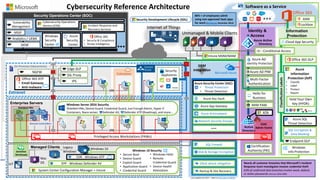
cyber-security-reference-architecture
- 1. Internet of Things Unmanaged & Mobile Clients Sensitive Workloads Cybersecurity Reference Architecture Extranet Azure Key Vault Microsoft Azure On Premises Datacenter(s) NGFW Nearly all customer breaches that Microsoft’s Incident Response team investigates involve credential theft 63% of confirmed data breaches involve weak, default, or stolen passwords (Verizon 2016 DBR) Colocation $ Mac OS Multi-Factor Authentication MIM PAM Network Security Groups Azure AD PIM Windows Info Protection Enterprise Servers VPN VPN VMs VMs Certification Authority (PKI) Security Operations Center (SOC) WEF SIEM Integration IoT Identity & Access Windows 10Managed Clients Software as a Service ATA Azure Information Protection (AIP) • Classify • Label • Protect • Report Endpoint DLP ClassificationLabels Office 365 Information Protection Legacy Windows Hold Your Own Key (HYOK) 80% + of employees admit using non-approved SaaS apps for work (Stratecast, December 2013) IPS Edge DLP SSL Proxy Azure AD Identity Protection Security Appliances Last updated July 2017 – latest at http://aka.ms/MCRA EPP - Windows Defender AV EDR - Windows ATP Azure SQL Threat Detection Windows Server 2016 Security Shielded VMs, Device Guard, Credential Guard, Just Enough Admin, Hyper-V Containers, Nano server, Defender AV, Defender ATP (Roadmap), and more… Azure App Gateway Azure Antimalware SQL Encryption & Data Masking SQL Firewall Disk & Storage Encryption Conditional Access Office 365 ATP • Email Gateway • Anti-malware • Threat Protection • Threat Detection Azure Security Center (ASC) Analytics / UEBA MSSP Windows Security Center Azure Security Center Vulnerability Management SIEM Office 365 • Security & Compliance • Threat Intelligence Hello for Business Windows 10 Security • Secure Boot • Device Guard • Exploit Guard • Application Guard • Credential Guard • Windows Hello • Remote Credential Guard • Device Health Attestation Security Development Lifecycle (SDL) Cybersecurity Operations Service (COS) Incident Response and Recovery Services Office 365 DLP Cloud App Security Lockbox ASM Intune MDM/MAM DDoS attack mitigation Backup & Site RecoverySystem Center Configuration Manager + Intune Privileged Access Workstations (PAWs) Shielded VMs ESAE Admin Forest Domain Controllers
- 2. Cybersecurity Reference Architecture Mark Simos Sachin Gupta Enterprise Cybersecurity Group
- 3. Active Threat Detection Software as a Service Office 365 Unmanaged & Mobile Clients Sensitive Workloads Cybersecurity Reference Architecture Intranet Extranet On Premises Datacenter(s) IPS DLP SSL Proxy $ Windows 10 NGFW Mac OS Enterprise Servers Domain Controllers VMs VMs Certification Authority (PKI) Incident Response Vulnerability Management Analytics Managed Security Provider SIEM Security Operations Center (SOC) Logs & Analytics Hunting Teams IoT Identity & AccessUEBA Managed Clients Legacy Windows Information Protection Endpoint DLP Components • Network Edge Defenses • Operations, Identity, & Info Protection Functions • Enterprise Servers & VMs • SaaS adoption (sanctioned or Shadow IT) • Identity Systems including Active Directory • Mix of managed & unmanaged devices • Endpoint and Edge DLP • Highly Sensitive Assets • SIEM & Analytics • Advanced Detection & Response
- 4. SECURE MODERN ENTERPRISE Identity Apps and Data Infrastructure Devices Identity Embraces identity as primary security perimeter and protects identity systems, admins, and credentials as top priorities Apps and Data Aligns security investments with business priorities including identifying and securing communications, data, and applications Infrastructure Operates on modern platform and uses cloud intelligence to detect and remediate both vulnerabilities and attacks Devices Accesses assets from trusted devices with hardware security assurances, great user experience, and advanced threat detectionSecure Platform (secure by design)
