Flowchart - Building next gen malware behavioural analysis environment
•
1 recomendación•614 vistas
ISC2 Hellenic Chapter 25/10/2016
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
App secforum2014 andrivet-cplusplus11-metaprogramming_applied_to_software_obf...

App secforum2014 andrivet-cplusplus11-metaprogramming_applied_to_software_obf...Cyber Security Alliance
Recomendados
App secforum2014 andrivet-cplusplus11-metaprogramming_applied_to_software_obf...

App secforum2014 andrivet-cplusplus11-metaprogramming_applied_to_software_obf...Cyber Security Alliance
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Nessus scan report using microsoft patchs scan policy - Tareq Hanaysha

Nessus scan report using microsoft patchs scan policy - Tareq Hanaysha
Specializing the Data Path - Hooking into the Linux Network Stack

Specializing the Data Path - Hooking into the Linux Network Stack
ZeroNights: Automating iOS blackbox security scanning

ZeroNights: Automating iOS blackbox security scanning
MongoDB 2.8 Replication Internals: Fitting it all together

MongoDB 2.8 Replication Internals: Fitting it all together
Destacado
Destacado (12)
Building next gen malware behavioural analysis environment 

Building next gen malware behavioural analysis environment
The evolving threats and the challenges of the modern CISO

The evolving threats and the challenges of the modern CISO
Pci standards, from participation to implementation and review

Pci standards, from participation to implementation and review
European Cyber Security Challenge - Greel National Cyber Security Team

European Cyber Security Challenge - Greel National Cyber Security Team
Similar a Flowchart - Building next gen malware behavioural analysis environment
Similar a Flowchart - Building next gen malware behavioural analysis environment (20)
finalprojtemplatev5finalprojtemplate.gitignore# Ignore the b

finalprojtemplatev5finalprojtemplate.gitignore# Ignore the b
Midiendo la calidad de código en WTF/Min (Revisado EUI Abril 2014)

Midiendo la calidad de código en WTF/Min (Revisado EUI Abril 2014)
Shell to be modified#include stdlib.h #include unistd.h .pdf

Shell to be modified#include stdlib.h #include unistd.h .pdf
The Ring programming language version 1.6 book - Part 28 of 189

The Ring programming language version 1.6 book - Part 28 of 189
200 Open Source Projects Later: Source Code Static Analysis Experience

200 Open Source Projects Later: Source Code Static Analysis Experience
"Revenge of The Script Kiddies: Current Day Uses of Automated Scripts by Top ...

"Revenge of The Script Kiddies: Current Day Uses of Automated Scripts by Top ...
“Linux Kernel CPU Hotplug in the Multicore System”

“Linux Kernel CPU Hotplug in the Multicore System”
Más de isc2-hellenic
Más de isc2-hellenic (12)
Event 16 12-15 global information security workforce study 1.0

Event 16 12-15 global information security workforce study 1.0
5. Experience from recent national & international cyber exercises

5. Experience from recent national & international cyber exercises
Último
Último (20)
Generative Artificial Intelligence: How generative AI works.pdf

Generative Artificial Intelligence: How generative AI works.pdf
Why device, WIFI, and ISP insights are crucial to supporting remote Microsoft...

Why device, WIFI, and ISP insights are crucial to supporting remote Microsoft...
Take control of your SAP testing with UiPath Test Suite

Take control of your SAP testing with UiPath Test Suite
Long journey of Ruby standard library at RubyConf AU 2024

Long journey of Ruby standard library at RubyConf AU 2024
So einfach geht modernes Roaming fuer Notes und Nomad.pdf

So einfach geht modernes Roaming fuer Notes und Nomad.pdf
A Journey Into the Emotions of Software Developers

A Journey Into the Emotions of Software Developers
Modern Roaming for Notes and Nomad – Cheaper Faster Better Stronger

Modern Roaming for Notes and Nomad – Cheaper Faster Better Stronger
Merck Moving Beyond Passwords: FIDO Paris Seminar.pptx

