Functional Safety and Security process alignment
•Download as PPTX, PDF•
3 likes•599 views
This document discusses security and safety requirements for Intel systems. It describes performing threat analysis and risk assessment (TARA) along with hazard analysis and risk assessment (HARA) to define security and safety goals. Additionally, it proposes adding security mechanisms such as checking for file tampering and application trust when monitoring graphics systems to protect against threats.
Report
Share
Report
Share
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Dragos S4x20: How to Build an OT Security Operations Center

Dragos S4x20: How to Build an OT Security Operations Center
Equivalences and diffrences between SysML and Arcadia / Capella

Equivalences and diffrences between SysML and Arcadia / Capella
ISO Automotive,SAE 21434 Training, Road Vehicles Cybersecurity Engineering

ISO Automotive,SAE 21434 Training, Road Vehicles Cybersecurity Engineering
Frequently Asked Question (FAQ's) on ISO 26262 Functional Safety

Frequently Asked Question (FAQ's) on ISO 26262 Functional Safety
ISO 26262 Unit Testing | Functional Safety in Automotive 

ISO 26262 Unit Testing | Functional Safety in Automotive
Similar to Functional Safety and Security process alignment
Similar to Functional Safety and Security process alignment (20)
Automated Interpretation and Integration of Security Tools Using Semantic Kno...

Automated Interpretation and Integration of Security Tools Using Semantic Kno...
Architecture-centric Support for Integrating Security Tool in a Security Orch...

Architecture-centric Support for Integrating Security Tool in a Security Orch...
ОЛЬГА АКСЬОНЕНКО «Безпечна розробка програмного забезпечення в Agile проектах...

ОЛЬГА АКСЬОНЕНКО «Безпечна розробка програмного забезпечення в Agile проектах...
Security Testing Report Hitachi Application Q1 Sep 2015

Security Testing Report Hitachi Application Q1 Sep 2015
INTERFACE by apidays 2023 - Security Exposure Management in API First World, ...

INTERFACE by apidays 2023 - Security Exposure Management in API First World, ...
Chapter 4 - Quality Characteristics for Technical Testing

Chapter 4 - Quality Characteristics for Technical Testing
SOURCE CODE ANALYSIS TO REMOVE SECURITY VULNERABILITIES IN JAVA SOCKET PROGR...

SOURCE CODE ANALYSIS TO REMOVE SECURITY VULNERABILITIES IN JAVA SOCKET PROGR...
More from Alan Tatourian
More from Alan Tatourian (9)
Systems architecture with the functional safety/security emphasis

Systems architecture with the functional safety/security emphasis
Securing future connected vehicles and infrastructure

