Vulnerability Scans & Penetration Test Comparison Chart
•
0 likes•1,042 views
Are you 100 percent sure you understand the difference between vulnerability scans and penetration tests? Learn the specific variations here from I.S. Partners, LLC!
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
Enterprise Vulnerability Management: Back to Basics

Enterprise Vulnerability Management: Back to Basics
Mapping the Enterprise Threat, Risk, and Security Control Landscape with Splunk

Mapping the Enterprise Threat, Risk, and Security Control Landscape with Splunk
Enterprise IT Security Audit | Cyber Security Services

Enterprise IT Security Audit | Cyber Security Services
The Critical Security Controls and the StealthWatch System

The Critical Security Controls and the StealthWatch System
What We’ve Learned Building a Cyber Security Operation Center: du Case Study

What We’ve Learned Building a Cyber Security Operation Center: du Case Study
Similar to Vulnerability Scans & Penetration Test Comparison Chart
Similar to Vulnerability Scans & Penetration Test Comparison Chart (20)
(VAPT) Vulnerability Assessment And Penetration Testing

(VAPT) Vulnerability Assessment And Penetration Testing
SynerComm's Tech TV series CIS Top 20 Critical Security Controls #4

SynerComm's Tech TV series CIS Top 20 Critical Security Controls #4
Application Portfolio Risk Ranking: Banishing FUD With Structure and Numbers

Application Portfolio Risk Ranking: Banishing FUD With Structure and Numbers
What is penetration testing and why is it important for a business to invest ...

What is penetration testing and why is it important for a business to invest ...
AlienVault MSSP Overview - A Different Approach to Security for MSSP's

AlienVault MSSP Overview - A Different Approach to Security for MSSP's
Recently uploaded
Mifty kit IN Salmiya (+918133066128) Abortion pills IN Salmiyah Cytotec pills

Mifty kit IN Salmiya (+918133066128) Abortion pills IN Salmiyah Cytotec pillsAbortion pills in Kuwait Cytotec pills in Kuwait
Recently uploaded (20)
Value Proposition canvas- Customer needs and pains

Value Proposition canvas- Customer needs and pains
How to Get Started in Social Media for Art League City

How to Get Started in Social Media for Art League City
MONA 98765-12871 CALL GIRLS IN LUDHIANA LUDHIANA CALL GIRL

MONA 98765-12871 CALL GIRLS IN LUDHIANA LUDHIANA CALL GIRL
Insurers' journeys to build a mastery in the IoT usage

Insurers' journeys to build a mastery in the IoT usage
The Path to Product Excellence: Avoiding Common Pitfalls and Enhancing Commun...

The Path to Product Excellence: Avoiding Common Pitfalls and Enhancing Commun...
Yaroslav Rozhankivskyy: Три складові і три передумови максимальної продуктивн...

Yaroslav Rozhankivskyy: Три складові і три передумови максимальної продуктивн...
Mifty kit IN Salmiya (+918133066128) Abortion pills IN Salmiyah Cytotec pills

Mifty kit IN Salmiya (+918133066128) Abortion pills IN Salmiyah Cytotec pills
Enhancing and Restoring Safety & Quality Cultures - Dave Litwiller - May 2024...

Enhancing and Restoring Safety & Quality Cultures - Dave Litwiller - May 2024...
0183760ssssssssssssssssssssssssssss00101011 (27).pdf

0183760ssssssssssssssssssssssssssss00101011 (27).pdf
Lucknow 💋 Escorts in Lucknow - 450+ Call Girl Cash Payment 8923113531 Neha Th...

Lucknow 💋 Escorts in Lucknow - 450+ Call Girl Cash Payment 8923113531 Neha Th...
FULL ENJOY Call Girls In Mahipalpur Delhi Contact Us 8377877756

FULL ENJOY Call Girls In Mahipalpur Delhi Contact Us 8377877756
7.pdf This presentation captures many uses and the significance of the number...

7.pdf This presentation captures many uses and the significance of the number...
RSA Conference Exhibitor List 2024 - Exhibitors Data

RSA Conference Exhibitor List 2024 - Exhibitors Data
Vulnerability Scans & Penetration Test Comparison Chart
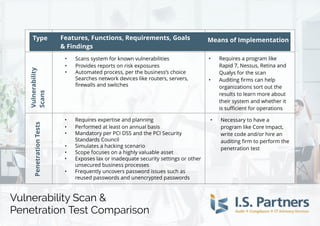
- 1. Type VulnerabilityScansPenetrationTests - Scans system for known vulnerabilities - Provides reports on risk exposures - Automated process, per the business?s choice - Searches network devices like routers, servers, firewalls and switches - Requires a program like Rapid 7, Nessus, Retina and Qualys for the scan - Auditing firms can help organizations sort out the results to learn more about their system and whether it is sufficient for operations - Requires expertise and planning - Performed at least on annual basis - Mandatory per PCI DSSand the PCI Security Standards Council - Simulates a hacking scenario - Scope focuses on a highly valuable asset - Exposes lax or inadequate security settings or other unsecured business processes - Frequently uncovers password issues such as reused passwords and unencrypted passwords - Necessary to have a program like Core Impact, write code and/or hire an auditing firm to perform the penetration test Vulnerability Scan & Penetration Test Comparison Feat ures, Funct ions, Requirement s, Goals & Findings Means of Implement at ion Vulnerability Scan & Penetration Test Comparison Type Feat ures, Funct ions, Requirement s, Goals & Findings Means of Implement at ion Vulnerability Scans PenetrationTests - Scans system for known vulnerabilities - Provides reports on risk exposures - Automated process, per the business?s choice Searches network devices like routers, servers, firewalls and switches - Requires a program like Rapid 7, Nessus, Retina and Qualys for the scan - Auditing firms can help organizations sort out the results to learn more about their system and whether it is sufficient for operations - Requires expertise and planning - Performed at least on annual basis - Mandatory per PCI DSSand the PCI Security Standards Council - Simulates a hacking scenario - Scope focuses on a highly valuable asset - Exposes lax or inadequate security settings or other unsecured business processes - Frequently uncovers password issues such as reused passwords and unencrypted passwords - Necessary to have a program like Core Impact, write code and/or hire an auditing firm to perform the penetration test