- 5. Secure Platform (secure by design) SECURE MODERN ENTERPRISE Identity Apps and Data Infrastructure Devices Secure the Pillars Build the Security Foundation Start the journey by getting in front of current attacks • Critical Mitigations – Critical attack protections • Attack Detection – Hunt for hidden persistent adversaries and implement critical attack detection • Roadmap and planning – Share Microsoft insight on current attacks and strategies, build a tailored roadmap to defend your organization’s business value and mission Build Security Foundation – Critical Attack Defenses Secure the Pillars Continue building a secure modern enterprise by adopting leading edge technology and approaches: • Threat Detection – Integrate leading edge intelligence and Managed detection and response (MDR) capabilities • Identity and Access Management – continue reducing risk to business critical identities and assets • Information Protection– Discover, protect, and monitor your critical data • Cloud Adoption – Chart a secure path into a cloud- enabled enterprise • Device & Datacenter Security – Hardware protections for Devices, Credentials, Servers, and Applications • App/Dev Security – Secure your development practices and digital transformation components http://aka.ms/SPARoadmap
- 6. Active Threat Detection Software as a Service Office 365 Unmanaged & Mobile Clients Sensitive Workloads Cybersecurity Reference Architecture Intranet Extranet On Premises Datacenter(s) IPS DLP SSL Proxy $ Windows 10 NGFW Mac OS Enterprise Servers Domain Controllers VMs VMs Certification Authority (PKI) Incident Response Vulnerability Management Analytics Managed Security Provider SIEM Security Operations Center (SOC) Logs & Analytics Hunting Teams IoT Identity & AccessUEBA Managed Clients Legacy Windows Information Protection Endpoint DLP Major Incident Credential Theft Mitigations Prevention • Privileged Access Workstations • Administrative Forest (ESAE) • Privileged Access Management Detection • Advanced Threat Analytics • ETD Managed Detection and Response (MDR) Response • Incident Response MIM PAM Enterprise Threat Detection Investigation and Recovery ATA ATA Nearly all customer breaches that Microsoft’s Incident Response team investigates involve credential theft 63% of confirmed data breaches involve weak, default, or stolen passwords (Verizon 2016 DBR) Privileged Access Workstations Admin Forest
- 7. Approved Cloud Services Office 365 Network Perimeter Unmanaged Devices Threats Persistent • Network perimeter repels and detects classic attacks …but is reliably defeated by • Phishing • Credential theft • Data has moved out of the network and its protections • You must establish an Identity security perimeter • Strong Authentication • Monitoring and enforcement of access policies • Threat monitoring using telemetry & intelligence Resources $ $ $ $$ $ $ $ $ $ $ Identity Perimeter Shadow IT
- 8. Devices Apps Infrastructure Data Identity Unprotected Sensitive Data Unmanaged Devices Risky Use of Approved SaaS Apps Shadow IT SaaS Applications Phishing Credential Theft & Abuse
- 9. MIM PAM Enterprise Threat Detection Investigation and Recovery ATA Privileged Access Workstations Admin Forest Challenges • Phishing reliably gains foothold in environment • Credential Theft allows traversal within environment Microsoft Approach • Time of click (vs. time of send) protection and attachment detonation • Integrated Intelligence, Reporting, Policy enforcement • Securing Privileged Access (SPA) roadmap to protect Active Directory and existing infrastructure Identity Phishing Credential Theft & Abuse Office 365 ATP • Email Gateway • Anti-malware Azure AD Identity Protection Conditional Access Advanced Threat Analytics
