Security Awareness 9 10 09 V4 Web Browser
•Descargar como PPTX, PDF•
0 recomendaciones•253 vistas
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Information Security Awareness And Training Business Case For Web Based Solut...

Information Security Awareness And Training Business Case For Web Based Solut...Michael Kaishar, MSIA | CISSP
Más contenido relacionado
La actualidad más candente
Information Security Awareness And Training Business Case For Web Based Solut...

Information Security Awareness And Training Business Case For Web Based Solut...Michael Kaishar, MSIA | CISSP
La actualidad más candente (11)
PRESENTATION DATA PROTECTION CONFERENCE ASIAN LEGAL BUSINESS (ALB) 2014 KUALA...

PRESENTATION DATA PROTECTION CONFERENCE ASIAN LEGAL BUSINESS (ALB) 2014 KUALA...
Information Security Awareness And Training Business Case For Web Based Solut...

Information Security Awareness And Training Business Case For Web Based Solut...
Et 5083 week 3 assignment - technology safety, security, & filtering traini...

Et 5083 week 3 assignment - technology safety, security, & filtering traini...
Addressing todays Governance Risk and Compliance Requirements

Addressing todays Governance Risk and Compliance Requirements
Similar a Security Awareness 9 10 09 V4 Web Browser
Similar a Security Awareness 9 10 09 V4 Web Browser (20)
Social Engineering: Protecting Yourself on the Campus Network

Social Engineering: Protecting Yourself on the Campus Network
An introduction to cyber security by cyber security infotech pvt ltd(csi)

An introduction to cyber security by cyber security infotech pvt ltd(csi)
Dev Abhijet Gagan Chaitanya VII-A ....Salwan public school

Dev Abhijet Gagan Chaitanya VII-A ....Salwan public school
CYBER SECURITY AND CYBER CRIME COMPLETE GUIDE.pLptx

CYBER SECURITY AND CYBER CRIME COMPLETE GUIDE.pLptx
Más de Megan Bell
Más de Megan Bell (9)
Week 1 ppt and-lecture-transcript-with audio2slides

Week 1 ppt and-lecture-transcript-with audio2slides
Último
Último (20)
WordPress Websites for Engineers: Elevate Your Brand

WordPress Websites for Engineers: Elevate Your Brand
Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
Unleash Your Potential - Namagunga Girls Coding Club

Unleash Your Potential - Namagunga Girls Coding Club
New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
The Ultimate Guide to Choosing WordPress Pros and Cons

The Ultimate Guide to Choosing WordPress Pros and Cons
Use of FIDO in the Payments and Identity Landscape: FIDO Paris Seminar.pptx

Use of FIDO in the Payments and Identity Landscape: FIDO Paris Seminar.pptx
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
DevoxxFR 2024 Reproducible Builds with Apache Maven

DevoxxFR 2024 Reproducible Builds with Apache Maven
TrustArc Webinar - How to Build Consumer Trust Through Data Privacy

TrustArc Webinar - How to Build Consumer Trust Through Data Privacy
TeamStation AI System Report LATAM IT Salaries 2024

TeamStation AI System Report LATAM IT Salaries 2024
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
Scanning the Internet for External Cloud Exposures via SSL Certs

Scanning the Internet for External Cloud Exposures via SSL Certs
Security Awareness 9 10 09 V4 Web Browser
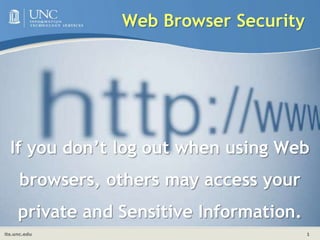
- 1. Web Browser Security If you don’t log out when using Web browsers, others may access your private and Sensitive Information.
- 2. Web Browser Security Section: Web Browser Security When using Web browsers (like Internet Explorer or Firefox) log out of sites storing Sensitive Information. banking sites, Payroll services, Student Central, etc. Many Web sites store (cache) personal information, such as login names and passwords, until a user logs out.
- 3. Suspect Unauthorized Access? …Steps to Take Section: Web Browser Security Immediately notify University officials: Your supervisor Office of University Counsel Information Security Office at (919.445.9393) ITS Help Desk at (919.962.HELP) Problems or Questions? Contact (919.962.HELP) or your departmental IT staff for assistance on downloading and installing any software from the ITS Shareware site.
- 4. Your Responsibilities If Unauthorized Access Occurs Section: Web Browser Security The University is required to take reasonable steps to lessen harmful effects of any unauthorized access. Timely notification of the incident is vitalto minimize potential harm. Remember: It is always better to ask questions first rather than risk violating a University policy. Call (919.962.HELP) for advice.
- 5. Learning Point # 6 Section: Web Browser Security If you believe that Sensitive Information has been accessed by a hacker, you should inform University staff. Right? Right! Everyone affiliated with the University should report an unauthorized access to Sensitive Information. Notification can occur by calling 919.962.HELP.