Cyber Espionage: A Digital License To Kill?
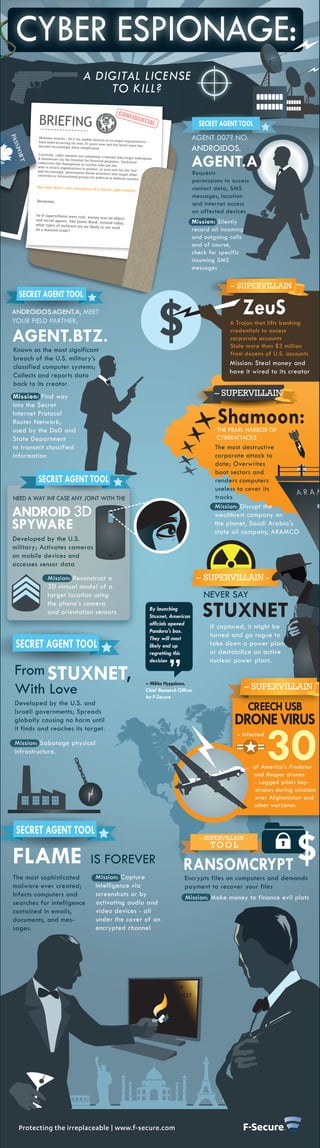
- 1. CYBER ESPIONAGE: A DIGITAL LICENSE TO KILL? BRIEFING SECRET AGENT TOOL Malware attacks – be it for mobi have been occurring for over 25 le devices or on major organizatio ns – AGENT 007? NO. years now and the latest wave become increasingly more comp licated. has ANDROIDOS. AGENT.A Currently, cyber enemies are comm only criminals who target indiv & businesses via the Internet iduals for financial purposes; 'hacktivist collectives like Anonymous or ' LulzSec who use the web to attack organizations in protest, or even just for the 'lulz' and increasingly, government-bo ; countries or international group rne attackers who target other Requests s for political or defense reaso ns. permissions to access But now there’s the emergence of a fourth cyber enemy: contact data, SMS messages, location Terrorists. and Internet access on affected devices So if supervillains were real, mon ey was no object, and secret agents, like James what types of malware are we Bond, existed today, Mission: Silently likely to see used on a massive scale? record all incoming and outgoing calls and of course, check for specific incoming SMS messages – SUPERVILLAIN - SECRET AGENT TOOL ANDROIDOS.AGENT.A, MEET YOUR FIELD PARTNER, ZeuS A Trojan that lifts banking AGENT.BTZ. credentials to access corporate accounts Stole more than $3 million Known as the most significant from dozens of U.S. accounts breach of the U.S. military’s Mission: Steal money and classified computer systems; have it wired to its creator Collects and reports data back to its creator Mission: Find way – SUPERVILLAIN into the Secret Internet Protocol Router Network, used by the DoD and Shamoon: THE PEARL HARBOR OF State Department CYBERATTACKS to transmit classified The most destructive information corporate attack to date; Overwrites boot sectors and SECRET AGENT TOOL renders computers useless to cover its NEED A WAY IN? CASE ANY JOINT WITH THE tracks ANDROID 3D Mission: Disrupt the wealthiest company on SPYWARE the planet, Saudi Arabia's state oil company, ARAMCO Developed by the U.S. military; Activates cameras on mobile devices and accesses sensor data Mission: Reconstruct a – SUPERVILLAIN - 3D virtual model of a target location using NEVER SAY STUXNET the phone’s camera By launching and orientation sensors Stuxnet, American officials opened If captured, it might be Pandora's box. They will most turned and go rogue to SECRET AGENT TOOL likely end up take down a power plant, regretting this or destabilize an active decision nuclear power plant. From STUXNET, With Love – Mikko Hyppönen, Chief Research Officer – SUPERVILLAIN for F-Secure Developed by the U.S. and Israeli governments; Spreads CREECH USB globally causing no harm until DRONE VIRUS 30 it finds and reaches its target. - Infected Mission: Sabotage physical infrastructure. of America's Predator and Reaper drones - Logged pilots key- strokes during missions over Afghanistan and other warzones SECRET AGENT TOOL – SUPERVILLAIN - TOOL FLAME IS FOREVER RANSOMCRYPT The most sophisticated Mission: Capture Encrypts files on computers and demands malware ever created; intelligence via payment to recover your files Infects computers and screenshots or by Mission: Make money to finance evil plots searches for intelligence activating audio and contained in emails, video devices - all documents, and mes- under the cover of an sages. encrypted channel TOP SECRET Protecting the irreplaceable | www.f-secure.com