- 10. Internet of Things Unmanaged & Mobile Clients Sensitive Workloads Cybersecurity Reference Architecture Extranet Azure Key Vault Azure Security Center • Threat Protection • Threat Detection Microsoft Azure On Premises Datacenter(s) NGFW Nearly all customer breaches that Microsoft’s Incident Response team investigates involve credential theft 63% of confirmed data breaches involve weak, default, or stolen passwords (Verizon 2016 DBR) Colocation $ Mac OS Multi-Factor Authentication MIM PAMAzure App Gateway Network Security Groups Azure AD PIM Azure Antimalware Disk & Storage Encryption SQL Encryption & Firewall Hello for Business Enterprise Servers VPN VPN VMs VMs Certification Authority (PKI) Incident Response Vulnerability Management Enterprise Threat Detection Analytics Managed Security Provider OMS ATA SIEM Security Operations Center (SOC) Logs & Analytics Active Threat Detection Hunting Teams Investigation and Recovery WEF SIEM Integration IoT Identity & AccessUEBA Windows 10Managed Clients Software as a Service ATA Privileged Access Workstations (PAWs) Endpoint DLP DDoS attack mitigation Office 365 Information Protection Legacy Windows Backup and Site Recovery Domain Controllers Office 365 ATP • Email Gateway • Anti-malware ESAE Admin Forest PADS 80% + of employees admit using non-approved SaaS apps for work (Stratecast, December 2013) IPS Edge DLP SSL Proxy Security Development Lifecycle (SDL) Azure AD Identity Protection Security Appliances
- 11. Apps Phishing Theft se Shadow IT SaaS Applications Challenges • Shadow IT - Unsanctioned cloud services storing and processing your sensitive data • SaaS Management – Challenging to consistently manage many Software as a Service (SaaS) Microsoft Approach Enable Full Security Lifecycle 1. Discover SaaS Usage 2. Investigate current risk posture 3. Take Control to enforce policy on SaaS tenants and data 4. Alert and take automatic action on policy violations (e.g. remove public access to sensitive document) Cloud App Security Risky Use of Approved SaaS Apps
- 12. Internet of Things Unmanaged & Mobile Clients Sensitive Workloads Cybersecurity Reference Architecture Extranet Azure Key Vault Azure Security Center • Threat Protection • Threat Detection Microsoft Azure On Premises Datacenter(s) NGFW Nearly all customer breaches that Microsoft’s Incident Response team investigates involve credential theft 63% of confirmed data breaches involve weak, default, or stolen passwords (Verizon 2016 DBR) Colocation $ Mac OS Multi-Factor Authentication MIM PAMAzure App Gateway Network Security Groups Azure AD PIM Azure Antimalware Disk & Storage Encryption SQL Encryption & Firewall Hello for Business Enterprise Servers VPN VPN VMs VMs Certification Authority (PKI) Incident Response Vulnerability Management Enterprise Threat Detection Analytics Managed Security Provider OMS ATA SIEM Security Operations Center (SOC) Logs & Analytics Active Threat Detection Hunting Teams Investigation and Recovery WEF SIEM Integration IoT Identity & AccessUEBA Windows 10Managed Clients Software as a Service ATA Privileged Access Workstations (PAWs) Endpoint DLP DDoS attack mitigation Office 365 Information Protection Legacy Windows Backup and Site Recovery Domain Controllers Office 365 ATP • Email Gateway • Anti-malware ESAE Admin Forest PADS 80% + of employees admit using non-approved SaaS apps for work (Stratecast, December 2013) IPS Edge DLP SSL Proxy Security Development Lifecycle (SDL) Azure AD Identity Protection Security Appliances Cloud App Security
- 13. Data Unprotected Sensitive Data Credential Theft & Abuse Challenges • Limited visibility and control of sensitive data • Data classification is large and challenging project Microsoft Approach • Protect data anywhere it goes • Bring or Hold your own Key • Support most popular formats • Integration with Existing DLP Azure Information Protection (AIP) • Classify • Label • Protect • Report ClassificationLabels Hold Your Own Key (HYOK) Endpoint DLP Edge DLP