Securing future connected vehicles and infrastructure
Recently uploaded
Mtp kit in kuwait௹+918133066128....) @abortion pills for sale in Kuwait City ✒Abortion CLINIC In Kuwait ?Kuwait pills +918133066128௵) safe Abortion Pills for sale in Salmiya, Kuwait city,Farwaniya-cytotec pills for sale in Kuwait city. Kuwait pills +918133066128WHERE I CAN BUY ABORTION PILLS IN KUWAIT, CYTOTEC 200MG PILLS AVAILABLE IN KUWAIT, MIFEPRISTONE & MISOPROSTOL MTP KIT FOR SALE IN KUWAIT. Whatsapp:+Abortion Pills For Sale In Mahboula-abortion pills in Mahboula-abortion pills in Kuwait City- .Kuwait pills +918133066128)))abortion pills for sale in Mahboula …Mtp Kit On Sale Kuwait pills +918133066128mifepristone Tablets available in Kuwait?Zahra Kuwait pills +918133066128Buy Abortion Pills Cytotec Misoprostol 200mcg Pills Brances and now offering services in Sharjah, Abu Dhabi, Dubai, **))))Abortion Pills For Sale In Ras Al-Khaimah(((online Cytotec Available In Al Madam))) Cytotec Available In muscat, Cytotec 200 Mcg In Zayed City, hatta,Cytotec Pills௵+ __}Kuwait pills +918133066128}— ABORTION IN UAE (DUBAI, SHARJAH, AJMAN, UMM AL QUWAIN, ...UAE-ABORTION PILLS AVAILABLE IN DUBAI/ABUDHABI-where can i buy abortion pillsCytotec Pills௵+ __}Kuwait pills +918133066128}}}/Where can I buy abortion pills in KUWAIT , KUWAIT CITY, HAWALLY, KUWAIT, AL JAHRA, MANGAF , AHMADI, FAHAHEEL, In KUWAIT ... pills for sale in dubai mall and where anyone can buy abortion pills in Abu Dhabi, Dubai, Sharjah, Ajman, Umm Al Quwain, Ras Al Khaimah ... Abortion pills in Dubai, Abu Dhabi, Sharjah, Ajman, Fujairah, Ras Al Khaimah, Umm Al Quwain…Buy Mifepristone and Misoprostol Cytotec , Mtp KitABORTION PILLS _ABORTION PILLS FOR SALE IN ABU DHABI, DUBAI, AJMAN, FUJUIRAH, RAS AL KHAIMAH, SHARJAH & UMM AL QUWAIN, UAE ❤ Medical Abortion pills in ... ABU DHABI, ABORTION PILLS FOR SALE ----- Dubai, Sharjah, Abu dhabi, Ajman, Alain, Fujairah, Ras Al Khaimah FUJAIRAH, AL AIN, RAS AL KHAIMAMedical Abortion pills in Dubai, Abu Dhabi, Sharjah, Al Ain, Ajman, RAK City, Ras Al Khaimah, Fujairah, Dubai, Qatar, Bahrain, Saudi Arabia, Oman, ...Where I Can Buy Abortion Pills In Al ain where can i buy abortion pills in #Dubai, Exclusive Abortion pills for sale in Dubai ... Abortion Pills For Sale In Rak City, in Doha, Kuwait.௵ Kuwait pills +918133066128₩ Abortion Pills For Sale In Doha, Kuwait,CYTOTEC PILLS AVAILABLE Abortion in Doha, ꧁ @ ꧂ ☆ Abortion Pills For Sale In Ivory park,Rabie Ridge,Phomolong. ] Abortion Pills For Sale In Ivory Park, Abortion Pills+918133066128In Ivory Park, Abortion Clinic In Ivory Park,Termination Pills In Ivory Park,. *)][(Abortion Pills For Sale In Tembisa Winnie Mandela Ivory Park Ebony Park Esangweni Oakmoor Swazi Inn Whats'app...In Ra al Khaimah,safe termination pills for sale in Ras Al Khaimah. | Dubai.. @Kuwait pills +918133066128Abortion Pills For Sale In Kuwait, Buy Cytotec Pills In Kuwait.Cytotec Pills௵ __}Kuwait pills +918133066128}}}/Where can I buy abortion pills in KUWAIT ,Abortion pills Dubai (+918133066128) Cytotec 200mg pills UAE Abudhabi

Abortion pills Dubai (+918133066128) Cytotec 200mg pills UAE AbudhabiAbortion pills in Kuwait Cytotec pills in Kuwait
Faridabad Call Girls ₹7.5k Pick Up & Drop With Cash Payment 8168257667 Call Girls
Booking Contact Details
WhatsApp Chat: +91-8168257667
Normal Call : +91-8168257667
Faridabad Call Girls includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant;$S2 making an impressionable.
Faridabad Call Girls understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together.
We provide -
Flexibility
Choices and options
Lists of many beauty fantasies
Turn your dream into reality
Perfect companionship
Cheap and convenient
In-call and Out-call services
And many more.Faridabad Call Girls ₹7.5k Pick Up & Drop With Cash Payment 8168257667 Call G...

Faridabad Call Girls ₹7.5k Pick Up & Drop With Cash Payment 8168257667 Call G...Hyderabad Escorts Agency
Recently uploaded (20)
Is Your BMW PDC Malfunctioning Discover How to Easily Reset It

Is Your BMW PDC Malfunctioning Discover How to Easily Reset It
Top profile Call Girls In dharamshala [ 7014168258 ] Call Me For Genuine Mode...![Top profile Call Girls In dharamshala [ 7014168258 ] Call Me For Genuine Mode...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Top profile Call Girls In dharamshala [ 7014168258 ] Call Me For Genuine Mode...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Top profile Call Girls In dharamshala [ 7014168258 ] Call Me For Genuine Mode...
Abortion pills Dubai (+918133066128) Cytotec 200mg pills UAE Abudhabi

Abortion pills Dubai (+918133066128) Cytotec 200mg pills UAE Abudhabi
Stacey+= Dubai Calls Girls O525547819 Call Girls In Dubai

Stacey+= Dubai Calls Girls O525547819 Call Girls In Dubai
Faridabad Call Girls ₹7.5k Pick Up & Drop With Cash Payment 8168257667 Call G...

