TDM Figures and Concepts Explained
•Descargar como PPT, PDF•
1 recomendación•2,057 vistas
The document contains figures and captions from a textbook about synchronous and asynchronous time-division multiplexing (TDM) techniques. The figures illustrate concepts such as multiplexing, demultiplexing, framing bits, data rates, frames and addresses for TDM with different numbers of lines sending data.
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (16)
Similar a TDM Figures and Concepts Explained
Similar a TDM Figures and Concepts Explained (20)
Más de koolkampus
Más de koolkampus (17)
Transmission of Digital Data(Data Communication) DC11

Transmission of Digital Data(Data Communication) DC11
Analog to Digital Encoding in Data Communication DC9

Analog to Digital Encoding in Data Communication DC9
Analog to Analog Modulation in Data Communication DC10

Analog to Analog Modulation in Data Communication DC10
Authentication Application in Network Security NS4

Authentication Application in Network Security NS4
Último
Último (20)
How AI, OpenAI, and ChatGPT impact business and software.

How AI, OpenAI, and ChatGPT impact business and software.
Ensuring Technical Readiness For Copilot in Microsoft 365

Ensuring Technical Readiness For Copilot in Microsoft 365
Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx

Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx
TrustArc Webinar - How to Build Consumer Trust Through Data Privacy

TrustArc Webinar - How to Build Consumer Trust Through Data Privacy
Take control of your SAP testing with UiPath Test Suite

Take control of your SAP testing with UiPath Test Suite
TeamStation AI System Report LATAM IT Salaries 2024

TeamStation AI System Report LATAM IT Salaries 2024
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024

New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024
Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)

Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
Scanning the Internet for External Cloud Exposures via SSL Certs

Scanning the Internet for External Cloud Exposures via SSL Certs
Digital Identity is Under Attack: FIDO Paris Seminar.pptx

Digital Identity is Under Attack: FIDO Paris Seminar.pptx
New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
Hyperautomation and AI/ML: A Strategy for Digital Transformation Success.pdf

Hyperautomation and AI/ML: A Strategy for Digital Transformation Success.pdf
TDM Figures and Concepts Explained
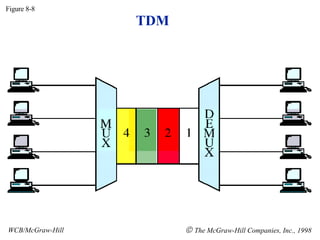
- 1. TDM Figure 8-8 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 2. Synchronous TDM Figure 8-9 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 3. Figure 8-10 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 TDM, Multiplexing
- 4. Figure 8-11 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 TDM, Demultiplexing
- 5. Framing Bits Figure 8-12 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 6. Data Rate Figure 8-13 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 7. Asynchronous TDM Figure 8-14 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 8. Frames and Addresses Figure 8-15 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 a. Only three lines sending data
- 9. Frames and Addresses Figure 8-15-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 b. Only four lines sending data
- 10. Frames and Addresses Figure 8-15-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 c. All five lines sending data
- 11. Figure 8-16 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Multiplexing and Inverse Multiplexing