- 14. Internet of Things Unmanaged & Mobile Clients Sensitive Workloads Cybersecurity Reference Architecture Extranet Azure Key Vault Azure Security Center • Threat Protection • Threat Detection Microsoft Azure On Premises Datacenter(s) NGFW Nearly all customer breaches that Microsoft’s Incident Response team investigates involve credential theft 63% of confirmed data breaches involve weak, default, or stolen passwords (Verizon 2016 DBR) Colocation $ Mac OS Multi-Factor Authentication MIM PAMAzure App Gateway Network Security Groups Azure AD PIM Azure Antimalware Disk & Storage Encryption SQL Encryption & Firewall Hello for Business Enterprise Servers VPN VPN VMs VMs Certification Authority (PKI) Incident Response Vulnerability Management Enterprise Threat Detection Analytics Managed Security Provider OMS ATA SIEM Security Operations Center (SOC) Logs & Analytics Active Threat Detection Hunting Teams Investigation and Recovery WEF SIEM Integration IoT Identity & AccessUEBA Windows 10Managed Clients Software as a Service ATA Privileged Access Workstations (PAWs) Conditional Access Cloud App Security Azure Information Protection (AIP) • Classify • Label • Protect • Report Office 365 DLP Endpoint DLP Structured Data & 3rd party Apps DDoS attack mitigation ClassificationLabels ASM Lockbox Office 365 Information Protection Legacy Windows Backup and Site Recovery Domain Controllers Office 365 ATP • Email Gateway • Anti-malware Hold Your Own Key (HYOK) ESAE Admin Forest PADS 80% + of employees admit using non-approved SaaS apps for work (Stratecast, December 2013) IPS Edge DLP SSL Proxy Security Development Lifecycle (SDL) Azure AD Identity Protection Security Appliances
- 15. Microsoft Approach • Provide a great user experience, strong Hardware- based security, and advanced detection + response capabilities • Mobile Device Management and Mobile App Management of popular devices via Intune • Policy enforcement via Conditional Access Devices Unmanaged Devices Challenges • Provide secure PCs and devices for sensitive data • Manage & protect data on non-corporate devices Intune MDM/MAM Conditional Access Windows 10
- 16. Internet of Things Unmanaged & Mobile Clients Sensitive Workloads Cybersecurity Reference Architecture Extranet Azure Key Vault Azure Security Center • Threat Protection • Threat Detection Microsoft Azure On Premises Datacenter(s) NGFW Nearly all customer breaches that Microsoft’s Incident Response team investigates involve credential theft 63% of confirmed data breaches involve weak, default, or stolen passwords (Verizon 2016 DBR) Colocation $ Mac OS Multi-Factor Authentication MIM PAMAzure App Gateway Network Security Groups Azure AD PIM Azure Antimalware Disk & Storage Encryption SQL Encryption & Firewall Hello for Business Enterprise Servers VPN VPN VMs VMs Certification Authority (PKI) Incident Response Vulnerability Management Enterprise Threat Detection Analytics Managed Security Provider OMS ATA SIEM Security Operations Center (SOC) Logs & Analytics Active Threat Detection Hunting Teams Investigation and Recovery WEF SIEM Integration IoT Identity & AccessUEBA Windows 10Managed Clients Software as a Service ATA Privileged Access Workstations (PAWs) Intune MDM/MAM Conditional Access Cloud App Security Azure Information Protection (AIP) • Classify • Label • Protect • Report Office 365 DLP Endpoint DLP Structured Data & 3rd party Apps DDoS attack mitigation ClassificationLabels ASM Lockbox Office 365 Information Protection Legacy Windows Backup and Site Recovery Domain Controllers Office 365 ATP • Email Gateway • Anti-malware Hold Your Own Key (HYOK) ESAE Admin Forest PADS 80% + of employees admit using non-approved SaaS apps for work (Stratecast, December 2013) IPS Edge DLP SSL Proxy Security Development Lifecycle (SDL) Azure AD Identity Protection Security Appliances
- 17. Powered by the Intelligent Security Graph Professional Services Information Identity Cloud Infrastructure Private Cloud & On- Premises Infrastructure Microsoft Threat Detection Deep insight across your environment Azure Security Center • Threat Protection • Threat Detection EDR - Windows Defender ATP Enterprise Threat Detection OMS ATA Investigation and Recovery Cloud App Security Office 365 ATP • Email Gateway • Anti-malware PADS Detect Threats with managed detection and response (MDR) service Hunt for threats and persistent adversaries in your environment Respond to Threats with seasoned professionals and deep expertise Operations Management Suite Azure AD Identity Protection Advanced Threat Analytics SIEM Security Appliances
