Excell shortcuts
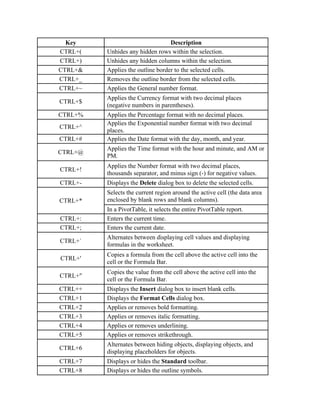
- 1. Key Description CTRL+( Unhides any hidden rows within the selection. CTRL+) Unhides any hidden columns within the selection. CTRL+& Applies the outline border to the selected cells. CTRL+_ Removes the outline border from the selected cells. CTRL+~ Applies the General number format. Applies the Currency format with two decimal places CTRL+$ (negative numbers in parentheses). CTRL+% Applies the Percentage format with no decimal places. Applies the Exponential number format with two decimal CTRL+^ places. CTRL+# Applies the Date format with the day, month, and year. Applies the Time format with the hour and minute, and AM or CTRL+@ PM. Applies the Number format with two decimal places, CTRL+! thousands separator, and minus sign (-) for negative values. CTRL+- Displays the Delete dialog box to delete the selected cells. Selects the current region around the active cell (the data area CTRL+* enclosed by blank rows and blank columns). In a PivotTable, it selects the entire PivotTable report. CTRL+: Enters the current time. CTRL+; Enters the current date. Alternates between displaying cell values and displaying CTRL+` formulas in the worksheet. Copies a formula from the cell above the active cell into the CTRL+' cell or the Formula Bar. Copies the value from the cell above the active cell into the CTRL+" cell or the Formula Bar. CTRL++ Displays the Insert dialog box to insert blank cells. CTRL+1 Displays the Format Cells dialog box. CTRL+2 Applies or removes bold formatting. CTRL+3 Applies or removes italic formatting. CTRL+4 Applies or removes underlining. CTRL+5 Applies or removes strikethrough. Alternates between hiding objects, displaying objects, and CTRL+6 displaying placeholders for objects. CTRL+7 Displays or hides the Standard toolbar. CTRL+8 Displays or hides the outline symbols.
- 2. CTRL+9 Hides the selected rows. CTRL+0 Hides the selected columns. Selects the entire worksheet. If the worksheet contains data, CTRL+A selects the current region. Pressing CTRL+A a second time selects the entire worksheet. CTRL+A When the insertion point is to the right of a function name in a formula, displays the Function Arguments dialog box. CTRL+SHIFT+A inserts the argument names and parentheses when the insertion point is to the right of a function name in a formula. CTRL+B Applies or removes bold formatting. Copies the selected cells. CTRL+C CTRL+C followed by another CTRL+C displays the Microsoft Office Clipboard. Uses the Fill Down command to copy the contents and format CTRL+D of the topmost cell of a selected range into the cells below. Displays the Find dialog box. CTRL+F SHIFT+F5 also displays this dialog box, while SHIFT+F4 repeats the last Find action. Displays the Go To dialog box. CTRL+G F5 also displays this dialog box. CTRL+H Displays the Find and Replace dialog box. CTRL+I Applies or removes italic formatting. Displays the Insert Hyperlink dialog box for new hyperlinks CTRL+K or the Edit Hyperlink dialog box for selected existing hyperlinks. CTRL+L Displays the Create List dialog box. CTRL+N Creates a new, blank file. Displays the Open dialog box to open or find a file. CTRL+O CTRL+SHIFT+O selects all cells that contain comments. CTRL+P Displays the Print dialog box. Uses the Fill Right command to copy the contents and format CTRL+R of the leftmost cell of a selected range into the cells to the right. Saves the active file with its current file name, location, and CTRL+S file format. CTRL+U Applies or removes underlining.
- 3. Inserts the contents of the Clipboard at the insertion point and CTRL+V replaces any selection. Available only after you cut or copied an object, text, or cell contents. CTRL+W Closes the selected workbook window. CTRL+X Cuts the selected cells. CTRL+Y Repeats the last command or action, if possible. Uses the Undo command to reverse the last command or to delete the last entry you typed. CTRL+Z CTRL+SHIFT+Z uses the Undo or Redo command to reverse or restore the last automatic correction when AutoCorrect Smart Tags are displayed. Function keys Key Description Displays the Help task pane. CTRL+F1 closes and reopens the current task pane. F1 ALT+F1 creates a chart of the data in the current range. ALT+SHIFT+F1 inserts a new worksheet. Edits the active cell and positions the insertion point at the end of the cell contents. It also moves the insertion point into the F2 Formula Bar when editing in a cell is turned off. SHIFT+F2 edits a cell comment. Pastes a defined name into a formula. F3 SHIFT+F3 displays the Insert Function dialog box. Repeats the last command or action, if possible. F4 CTRL+F4 closes the selected workbook window. Displays the Go To dialog box. F5 CTRL+F5 restores the window size of the selected workbook window. Switches to the next pane in a worksheet that has been split (Window menu, Split command). SHIFT+F6 switches to the previous pane in a worksheet that F6 has been split. CTRL+F6 switches to the next workbook window when more than one workbook window is open.