Merck Moving Beyond Passwords: FIDO Paris Seminar.pptx
Decarbonising Buildings: Making a net-zero built environment a reality

Decarbonising Buildings: Making a net-zero built environment a reality
Transcript: New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024
Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx

Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx
TeamStation AI System Report LATAM IT Salaries 2024

TeamStation AI System Report LATAM IT Salaries 2024
How to Effectively Monitor SD-WAN and SASE Environments with ThousandEyes

How to Effectively Monitor SD-WAN and SASE Environments with ThousandEyes
The Fit for Passkeys for Employee and Consumer Sign-ins: FIDO Paris Seminar.pptx

The Fit for Passkeys for Employee and Consumer Sign-ins: FIDO Paris Seminar.pptx
How AI, OpenAI, and ChatGPT impact business and software.

How AI, OpenAI, and ChatGPT impact business and software.
The Future Roadmap for the Composable Data Stack - Wes McKinney - Data Counci...

The Future Roadmap for the Composable Data Stack - Wes McKinney - Data Counci...
Flowchart - Building next gen malware behavioural analysis environment
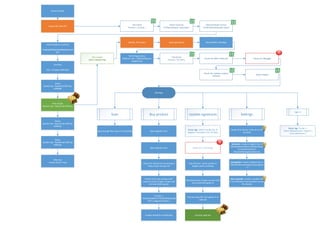
- 1. Extract Archive Unpack file with UPX Load TempKey in memory “c9e0b830ff18645849b8dbab57e47 7b5” CPU Check if (cores < 3) { Exit; } Check resources If (!filexists(base*.dat)) {exit;} Check Windows Version If (!WinVistaOrGreater) {exit;} Final Key Key = TempKey XOR 0x03 Decoy Base8.tmp = Base8.dat XOR Key XOR0x08 Real sample Base16.tmp = Base16.dat XOR key Decoy Base32.tmp = Base32.dat XOR Key XOR0x32 Decoy Base64.tmp = Base64.dat XOR Key XOR0x64 Clean-up: remove (base*.tmp) Run sample cmd /c base16.tmp Identify .NET binary Decompile binary RansomKiller: MainApp Write Registry Key RAND 15 char = HKLMSoftware SergSecKey CPU Check if (cores < 5) { Exit; } Checks for MAC ofNetcard Checks for debugger Checks for malware analysis software Detect HyperV MainApp Scan Buy product Update signatures Settings goes through files, doesn’t do anything Open Register Form Open Register Form Checks for internet by connecting to https://cyber-europe.net Checks thekey by sending a GET request to https://cyber-europe.net/ evl/ransomkill/reg.php If (reply == “260CA9DD8A4577FC00B7BD5810298 076") { RegisterProduct; } Enables all buttons of MainApp Easter Egg: checks ifpublic key of SergSec is installed in the CA Store Downloads https://cyber-europe.net// evl/ransomkill/update.rk Check ifit’s a Thursday Decrypt using AES-128 update.rk to updt.exe Gets AES Key = serial number of SergSec public certificate Executes updt.exe Creates Task: binary to be ran on 12th Oct 2016 Autoupdate: creates a Registry Key in HKLMSoftwareSergSecAutoUpdate = 1 Autostart: creates a Registry Key in HKLMSoftwareMicrosoftWindows CurrentVersionRun RansomKillerAppbase16.tmp Auto schedule: creates a weekly Task in theWindows Task Scheduler named RK_Weekly Sign in Easter Egg: if (user == “demo”)&(password==”demo”) { AccessWebPanel; }
- 2. updt.exe MainApp Hides Window Stalls Execution via Search Stalls Execution via Math Calculation Checks for debugger (Necromancy Check) Deletes Old Logs Anti-Forensics Checks Username Computer Name Processes Running CheckChecks for debugger (Running Proccess) Stalls Execution via Search2 Keylogger ScreenGrabber Sends data to: 10.210.1.12 Exfiltrator Stores key strikes in: rNdfgl34f.txt Grabs Printscreen test.jpg 500 Strikes Persistance Deletes Logs