NIST 800-37 Certification & Accreditation Process
•Download as PPT, PDF•
3 likes•3,210 views
NIST 800-37 Certification & Accreditation Process
Report
Share
Report
Share
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Introduction to NIST’s Risk Management Framework (RMF)

Introduction to NIST’s Risk Management Framework (RMF)
Critical Security Controls v4 1 Mapped to NIST SP 800-53 Rev.4-final r6a

Critical Security Controls v4 1 Mapped to NIST SP 800-53 Rev.4-final r6a
Understanding the Risk Management Framework & (ISC)2 CAP Module 2: Introduction

Understanding the Risk Management Framework & (ISC)2 CAP Module 2: Introduction
Iso iec 27032 foundation - cybersecurity training course

Iso iec 27032 foundation - cybersecurity training course
Cybersecurity roadmap : Global healthcare security architecture

Cybersecurity roadmap : Global healthcare security architecture
NIST 800-30 Intro to Conducting Risk Assessments - Part 1

NIST 800-30 Intro to Conducting Risk Assessments - Part 1
Cybersecurity Priorities and Roadmap: Recommendations to DHS

Cybersecurity Priorities and Roadmap: Recommendations to DHS
Building a Cyber Security Operations Center for SCADA/ICS Environments

Building a Cyber Security Operations Center for SCADA/ICS Environments
Introduction to Risk Management via the NIST Cyber Security Framework

Introduction to Risk Management via the NIST Cyber Security Framework
(4) NIST SP 800-53 Revision 4 (security control enhancements omitted) 20140804

(4) NIST SP 800-53 Revision 4 (security control enhancements omitted) 20140804
Similar to NIST 800-37 Certification & Accreditation Process
Similar to NIST 800-37 Certification & Accreditation Process (20)
Understanding the Risk Management Framework & (ISC)2 CAP Module 4: Life Cycle

Understanding the Risk Management Framework & (ISC)2 CAP Module 4: Life Cycle
250250902-141-ISACA-NACACS-Auditing-IT-Projects-Audit-Program.pdf

250250902-141-ISACA-NACACS-Auditing-IT-Projects-Audit-Program.pdf
[Insert System Name (Acronym)]Security Categorization Moderat.docx![[Insert System Name (Acronym)]Security Categorization Moderat.docx](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Insert System Name (Acronym)]Security Categorization Moderat.docx](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Insert System Name (Acronym)]Security Categorization Moderat.docx
Navigating Process Safety Audits in the Oil and Gas Industry

Navigating Process Safety Audits in the Oil and Gas Industry
Understanding the Risk Management Framework & (ISC)2 CAP Module 9: Assess Con...

Understanding the Risk Management Framework & (ISC)2 CAP Module 9: Assess Con...
Recently uploaded
Recently uploaded (20)
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...

Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)

AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
NIST 800-37 Certification & Accreditation Process
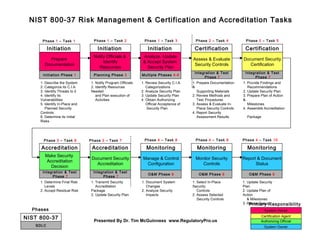
- 1. System Owner Authorizing Official Certification Agent Prepare Documentation Initiation Phase 1 1. Describe the System 2. Categorize its C.I.A. 3. Identify Threats to it 4. Identify its Vulnerabilities 5. Identify In-Place and Planned Security Controls 6. Determine its Initial Risks Initiation NIST 800-37 Risk Management & Certification and Accreditation Tasks Notify Officials & Identify Resources Planning Phase 3 1. Notify Program Officials 2. Identify Resources Needed and Plan execution of Activities Initiation Monitor Security Controls O&M Phase 9 1. Select In-Place Security Controls 2. Assess Selected Security Controls Monitoring Analyze, Update & Accept System Security Plan Multiple Phases 4-6 1. Review Security C.I.A. Categorizations 2. Analyze Security Plan 3. Update Security Plan 4. Obtain Authorizing Official Acceptance of Security Plan Initiation System Owner Phase 1 – Task 1 Phase 3 – Task 6 Phase 1 – Task 2 Phase 1 – Task 3 Phase 2 – Task 4 Phase 2 – Task 5 Phase 3 – Task 7 Phase 4 – Task 8 Phase 4 – Task 9 Phase 4 – Task 10 Primary Responsibility SDLC NIST 800-37 Phases Presented By Dr. Tim McGuinness www.RegulatoryPro.us Report & Document Status O&M Phase 9 1. Update Security Plan 2. Update Plan of Action & Milestones 3. Report Status Monitoring Manage & Control Configuration O&M Phase 9 1. Document System Changes 2. Analyze Security Impacts Monitoring Assess & Evaluate Security Controls Integration & Test Phase 7 1. Prepare Documentation & Supporting Materials 2. Review Methods and Test Procedures 3. Assess & Evaluate In- Place Security Controls 4. Report Security Assessment Results Certification Document Security Accreditation Integration & Test Phase 7 1. Transmit Security Accreditation Package 2. Update Security Plan Accreditation Document Security Certification Integration & Test Phase 7 1. Provide Findings and Recommendations 2. Update Security Plan 3. Prepare Plan of Action & Milestones 4. Assemble Accreditation Package Certification Make Security Accreditation Decision Integration & Test Phase 7 1. Determine Final Risk Levels 2. Accept Residual Risk Accreditation