- 4. Note When the task pane is visible, F6 and SHIFT+F6 include that pane when switching between panes. Displays the Spelling dialog box to check spelling in the active worksheet or selected range. F7 CTRL+F7 performs the Move command on the workbook window when it is not maximized. Use the arrow keys to move the window, and when finished press ESC. Turns extend mode on or off. In extend mode, EXT appears in the status line, and the arrow keys extend the selection. SHIFT+F8 enables you to add a non-adjacent cell or range to a selection of cells by using the arrow keys. F8 CTRL+F8 performs the Size command (on the Control menu for the workbook window) when a workbook is not maximized. ALT+F8 displays the Macro dialog box to run, edit, or delete a macro. Calculates all worksheets in all open workbooks. F9 followed by ENTER (or followed by CTRL+SHIFT+ENTER for array formulas) calculates the selected a portion of a formula and replaces the selected portion with the calculated value. SHIFT+F9 calculates the active worksheet. F9 CTRL+ALT+F9 calculates all worksheets in all open workbooks, regardless of whether they have changed since the last calculation. CTRL+ALT+SHIFT+F9 rechecks dependent formulas, and then calculates all cells in all open workbooks, including cells not marked as needing to be calculated. CTRL+F9 minimizes a workbook window to an icon. Selects the menu bar or closes an open menu and submenu at the same time. SHIFT+F10 displays the shortcut menu for a selected item. F10 ALT+SHIFT+F10 displays the menu or message for a smart tag. If more than one smart tag is present, it switches to the next smart tag and displays its menu or message. CTRL+F10 maximizes or restores the selected workbook window. Creates a chart of the data in the current range. F11 SHIFT+F11 inserts a new worksheet.
- 5. ALT+F11 opens the Visual Basic Editor, in which you can create a macro by using Visual Basic for Applications (VBA). ALT+SHIFT+F11 opens the Microsoft Script Editor, where you can add text, edit HTML tags, and modify any script code. F12 Displays the Save As dialog box. Other useful shortcut keys Key Description Move one cell up, down, left, or right in a worksheet. CTRL+ARROW KEY moves to the edge of the current data region (data region: A range of cells that contains data and that is bounded by empty cells or datasheet borders.) in a worksheet. SHIFT+ARROW KEY extends the selection of cells by one cell. CTRL+SHIFT+ARROW KEY extends the selection of cells to the last nonblank cell in the same column or row as the active cell. ARROW KEYS LEFT ARROW or RIGHT ARROW selects the menu to the left or right when a menu is visible. When a submenu is open, these arrow keys switch between the main menu and the submenu. DOWN ARROW or UP ARROW selects the next or previous command when a menu or submenu is open. In a dialog box, arrow keys move between options in an open drop--down list, or between options in a group of options. ALT+DOWN ARROW opens a selected drop down list. drop-down Deletes one character to the left in the Formula Bar. BACKSPACE Also clears the content of the active cell. Removes the cell contents (data and formulas) from selected cells without affecting cell formats or comments. DELETE In cell editing mode, it deletes the character to the right of the insertion point. Moves to the cell in the lower lower-right corner of the window when SCROLL LOCK is turned on. Also selects the last command on the menu when a menu or submenu is visible. END CTRL+END moves to the last cell on a worksheet, in the lowest used row of the rightmost used column. CTRL+SHIFT+END extends the selection of cells to the last used cell on the worksheet (lower (lower-right corner).
- 6. Completes a cell entry from the cell or the Formula Bar, and selects the cell below (by default). In a data form, it moves to the first field in the next record. Opens a selected menu (press F10 to activate the menu bar) or performs the action for a selected command. In a dialog box, it performs the action for the default ENTER command button in the dialog box (the button with the bold outline, often the OK button). ALT+ENTER starts a new line in the same cell. CTRL+ENTER fills the selected cell range with the current entry. SHIFT+ENTER completes a cell entry and selects the cell above. Cancels an entry in the cell or Formula Bar. ESC It also closes an open menu or submenu, dialog box, or message window. Moves to the beginning of a row in a worksheet. Moves to the cell in the upper-left corner of the window when SCROLL LOCK is turned on. Selects the first command on the menu when a menu or HOME submenu is visible. CTRL+HOME moves to the beginning of a worksheet. CTRL+SHIFT+HOME extends the selection of cells to the beginning of the worksheet. Moves one screen down in a worksheet. ALT+PAGE DOWN moves one screen to the right in a worksheet. PAGE DOWN CTRL+PAGE DOWN moves to the next sheet in a workbook. CTRL+SHIFT+PAGE DOWN selects the current and next sheet in a workbook. Moves one screen up in a worksheet. ALT+PAGE UP moves one screen to the left in a worksheet. PAGE UP CTRL+PAGE UP moves to the previous sheet in a workbook. CTRL+SHIFT+PAGE UP selects the current and previous sheet in a workbook. In a dialog box, performs the action for the selected button, or SPACEBAR selects or clears a check box. CTRL+SPACEBAR selects an entire column in a worksheet.
- 7. SHIFT+SPACEBAR select an entire row in a worksheet. CTRL+SHIFT+SPACEBAR select the entire worksheet. If the worksheet contains data, CTRL+SHIFT+SPACEBAR selects the current region. Pressing CTRL+SHIFT+SPACEBAR a second time selects the entire worksheet. When an object is selected, CTRL+SHIFT+SPACEBAR selects all objects on a worksheet. ALT+SPACEBAR displays the Control menu for the Excel window. Moves one cell to the right in a worksheet. Moves between unlocked cells in a protected worksheet. Moves to the next option or option group in a dialog box. TAB SHIFT+TAB moves to the previous cell in a worksheet or the previous option in a dialog box. CTRL+TAB switches to the next tab in dialog box. CTRL+SHIFT+TAB switches to the previous tab in a dialog box.