Faridabad Call Girls ₹7.5k Pick Up & Drop With Cash Payment 8168257667 Call G...
Top profile Call Girls In dewas [ 7014168258 ] Call Me For Genuine Models We ...![Top profile Call Girls In dewas [ 7014168258 ] Call Me For Genuine Models We ...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Top profile Call Girls In dewas [ 7014168258 ] Call Me For Genuine Models We ...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Top profile Call Girls In dewas [ 7014168258 ] Call Me For Genuine Models We ...
Top profile Call Girls In Ranchi [ 7014168258 ] Call Me For Genuine Models We...![Top profile Call Girls In Ranchi [ 7014168258 ] Call Me For Genuine Models We...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Top profile Call Girls In Ranchi [ 7014168258 ] Call Me For Genuine Models We...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Top profile Call Girls In Ranchi [ 7014168258 ] Call Me For Genuine Models We...
T.L.E 5S's (Seiri, Seiton, Seiso, Seiketsu, Shitsuke).pptx

T.L.E 5S's (Seiri, Seiton, Seiso, Seiketsu, Shitsuke).pptx
John Deere Tractors 5415 Diagnostic Repair Service Manual.pdf

John Deere Tractors 5415 Diagnostic Repair Service Manual.pdf
What Does The Engine Malfunction Reduced Power Message Mean For Your BMW X5

What Does The Engine Malfunction Reduced Power Message Mean For Your BMW X5
Functional Safety and Security process alignment
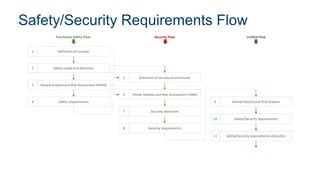
- 1. Intel Confidential 1 Safety/Security Requirements Flow Definition of security environment5 Threat Analysis and Risk Assessment (TARA)6 Security requirements8 Overall Hazard and Risk Analysis9 Safety/Security requirements10 Safety/Security requirements allocation11 Security objectives7 Definition of concept1 Safety scope and definition2 Hazard Analysis and Risk Assessment (HARA)3 Safety requirements4 Functional Safety Flow Security Flow Unified Flow
- 2. Intel Confidential 2 HARA and TARA Done Together Threat Security Goal AssetOwner Attacker Malicious Action Attack Potential Point of Attack with regard to with risk of has a value for has for execution of reduced by performed at TARA HARA Define the safety item Determine features to realize safety item Determine malfunctions of functions Determine operational scenarios Identify possible hazards (effects) Evaluate the ASIL and determine the safety goals
- 3. Intel Confidential 3 Mixed-Criticality Cluster
- 4. Intel Confidential 4 Graphics Fail-Safe Step By Step 1. Monitor parses configuration file for checking criteria 2. Cluster app requests Screen to display a symbol 3. Cluster app requests Monitor to check the rendered symbol 4. Monitor retrieves the framebuffer from Screen 5. Monitor performs checking according to criteria from (1) 6. Monitor notifies the cluster app of the checking results 7. Cluster app decides the course of action
- 5. Intel Confidential 5 Security Mechanism to Protect Graphics 1. Monitor parses configuration file for checking criteria (Was the file tampered with? Is the monitor trusted?) 2. Cluster app requests Screen to display a symbol (Does the application run in a trusted sandbox? Is the application trusted?) 3. Cluster app requests Monitor to check the rendered symbol 4. Monitor retrieves the framebuffer from Screen 5. Monitor performs checking according to criteria from (1) 6. Monitor notifies the cluster app of the checking results 7. Cluster app decides the course of action Does the application trust the message? Was the configuration file tampered? Is the application trusted? Is the monitor trusted?
