity Workspace Streaming Backup Exec™ Service Data Loss Prevention pg 5 Veritas Cluster Server SYMANTEC ENTERPRISE Workspace Virtualization Backup Exec System Recovery Veritas Cluster Server One Critical Systems Protection Enterprise Vault Veritas CommandCentral Disaster SOLUTIONS: SOFTWARE, Messaging Security pg 5 Data Loss Prevention for Endpoint NetBackup™ Recovery Advisor APPLIANCES, AND Email Encryption Data Loss Prevention for Network NetBackup Appliances NetBackup RealTime Veritas Storage Foundation IM Manager Data Loss Prevention for Storage Veritas Storage Foundation Cluster File SERVICES MessageLabs™ Hosted Email Security Encryption Management Online Backup System MessageLabs Hosted Instant Messaging OpsCenter Analytics Endpoint Encryption Veritas Volume Replicator Protection Suites Security Enterprise Vault Information Management Consulting Storage and Availability Consulting Services Messaging Gateway File Encryption Services Mail Security for Domino® MessageLabs Hosted Email Encryption Managed Backup Services Mail Security for Microsoft® Exchange Protection Suites Virtualization Management pg 4 Protection for SharePoint Servers Security Consulting Services Backup Exec Protection Suites Backup Exec System Recovery Traffic Shaper NetBackup Security Consulting Services NetBackup Appliances Veritas Cluster Server Web Security pg 5 Veritas CommandCentral Storage Veritas Storage Foundation Data Loss Prevention for Network Information Management Consulting MessageLabs Hosted Web Security Services Protection Suites Storage and Availability Consulting Web Gateway Services Managed Security Services Security Consulting Services VeriSign Identity Protection Fraud Green IT pg 4 Detection Service Altiris Client Management Suite Altiris Server Management Suite Enterprise Vault Endpoint Virtualization Suite NetBackup Veritas Cluster Server Veritas CommandCentral Storage Veritas Storage Foundation All solutions include Education Services, Enterprise Support Services, and Business Critical Services.