- 8. Control Systems Procurement & Maintenance Specifications Terms List SCADA Procurement Project Procurement Specifications Terms List The list of terms is critical to ensure there is a common understanding in developing procurement language. The objective was to provide definitions that are clear, concise and applicable to the procurement effort. This common terms document will be a living document and can grow and change over time. ACL (Access Control List) — An access control list is a concept in computer security, used to enforce privilege separation. It is a means of enforcing the appropriate access rights to a given object given certain aspects of the user process that is requesting them, principally the process's user identity. On a router an access list specifies which addresses are allowed to access services. Access lists can be used to control both inbound and outbound traffic on a router. Active Directory — Active Directory is an implementation of LDAP directory services by Microsoft for use in Windows environments. Active Directory allows administrators to assign enterprise-wide policies, deploy programs to many computers, and apply critical updates to an entire organization. An Active Directory stores information and settings relating to an organization in a central, organized, accessible database. Active Directory networks can vary from a small installation with a few hundred objects, to a large installation with millions of objects. AES — AES is the Advanced Encryption Standard (AES) that is a block cipher adopted as an encryption standard by the US government. It is expected to be used worldwide and analyzed extensively, as was the case with its predecessor, the Data Encryption Standard (DES). AES was adopted by National Institute of Standards and Technology (NIST) as US FIPS PUB 197 in November 2001. AP (Access Point) — A wireless access point (WAP or AP) is a device that "connects" wireless communication devices together to create a wireless network. The WAP is usually connected to a wired network, and can relay data between devices on each side. API (Application Programming Interface) — APIs are a set of definitions of the ways in which one piece of computer software communicates with another. It is a method of achieving abstraction, usually (but not necessarily) between lower-level and higher-level software. Asynchronous Transfer Mode (ATM) — ATM is a cell relay network protocol which encodes data traffic into small fixed-sized (53 byte; 48 bytes of data and 5 bytes of header information) cells instead of variable sized packets as in packet-switched networks (such as the Internet Protocol or Ethernet). It is a connection-oriented technology, in which a connection is established between the two endpoints before the actual data exchange begins. 5/13/2010 Page 1 of 13
- 9. Control Systems Procurement & Maintenance Specifications Terms List Authentication — Authentication is the process of verifying an identity claimed by or for a system entity. Also, any security measure designed to establish the validity of a transmission, message, or originator, or a means of verifying and individual’s eligibility to receive specific categories of information [http://www.its.bldrdoc.gov/fs-1037/]. As perceived by a computer user, authentication is generally associated with a password and/or token(s) entered into a host system for the purpose of gaining access to computer application(s). As examples of user authentication to a host computer, the authentication mechanism might be a password or string of characters provided by the user at a prompt (something you know), and/or a token (something you have), and/or a fingerprint (something you are). Authorization — Authorization is a right or a permission that is granted to a system entity to access a system resource. BPL (Broadband over Power Lines) — Also known as Power Line Communications (PLC), can transmit data at up to 200Mbps by utilizing normal electrical power lines. Users of the service would plug their broadband modem into a normal power receptacle. CHAP — The Challenge-Handshake Authentication Protocol (CHAP) authenticates a user to an Internet access provider. RFC 1994: PPP Challenge Handshake Authentication Protocol (CHAP) defines the protocol. Cleartext — Data in which the semantic information content (i.e., the meaning) is intelligible or is directly available as opposed to ciphertext which is encrypted. Client — A Client is any computer whose identification and authorization privileges for network connection are hosted by a server. An HMI interface (e.g., at operator desks in a Control Room) is an example of a client computer configuration. Common Criteria (CC) — ISO/IEC 15408, a standard for evaluating information technology products and systems, such as operating systems, computer networks, distributed systems, and applications. It states requirements for security functions and for assurance measures, which addresses data confidentiality, data integrity, and availability, focuses on threats to information arising from human activities, malicious or otherwise, applies to security measures implemented in hardware, firmware, or software Configuration Management — The term configuration management has the following meanings: The management of features and assurances (including security) through control of changes made to hardware, software, firmware, documentation, test, test fixtures and test documentation of an automated information system, throughout the development and operational life of a system. Source Code Management or revision control is part of this. 5/13/2010 Page 2 of 13
- 10. Control Systems Procurement & Maintenance Specifications Terms List The control of changes made to the hardware, software, firmware, and documentation throughout the system lifecycle. Control System — An interconnection of components (computers, sensors, actuators, communication pathways, etc.) connected or related in such a manner as to command, direct, or regulate itself or another system (e.g., chemical process plant equipment/system, oil refinery equipment/systems, electric generation/distribution equipment/systems, water/waste water systems, manufacturing control systems, etc.). Data Acquisition — The sampling of the real world to acquire data that can be recorded and/or manipulated by a computer. Sometimes abbreviated DAQ, data acquisition typically involves acquisition of signals and waveforms and processing the signals to obtain desired information. Database Server — A server hosting a database system (usually an RDBMS) typically used as a historian and/or business link to the process control environment. Data Logger — A data logger is an electronic instrument that records digital or analog measurements over time. DCS (Distributed Control System) — Distributed control systems are used in industrial and civil engineering applications to monitor and control distributed equipment with remote human intervention. DES — The Data Encryption Standard (DES) is a cipher (a method for encrypting information) selected as an official Federal Information Processing Standard (FIPS) for the United States in 1976, and which has subsequently enjoyed widespread use internationally. It is being replaced by AES. DNP3 (Distributed Network Protocol) — DNP3 is an open, standards-based communication protocol commonly used in the utility industry. DNP3 provides multiplexing, data fragmentation, error checking, link control, prioritization, and layer 2 addressing services for user data. DoS (Denial of Service) — An attack on a computer system or network that causes a loss of service to users, typically the loss of network connectivity and services by consuming the bandwidth of the victim network or overloading the computational resources of the victim system. A DDoS (Distributed Denial of Service) attack consists of hundreds or thousands of globally distributed sources. Direct-sequence spread spectrum (DSSS) — In telecommunications, direct- sequence spread spectrum is a modulation technique where the transmitted signal takes up 5/13/2010 Page 3 of 13
