CSRF_main_vid.pptx
•
0 likes•8 views
this video explains what is csrf attack
Report
Share
Report
Share
Recommended
More Related Content
Similar to CSRF_main_vid.pptx
Similar to CSRF_main_vid.pptx (20)
Mutillidae and the OWASP Top 10 by Adrian Crenshaw aka Irongeek

Mutillidae and the OWASP Top 10 by Adrian Crenshaw aka Irongeek
Its all about CSRF - null Mumbai Meet 10 January 2015 Null/OWASP Chapter 

Its all about CSRF - null Mumbai Meet 10 January 2015 Null/OWASP Chapter
Prevention Against CSRF Attack using Client Server Mutual Authentication Tech...

Prevention Against CSRF Attack using Client Server Mutual Authentication Tech...
CROSS-SITE REQUEST FORGERY - IN-DEPTH ANALYSIS 2011

CROSS-SITE REQUEST FORGERY - IN-DEPTH ANALYSIS 2011
[Lithuania] Cross-site request forgery: ways to exploit, ways to prevent![[Lithuania] Cross-site request forgery: ways to exploit, ways to prevent](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Lithuania] Cross-site request forgery: ways to exploit, ways to prevent](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Lithuania] Cross-site request forgery: ways to exploit, ways to prevent
Recently uploaded
Recently uploaded (20)
DevoxxFR 2024 Reproducible Builds with Apache Maven

DevoxxFR 2024 Reproducible Builds with Apache Maven
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
"Federated learning: out of reach no matter how close",Oleksandr Lapshyn

"Federated learning: out of reach no matter how close",Oleksandr Lapshyn
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
Gen AI in Business - Global Trends Report 2024.pdf

Gen AI in Business - Global Trends Report 2024.pdf
Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)

Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
Dev Dives: Streamline document processing with UiPath Studio Web

Dev Dives: Streamline document processing with UiPath Studio Web
Integration and Automation in Practice: CI/CD in Mule Integration and Automat...

Integration and Automation in Practice: CI/CD in Mule Integration and Automat...
Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
CSRF_main_vid.pptx
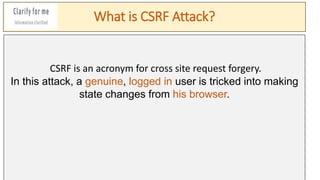
- 1. What is CSRF Attack? CSRF is an acronym for cross site request forgery. In this attack, a genuine, logged in user is tricked into making state changes from his browser.
- 2. What causes CSRF vulnerability ? The attacker exploits the property of web browsers where the browser can automatically include cookies set by a given domain, in any web request sent to that domain(regardless of the origin of the request). https://example.com Example.com AppServer http request to server http response with cookie c1=v1 in response headers Cookie c1=v1 automatically added by browser in subsequent requests to example.com Example.com cookie C1=v1 saved ! Example.com adds cookie C1=v1 to response headers
- 3. CSRF Attack http://icicibank.com/login.jsp ICICI Bank Application server Auth Request Auth_cookie=1234xx SameSite=None Auth_cookie=1234xx Web Browser https://attacker- website.com/anypage.jsp Cross site Form Post (Auth_cokkie=1234xx) State modified Verifying credentials.. Modifying state.. Checking auth cookie https://attacker-website.com/anypage.jsp Nishant **** https://clarifyforme.com Generating session cookie..
- 4. Conclusion Now it should clear that if the browser sends cookies to the application as request headers in cross site requests then there is a possibility of CSRF attack.
- 5. Mitigation SameSite attribute of cookie SameSite=None : The browser will add cookies to request headers in cross site requests. SameSite=Lax : The browser will add cookies to response headers in cross site get requests which lead to top level navigation but block them in POST and script requests. SameSite=Strict : The browser will NOT add cookies to request headers in cross site requests. CSRF tokens Origin and referer header verification
- 6. Read more Links to article , other videos in the play group etc…