How To Become PCI Compliant - Connect First Infographic
A step-by-step infographic on how to become PCI compliant. PCI DSS is a set of requirements established in 2006 to protect consumers throughout the debit or credit card transaction process—from data input to storage. PCI DSS compliance applies to all organizations that store or accept cardholder information. While being contact center PCI compliant is not a law, merchants that do not comply with it are subject to penalties such as heavy fines, brand damage compensation and card replacement costs, among others. It is backed by industry giants such as Visa, MasterCard and American Express. If you are looking for a cloud-based customer management solution, make sure you don’t skimp on PCI DSS compliance. This is crucial given the fact that choosing a cloud partner means you will be storing consumer data off site. Ensure that you have complete visibility into the network and a guarantee that information is being securely maintained in compliance with required standards. Many vendors claim that they have PCI compliance when that is not actually true: they rely on a third party company to run credit card processing though there systems, adding both cost and danger to the process. For more information about Connect First's PCI Compliance Suite: http://www.connectfirst.com/compliance-suite/
Recomendados
Recomendados
Más contenido relacionado
Destacado
Destacado (17)
Más de Connect First
Más de Connect First (12)
Último
Último (20)
How To Become PCI Compliant - Connect First Infographic
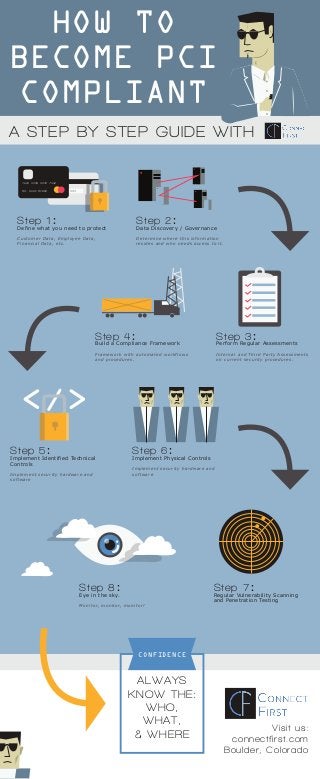
- 1. Visit us: connectfirst.com Boulder, Colorado HOW TO BECOME PCI COMPLIANT A STEP BY STEP GUIDE WITH 993 7624 4558 9932 7440 MR. DUDE MCBRO Step 1: Define what you need to protect Customer Data, Employee Data, Financial Data, etc. Step 2: Data Discovery / Governance Determine where this information resides and who needs access to it. Step 3: Perform Regular Assessments Internal and Third Party Assessments on current security procedures. Step 4: Build a Compliance Framework Framework with automated workflows and procedures. </> Step 5: Implement Identified Technical Controls Implement security hardware and software Step 6: Implement Physical Controls Implement security hardware and software Step 7: Regular Vulnerability Scanning and Penetration Testing Step 8: Eye in the sky. Monitor, monitor, monitor! CONFIDENCE ALWAYS KNOW THE: WHO, WHAT, & WHERE