- 11. Control Systems Procurement & Maintenance Specifications Terms List more bandwidth than the information signal that is being modulated, which is the reason that it is called spread spectrum. Discretionary Access Control (DAC) — Discretionary access control defines basic access control policies to objects in a file system. Generally, these are done at the discretion of the object owner -- file/directory permissions and user/group ownership. Demilitarized Zone (DMZ) — Isolation zone between a protected control network (CN) and external users, such that all production traffic “flowing” between the CN and those external users actually flows through an access control device, such as a firewall. DSL — Digital Subscriber Line (also, ADSL, RDSL) is the typical technology used for delivering broadband communications over copper circuits. Widely used for home and small office broadband connection. EAP — Extensible Authentication Protocol, or EAP (pronounced "eep"), is a universal authentication mechanism, frequently used in wireless networks and Point-to-Point connections. Although the EAP protocol is not limited to wireless LAN networks and can be used for wired LAN authentication, it is most often used in wireless LAN networks. The WPA and WPA2 standard has officially adopted five EAP types as its official authentication mechanisms. Embedded System/OS — A special-purpose computer controlled electro-mechanical system in which the computer is completely encapsulated by the device it controls. An embedded system has specific requirements and performs pre-defined tasks, unlike a general-purpose personal computer. Encryption — In cryptography, encryption is the process of obscuring information to make it unreadable without special knowledge. Ethernet — Ethernet is a frame-based computer networking technology for local area networks (LANs). It defines wiring and signaling for the physical layer, and frame formats and protocols for the media access control (MAC)/data link layer of the OSI model. Ethernet is mostly standardized as IEEE 802.3. Factory Acceptance Test — A test conducted at the vendor premise usually by a third- party to ensure operability of a system according to specifications. Front End Processor (FEP) — A computer which handles communications processing for a larger computer. Data collection systems may include a front end processor which accepts data from instruments and partially processes it before transfer to a larger computer. 5/13/2010 Page 4 of 13
- 12. Control Systems Procurement & Maintenance Specifications Terms List Frequency-hopping spread spectrum (FHSS) — Frequency-hopping spread spectrum (FHSS) is a spread-spectrum method of transmitting radio signals by rapidly switching a carrier among many frequency channels, using a pseudorandom sequence known to both transmitter and receiver. FIELDBUS — Fieldbus control system is a form of decentralized control which links PLC's via a Controller Area Network (CAN) to control the manufacturing processes at the workshop-floor level. Such systems include Profibus, Netbus, LonWorks, Industrial Ethernet and many others. Firewall — Firewall is hardware and/or software which functions in a networked environment to prevent some communications forbidden by the security policy. It has the basic task of controlling traffic between different zones of trust. Typical zones of trust include the Internet (a zone with no trust) and an internal network (a zone with higher trust). FTP (File Transfer Protocol) — The File Transfer Protocol is a software standard for transferring computer files between machines. It belongs to the application layer of the TCP/IP protocol suite. Since FTP is non-secure it is being replaced by sftp - Secure File Transfer Protocol. Gateway — Gateway in a communications network is a network node equipped for interfacing with another network that uses different protocols. GPRS — GPRS is the General Packet Radio Service a standard for digital overlay on the GSM digital cellular system. It allows high speed digital and IP connections to be established using existing GSM voice infrastructure and is generally used to provide IP connectivity to RTUs. GSM — GSM is Global System for Mobile communications. It is the most common digital cellular system. GSM can be used for both voice and data applications. It is also used to provide serial communications to RTUs. Hardened System/OS — Hardened hardware and/or software that has been modified with high security and hardening features, packages and enhanced toolkits, kernel patches and other cryptography and security related enhancements. HMI (Human-Machine Interface) — A term that refers to the "layer" that separates a human that is operating a machine from the machine itself. One example of a HMI is the computer hardware and software that enables a single operator to monitor and control large machinery remotely. 5/13/2010 Page 5 of 13
- 13. Control Systems Procurement & Maintenance Specifications Terms List Host-based intrusion detection system (HIDS) — HIDS is an application that detects possible malicious activity on a host from characteristics such as change of files (file system integrity checker), operating system call profiles, etc. Hyper-text Transfer Protocol (HTTP) — HTTP is a request/response protocol between clients and servers. The originating client, such as a web browser, spider, or other end- user tool, is referred to as the user agent. The destination server, which stores or creates resources such as HTML files and images, is called the origin server. ICMP — Internet Control Message Protocol (ICMP) is one of the core protocols of the Internet protocol suite. It is chiefly used by networked computers' operating systems to test other systems and return error messages—indicating, for instance, that a requested service is not available or that a host or router could not be reached. IDS (Intrusion Detection System) — An IDS is software or an appliance used to detect unauthorized access or malicious or abnormal operation to a computer system or network. IDS systems that operate on a host to detect malicious activity are called host-based IDS systems or HIDS, and IDS systems that operate on network data flows are called network-based IDS systems or NIDS. IEC — International Electrotechnical Commission, is a European standards body which has developed IEC60870-5 series of SCADA protocols. IEC is now working on IEC-62351 a secure protocol envelope for DNP3 and IEC60870-5. IED (Intelligent Electronic Device) — A device on the network that contains an embedded system (an embedded system is a special-purpose computer system, which is completely encapsulated by the device it controls). Inter-Control Center Communications Protocol (ICCP) — A standard real- time network protocol for data exchange over wide area networks. ICCP is the most common communications protocol between RTO/ISO and control centers (aka, Telecontrol Application Service Element.2 (TASE.2)). IP (Internet Protocol) — A data-oriented protocol used by source and destination hosts for communicating data across a packet-switched internetwork. Data in an IP internetwork are sent in blocks referred to as packets or datagrams (the terms are basically synonymous in IP). IPS (Intrusion Prevention System) — Any hardware and/or software system that proactively exercises access control to protect computers from exploitation. "Intrusion prevention" technology is considered by some to be an extension of intrusion detection (IDS) 5/13/2010 Page 6 of 13