- 18. Internet of Things Unmanaged & Mobile Clients Sensitive Workloads Cybersecurity Reference Architecture Extranet Azure Key Vault Azure Security Center • Threat Protection • Threat Detection System Center Configuration Manager + Intune Microsoft Azure On Premises Datacenter(s) NGFW Nearly all customer breaches that Microsoft’s Incident Response team investigates involve credential theft 63% of confirmed data breaches involve weak, default, or stolen passwords (Verizon 2016 DBR) Colocation $ EPP - Windows Defender EDR - Windows Defender ATPMac OS Multi-Factor Authentication MIM PAMAzure App Gateway Network Security Groups Azure AD PIM Azure Antimalware Disk & Storage Encryption SQL Encryption & Firewall Hello for Business Windows Info Protection Enterprise Servers VPN VPN VMs VMs Certification Authority (PKI) Incident Response Vulnerability Management Enterprise Threat Detection Analytics Managed Security Provider OMS ATA SIEM Security Operations Center (SOC) Logs & Analytics Active Threat Detection Hunting Teams Investigation and Recovery WEF SIEM Integration IoT Identity & AccessUEBA Windows 10 Windows 10 Security • Secure Boot • Device Guard • Application Guard • Credential Guard • Windows Hello Managed Clients Windows Server 2016 Security Shielded VMs, Device Guard, Credential Guard, Just Enough Admin, Hyper-V Containers, Nano server, … Software as a Service ATA Privileged Access Workstations (PAWs) • Device Health Attestation • Remote Credential Guard Intune MDM/MAM Conditional Access Cloud App Security Azure Information Protection (AIP) • Classify • Label • Protect • Report Office 365 DLP Endpoint DLP Structured Data & 3rd party Apps DDoS attack mitigation ClassificationLabels ASM Lockbox Office 365 Information Protection Legacy Windows Backup and Site Recovery Shielded VMs Domain Controllers Office 365 ATP • Email Gateway • Anti-malware Hold Your Own Key (HYOK) ESAE Admin Forest PADS 80% + of employees admit using non-approved SaaS apps for work (Stratecast, December 2013) IPS Edge DLP SSL Proxy Security Development Lifecycle (SDL) Azure AD Identity Protection Security Appliances • Hover over each item in presentation mode to see description • Click to go to a webpage
- 19. Business Critical Workloads Cybersecurity Reference Architecture Extranet Microsoft Azure On Premises Datacenter(s) Nearly all customer breaches involve credential theft (Microsoft Incident Response team) Colocation $ Enterprise Servers Security Operations Center (SOC) Identity & Access Managed Clients Legacy Windows Privileged Access Workstations (PAWs) Data Protection Full Lifecycle Protections (Classify, Protect, Report, Revoke) Critical Formats DLP integration Office 365 Information Protection Advanced Email Protection Partnerships • Firewall, Proxy • Data Loss Prevention (DLP) • Intrusion Prevention (IPS) Advanced Threat Protection and Detection Analytics & Reporting Conditional Access Multi-factor Authentication Privileged Access Management …and more Windows 10 Security • Hardware based protections • Powerful detection and investigation capabilities Mac OS Built-in Security Protection from DDoS, Disasters, & Ransomware Compliance Internet Facing Workloads Security Appliances Threat Protection and Monitoring • Incident Response and Recovery Services • Visibility across your enterprise assets • Integration with your existing SIEM Datacenter and Virtualization Security Critical Protections for Privileged Identities | Private Cloud Fabric | Workloads Internet of Things Unmanaged & Mobile Clients Mobile Device & App Management (MDM/MAM) Discover & Secure SaaS usage Last updated March 2017 – latest at http://aka.ms/MCRA
Notas del editor
- Key Takeaway: This is the Cybersecurity Reference architecture we built to illustrate the broad set of capabilities that help our customers secure their modern enterprise. Note that this slide has links to more information for each capability. Just put it in presentation mode and hover over them to see a brief description and click for more information.