- 14. Control Systems Procurement & Maintenance Specifications Terms List technology, but it is actually another form of access control, like an application layer firewall, that uses knowledge of malicious behavior. IPSec — IPsec is a set of cryptographic protocols for securing packet flows and key exchange. Of the former, there are two: Encapsulating Security Payload (ESP) provides authentication, data confidentiality and message integrity; Authentication Header (AH) provides authentication and message integrity, but does not offer confidentiality. Originally AH was only used for integrity and ESP was used only for encryption; authentication functionality was added subsequently to ESP. IPv6 (Internet Protocol version 6) — IPv6 is version 6 of the Internet Protocol; IPv6 is intended to replace the current standard, IPv4. ISO (International Organization for Standardization) — The International Organization for Standardization, also known as ISO, is global network of the national standards bodies of 156 countries dedicated to technical standards development. L2TP — The Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol used to support virtual private networks (VPNs). L2TP can be described as "PPP over IP" with additional features. LAN (Local Area Network) — A LAN is a computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings (campus). LDAP — The Lightweight Directory Access Protocol, or LDAP, is a networking protocol for querying and modifying directory services running over TCP/IP. An LDAP directory usually follows the X.500 model: It is a tree of entries, each of which consists of a set of named attributes with values. LINUX — LINUX is a computer operating system. It is among the most famous examples of free software and of open-source development. MAC (Media Access Control) Address — A media access control address (MAC address) is a unique identifier attached to most forms of networking equipment. It is used at layer 2 of the OSI protocol. Most layer 2 network protocols use one of three numbering spaces managed by the IEEE: MAC-48, EUI-48, and EUI-64, which are designed to be globally unique. Malware — Malware is malicious software designed to infiltrate or damage a computer system, without the owner's consent. Malware is commonly taken to include computer viruses, worms, Trojan horses, rootkits, spyware and adware. 5/13/2010 Page 7 of 13
- 15. Control Systems Procurement & Maintenance Specifications Terms List MODEM — A modem is a device that modulates an analog carrier signal (sound), to encode digital information, and that also demodulates such a carrier signal to decode the transmitted information. NAT — NAT is the process of network address translation and involves re-writing the source and/or destination address of IP packets as they pass through a router or firewall. NAT is used to enable multiple hosts on a private network to access the Internet using a single public IP address. Network-based intrusion detection system (NIDS) — Application that reads all packets, not just those sent to it, from a network and detects potentially malicious packets based on rules or algorithms. Network Topology — Network topology is the network structure (logical and/or physical) that may be represented as a collection of nodes, some of which are connected by links. Bus topology: A bus network is such that there is a single line (the bus) to which all nodes are connected and the nodes connect only to this bus. Mesh topology: A network topology in which there are at least two nodes with two or more paths between them. Ring topology: A network topology in which every node has exactly two branches connected to it. Star topology: A network topology in which peripheral nodes are connected to a central node only when using a hub. The more commonly used switch does not rebroadcast to all nodes, including the originating node. Tree topology: A network topology in which the nodes are arranged as a tree. A hybrid topology is a combination of any two or more network topologies in such a way that the resulting network does not have one of the standard forms. Network File System (NFS) — NFS is a file system which allows a computer to access files over a network as easily as if they were on its local disks. NIDS — Network Intrusion Detection System is a hardware tool which monitors IP traffic on a network segment (or segments) to detect unauthorized access to a computer system or network. OPC (Open Connectivity via Open Standards) — OPC is open connectivity in industrial automation and the enterprise systems that support industry. Interoperability is assured through the creation and maintenance of open standards specifications. OPC has been termed “OLE for Process Control”. Open Systems Interconnection Reference Model (OSI) — The Open Systems Interconnection Reference Model is a layered abstract description for communications and computer network protocol design, developed as part of the Open Systems Interconnect initiative. It is also called the OSI seven layer model as follows: Physical layer Layer 1; Data link layer Layer 2; Network layer Layer 3; Transport layer Layer 4; Session layer Layer 5; Presentation layer Layer 6; Application layer Layer 7. 5/13/2010 Page 8 of 13
- 16. Control Systems Procurement & Maintenance Specifications Terms List Patch — A fix for a software program where the actual binary executable and related files are modified. PCI Express — PCI Express is an implementation of the PCI computer bus that uses existing PCI programming concepts and communications standards, but bases it on a much faster serial communications system. PCS (Process Control System) — A generic term applied to the hardware, firmware, communications, and software used to enable automation of the physical systems. PEAP — Protected Extensible Authentication Protocol, Protected EAP, or simply PEAP (pronounced "peep"), is a method to securely transmit authentication information, including passwords, over wireless networks. It was jointly developed by Microsoft, RSA Security and Cisco Systems. It is an IETF open standard. PID (Proportional-Integral-Derivative controller) — A standard feedback loop component in industrial control applications. It measures an "output" of a process and controls an "input", with a goal of maintaining the output at a target value, which is called the "setpoint". PLC (Programmable Logic Controller) — A small computer used for automation of real-world processes, such as control of machinery on factory assembly lines. Port — Hardware Port: A hardware port is an outlet on a piece of equipment into which a plug or cable connects. Network port: A network port is an interface for communicating with a computer program over a network. I/O or machine port - port-mapped I/O: Nearly all processor families use the same assembly instructions for both memory access and hardware I/O. Software port: Software is sometimes written for specific processors, operating systems, or programming interfaces. A software port is software that has been changed to work on another system. PPP — The Point-to-Point Protocol, or PPP, is commonly used to establish a direct connection between two nodes. It can connect computers using serial cable, phone line, trunk line, cellular telephone, specialized radio links, or fiber optic links. Most internet service providers use PPP for dial-up access to the Internet. Process Control — An engineering discipline that deals with architectures, mechanisms, and algorithms for controlling the output of a specific process. For example, heating up the temperature in a room is a process that has the specific, desired outcome to reach and maintain a defined temperature (e.g. 20°C), kept constant over time. Here, the temperature is the controlled variable. At the same time, it is the input variable since it is measured by a thermometer and used to decide whether to heat or not to heat. The desired temperature (20°C) is the set point. 5/13/2010 Page 9 of 13
- 17. Control Systems Procurement & Maintenance Specifications Terms List The state of the heater (e.g., the setting of the valve allowing hot water to circulate through it) is called the manipulated variable since it is subject to control actions. PROFIBUS (Process Field Bus) — PROFIBUS is the most popular type of fieldbus for factory and industrial automation with worldwide more than 10 million nodes (2004) in use. Proxy Server — Computer process – often used as, or as part of, a firewall – that relays a protocol between client and server computer systems, by appearing to the client to be the server and appearing to the server to be the client. PSTN (Public Switched Telephone Network) — The public telephone system in the United States used for voice and data communications. Public Key Infrastructure (PKI) — In cryptography, a public key infrastructure (PKI) is an arrangement using digital certificates which provides for third-party vetting of, and vouching for, user identities. QoS (Quality of Service) — In packet-switched networks QoS refers to the probability of the network meeting a given traffic contract, or in many cases is used informally to refer the probability of a packet passing between two points in the network. RADIUS — Remote Authentication Dial-In User Service is an authentication, authorization and accounting protocol for applications such as network access or IP mobility. It is intended to work in both local and roaming situations. The RADIUS server checks that the information is correct using authentication schemes like PAP, CHAP or EAP. RBAC (Role Based Access Control) — An approach to restricting system access to authorized users. It is a newer and alternative approach to Mandatory Access Control (MAC) and Discretionary Access Control (DAC). Rootkits — Rootkits are sets of programs which are introduced into a computer system without permission of the computer operator to obtain privileged access which would allow control of the computer, usually with capabilities to avoid detection. Router — A router is a computer networking device that forwards data packets toward their destinations between disparate networks through a process known as routing. Routing occurs at layer 3 of the OSI seven-layer model. Routers can implement other functions and the RTU (Remote Terminal Unit) — An RTU, or Remote Terminal Unit is a device which interfaces objects in the physical world to a DCS or SCADA system by transmitting telemetry data to the system and/or altering the state of connected objects based on control messages received from the system. 5/13/2010 Page 10 of 13
- 18. Control Systems Procurement & Maintenance Specifications Terms List SCADA (Supervisory Control and Data Acquisition) — A SCADA computer system is developed for gathering and analyzing real time data. SCADA systems are used to monitor and control a plant or equipment in industries such as telecommunications, water and waste control, energy, oil and gas refining and transportation. Serial Communications — Serial communications is the process of sending data one bit at one time, sequentially, over a communications channel or computer bus. Serial communications is used for all long-haul communications and most computer networks, where the cost of cable and synchronization difficulties makes parallel communications impractical. Serial computer busses are becoming more common as improved technology enables them to transfer data at higher speeds. Server — A server is a computer or device on a network that manages network resources. For example, a file server is a computer and storage device dedicated to storing files, a web server for access to web content, a DNS server for domain name services, a database server for access to relational tables, an email server for access to email, etc. Server Message Block (SMB) — Server Message Block (SMB) is a network protocol mainly applied to share files, printers, serial ports, and miscellaneous communications between nodes on a network. It also provides an authenticated Inter-process communication mechanism. Synchronous optical networking (SONET) — The Synchronous optical network, commonly known as SONET, is a standard for communicating digital information using lasers or light emitting diodes (LEDs) over optical fiber as defined by GR-253-CORE from Telcordia. SPP-ICS (System Protection Profile – Industrial Control Systems) — A document developed by the National Institute of Standards and Technology (NIST) that identifies a starting point for formally stating the security requirements for industrial control systems in a logical and structured manner. SSH — Secure Shell Terminal Emulation communications protocol widely used for remote RTU configuration/ diagnostic. SSID (Service Set Identifier) — A service set identifier (SSID) is a code attached to all packets on a wireless network to identify each packet as part of that network. SSL (Secure Sockets Layer) — Secure Sockets Layer (SSL) and Transport Layer Security (TLS), its successor, are cryptographic protocols which provide secure communications over TCP/IP. 5/13/2010 Page 11 of 13
- 19. Control Systems Procurement & Maintenance Specifications Terms List Stateful Firewall — A stateful firewall is a firewall that keeps track of the state of network connections (such as TCP streams) traveling across it. Source packets are entered into the state table. Response packets are checked against the state table and only those packets constituting a proper response are allowed through the firewall. Switch — A network switch is a computer networking device that serves as a connection point for devices in a network. A switch forwards packets to the appropriate port based on the packet’s address. TCP (Transmission Control Protocol) — TCP is one of the main protocols in TCP/IP networks. Whereas the IP protocol deals only with packets, TCP enables two hosts to establish a connection and exchange streams of data over many packets. TCP includes mechanisms and protocols to ensure delivery of the data in the correct sequence from source to destination. Telnet — Telenet is a terminal emulation communications protocol widely used for remote RTU configuration/ diagnostic. Telenet is being replaced by SSH. Terminal Server — A device used as an interface between Network (IP) communications and serial communication communications. TLS (Transport Layer Security) — See SSL. UDP (User Datagram Protocol) — UDP is a connection-less transport layer protocol that is currently documented in IETF RFC 768. In the TCP/IP model, UDP provides a very simple interface between a network layer below and an application layer above. UDP has no mechanism to ensure delivery of the data in the packets nor can it ensure that delivery of the packets is in the proper sequence. If desired, this must be performed by the application layer. Upgrade — Generally an upgrade is a new release of software, hardware and/or firmware replacing the original components to fix errors and/or vulnerabilities in software and/or provide additional functionality and/or improve performance. URL (Uniform Resource Locator) — URL is a standardized address for some resource (such as a document or image) on the Internet (or elsewhere). USB (Universal Serial Bus) — Universal Serial Bus (USB) provides a serial bus standard for connecting devices, usually to a computer, but it also is in use on other devices. Virus — See Malware. 5/13/2010 Page 12 of 13
- 20. Control Systems Procurement & Maintenance Specifications Terms List VLAN (Virtual LAN) — A virtual LAN, commonly known as a VLAN, is a logically segmented network mapped over physical hardware. VPN (Virtual Private Network) — A private, encrypted communications network usually used within a company, or by several different companies or organizations, used for communicating in a software tunnel over a public network. VoIP — Voice over Internet Protocol (also called VoIP, IP Telephony, Internet telephony, and Digital Phone) is the routing of voice conversations over the Internet or any other IP-based network. The voice data flows over a general-purpose packet-switched network, instead of traditional dedicated, circuit-switched voice transmission lines. WEP (Wired Equivalent Privacy) — WEP is part of the IEEE 802.11 standard, and is a protocol used to secure wireless networks (WiFi). WiFi (Wireless Fidelity) — Short for wireless fidelity and is meant to be used generically when referring of any type of 802.11 network, whether 802.11b/a/g dual-band, etc. WiMax (Worldwide Interoperability of Microwave Access) — WiMax is the name commonly given to the IEEE 802.16 standard. A wireless protocol designed for distances as far as 30 miles but more commonly 3 – 5 miles. WPA — Wi-Fi Protected Access (WPA and WPA2) are wireless standards providing higher levels of security than WEP. WPA2 is based on IEEE 802.11i and provides government grade security based on NIST standards and AES encryption. 5/13/2010 Page 13 of 13
- 21. Glossary This glossary is only a tiny subset of all of the various terms and other things that people regularly use on The Net. For a more complete (and very entertaining) reference, it's suggested you get a copy of The New Hacker's Dictionary, which is based on a VERY large text file called the Jargon File. Edited by Eric Raymond (eric@snark.thyrsus.com), it is available from the MIT Press, Cambridge, Massachusetts, 02142; its ISBN number is 0-262-68069-6. Also see RFC-1208, A Glossary of Networking Terms. :-) This odd symbol is one of the ways a person can portray ``mood'' in the very flat medium of computers---by using ``smilies.'' This is `metacommunication', and there are literally hundreds of them, from the obvious to the obscure. This particular example expresses ``happiness.'' Don't see it? Tilt your head to the left 90 degrees. Smilies are also used to denote sarcasm. address resolution Conversion of an Internet address to the corresponding physical address. On an ethernet, resolution requires broadcasting on the local area network. administrivia Administrative tasks, most often related to the maintenance of mailing lists, digests, news gateways, etc. anonymous FTP Also known as ``anon FTP''; a service provided to make files available to the general Internet community---see section Anonymous FTP. ANSI The American National Standards Institute disseminates basic standards like ASCII, and acts as the United States' delegate to the ISO. Standards can be ordered from ANSI by writing to the ANSI Sales Department, 1430 Broadway, New York, NY 10018, or by telephoning (212) 354- 3300. archie A service which provides lookups for packages in a database of the offerings of countless of anonymous FTP sites. See section The archie Server for a full description. archive server Page | 1
- 22. An email-based file transfer facility offered by some systems. ARPA (Advanced Research Projects Agency) Former name of DARPA, the government agency that funded ARPAnet and later the DARPA Internet. ARPAnet A pioneering long haul network funded by ARPA. It served as the basis for early networking research as well as a central backbone during the development of the Internet. The ARPAnet consisted of individual packet switching computers interconnected by leased lines. The ARPAnet no longer exists as a singular entity. asynchronous Transmission by individual bytes, not related to specific timing on the transmitting end. auto-magic Something which happens pseudo-automatically, and is usually too complex to go into any further than to say it happens ``auto-magically.'' backbone A high-speed connection within a network that connects shorter, usually slower circuits. Also used in reference to a system that acts as a ``hub'' for activity (although those are becoming much less prevalent now than they were ten years ago). bandwidth The capacity of a medium to transmit a signal. More informally, the mythical ``size'' of The Net, and its ability to carry the files and messages of those that use it. Some view certain kinds of traffic (FTPing hundreds of graphics images, for example) as a ``waste of bandwidth'' and look down upon them. BITNET (Because It's Time Network) An NJE-based international educational network. bounce The return of a piece of mail because of an error in its delivery. btw An abbreviation for ``by the way.'' Page | 2
- 23. CFV (Call For Votes) Initiates the voting period for a Usenet newsgroup. At least one (occasionally two or more) email address is customarily included as a repository for the votes. See See section Newsgroup Creation for a full description of the Usenet voting process. ClariNews The fee-based Usenet newsfeed available from ClariNet Communications. client The user of a network service; also used to describe a computer that relies upon another for some or all of its resources. Cyberspace A term coined by William Gibson in his fantasy novel Neuromancer to describe the ``world'' of computers, and the society that gathers around them. datagram The basic unit of information passed across the Internet. It contains a source and destination address along with data. Large messages are broken down into a sequence of IP datagrams. disassembling Converting a binary program into human-readable machine language code. DNS (Domain Name System) The method used to convert Internet names to their corresponding Internet numbers. domain A part of the naming hierarchy. Syntactically, a domain name consists of a sequence of names or other words separated by dots. dotted quad A set of four numbers connected with periods that make up an Internet address; for example, 147.31.254.130. email The vernacular abbreviation for electronic mail. email address Page | 3
- 24. The UUCP or domain-based address that a user is referred to with. For example, the author's address is brendan@cs.widener.edu. ethernet A 10-million bit per second networking scheme originally developed by Xerox Corporation. Ethernet is widely used for LANs because it can network a wide variety of computers, it is not proprietary, and components are widely available from many commercial sources. FDDI (Fiber Distributed Data Interface) An emerging standard for network technology based on fiber optics that has been established by ANSI. FDDI specifies a 100-million bit per second data rate. The access control mechanism uses token ring technology. flame A piece of mail or a Usenet posting which is violently argumentative. FQDN (Fully Qualified Domain Name) The FQDN is the full site name of a system, rather than just its hostname. For example, the system lisa at Widener University has a FQDN of lisa.cs.widener.edu. FTP (File Transfer Protocol) The Internet standard high-level protocol for transferring files from one computer to another. FYI An abbreviation for the phrase ``for your information.'' There is also a series of RFCs put out by the Network Information Center called FYIs; they address common questions of new users and many other useful things. See section Requests for Comments for instructions on retrieving FYIs. gateway A special-purpose dedicated computer that attaches to two or more networks and routes packets from one network to the other. In particular, an Internet gateway routes IP datagrams among the networks it connects. Gateways route packets to other gateways until they can be delivered to the final destination directly across one physical network. header The portion of a packet, preceding the actual data, containing source and destination addresses and error-checking fields. Also part of a message or news article. hostname Page | 4
- 25. The name given to a machine. (See also FQDN.) IMHO (In My Humble Opinion) This usually accompanies a statement that may bring about personal offense or strong disagreement. Internet A concatenation of many individual TCP/IP campus, state, regional, and national networks (such as NSFnet, ARPAnet, and Milnet) into one single logical network all sharing a common addressing scheme. Internet number The dotted-quad address used to specify a certain system. The Internet number for the site cs.widener.edu is 147.31.254.130. A resolver is used to translate between hostnames and Internet addresses. interoperate The ability of multi-vendor computers to work together using a common set of protocols. With interoperability, PCs, Macs, Suns, Dec VAXen, CDC Cybers, etc, all work together allowing one host computer to communicate with and take advantage of the resources of another. ISO (International Organization for Standardization) Coordinator of the main networking standards that are put into use today. kernel The level of an operating system or networking system that contains the system-level commands or all of the functions hidden from the user. In a Unix system, the kernel is a program that contains the device drivers, the memory management routines, the scheduler, and system calls. This program is always running while the system is operating. LAN (Local Area Network) Any physical network technology that operates at high speed over short distances (up to a few thousand meters). mail gateway A machine that connects to two or more electronic mail systems (especially dissimilar mail systems on two different networks) and transfers mail messages among them. mailing list Page | 5
- 26. A possibly moderated discussion group, distributed via email from a central computer maintaining the list of people involved in the discussion. mail path A series of machine names used to direct electronic mail from one user to another. medium The material used to support the transmission of data. This can be copper wire, coaxial cable, optical fiber, or electromagnetic wave (as in microwave). multiplex The division of a single transmission medium into multiple logical channels supporting many simultaneous sessions. For example, one network may have simultaneous FTP, telnet, rlogin, and SMTP connections, all going at the same time. net.citizen An inhabitant of Cyberspace. One usually tries to be a good net.citizen, lest one be flamed. netiquette A pun on ``etiquette''; proper behavior on The Net. See section Usenet ``Netiquette''. network A group of machines connected together so they can transmit information to one another. There are two kinds of networks: local networks and remote networks. NFS (Network File System) A method developed by Sun Microsystems to allow computers to share files across a network in a way that makes them appear as if they're ``local'' to the system. NIC The Network Information Center. node A computer that is attached to a network; also called a host. NSFnet The national backbone network, funded by the National Science Foundation and operated by the Merit Corporation, used to interconnect regional (mid-level) networks such as WestNet to one another. Page | 6
- 27. packet The unit of data sent across a packet switching network. The term is used loosely. While some Internet literature uses it to refer specifically to data sent across a physical network, other literature views the Internet as a packet switching network and describes IP datagrams as packets. polling Connecting to another system to check for things like mail or news. postmaster The person responsible for taking care of mail problems, answering queries about users, and other related work at a site. protocols A formal description of message formats and the rules two computers must follow to exchange those messages. Protocols can describe low-level details of machine-to-machine interfaces (e.g., the order in which bits and bytes are sent across a wire) or high-level exchanges between allocation programs (e.g., the way in which two programs transfer a file across the Internet). recursion The facility of a programming language to be able to call functions from within themselves. resolve Translate an Internet name into its equivalent IP address or other DNS information. RFD (Request For Discussion) Usually a two- to three-week period in which the particulars of newsgroup creation are battled out. route The path that network traffic takes from its source to its destination. router A dedicated computer (or other device) that sends packets from one place to another, paying attention to the current state of the network. RTFM (Read The Fantastic Manual) Page | 7
- 28. .This anacronym is often used when someone asks a simple or common question. The word `Fantastic' is usually replaced with one much more vulgar. SMTP (Simple Mail Transfer Protocol) The Internet standard protocol for transferring electronic mail messages from one computer to another. SMTP specifies how two mail systems interact and the format of control messages they exchange to transfer mail. server A computer that shares its resources, such as printers and files, with other computers on the network. An example of this is a Network File System (NFS) server which shares its disk space with other computers. signal-to-noise ratio When used in reference to Usenet activity, signal-to-noise ratio describes the relation between amount of actual information in a discussion, compared to their quantity. More often than not, there's substantial activity in a newsgroup, but a very small number of those articles actually contain anything useful. signature The small, usually four-line message at the bottom of a piece of email or a Usenet article. In Unix, it's added by creating a file .signature in the user's home directory. Large signatures are a no-no. summarize To encapsulate a number of responses into one coherent, usable message. Often done on controlled mailing lists or active newsgroups, to help reduce bandwidth. synchronous Data communications in which transmissions are sent at a fixed rate, with the sending and receiving devices synchronized. TCP/IP (Transmission Control Protocol/Internet Protocol) A set of protocols, resulting from ARPA efforts, used by the Internet to support services such as remote login (telnet), file transfer (FTP) and mail (SMTP). telnet Page | 8
- 29. The Internet standard protocol for remote terminal connection service. Telnet allows a user at one site to interact with a remote timesharing system at another site as if the user's terminal were connected directly to the remote computer. terminal server A small, specialized, networked computer that connects many terminals to a LAN through one network connection. Any user on the network can then connect to various network hosts. @TeX A free typesetting system by Donald Knuth. twisted pair Cable made up of a pair of insulated copper wires wrapped around each other to cancel the effects of electrical noise. UUCP (Unix to Unix Copy Program) A store-and-forward system, primarily for Unix systems but currently supported on other platforms (e.g. VMS and personal computers). WAN (Wide-Area Network) A network spanning hundreds or thousands of miles. workstation A networked personal computing device with more power than a standard IBM PC or Macintosh. Typically, a workstation has an operating system such as unix that is capable of running several tasks at the same time. It has several megabytes of memory and a large, high- resolution display. Examples are Sun workstations and Digital DECstations. worm A computer program which replicates itself. The Internet worm (see section The Internet Worm) was perhaps the most famous; it successfully (and accidentally) duplicated itself on systems across the Internet. wrt With respect to. Page | 9
