Osi
•Download as PPTX, PDF•
1 like•298 views
Class Project References turned in.
Report
Share
Report
Share
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg

Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg
INTRODUCTION TO INTERNET PROTOCOL BY SAIKIRAN PANJALA

INTRODUCTION TO INTERNET PROTOCOL BY SAIKIRAN PANJALA
Slides for protocol layering and network applications

Slides for protocol layering and network applications
Viewers also liked
Viewers also liked (9)
Illustrating Freedom: 'Martin Luther King and the Montgomery Story' as a Rhet...

Illustrating Freedom: 'Martin Luther King and the Montgomery Story' as a Rhet...
Similar to Osi
Similar to Osi (20)
Manish Jha- Research Scholar- Internet Basics Requriement

Manish Jha- Research Scholar- Internet Basics Requriement
presentation on TCP/IP protocols data comunications

presentation on TCP/IP protocols data comunications
Recently uploaded
Recently uploaded (20)
Secure Zero Touch enabled Edge compute with Dell NativeEdge via FDO _ Brad at...

Secure Zero Touch enabled Edge compute with Dell NativeEdge via FDO _ Brad at...
Simplified FDO Manufacturing Flow with TPMs _ Liam at Infineon.pdf

Simplified FDO Manufacturing Flow with TPMs _ Liam at Infineon.pdf
Integrating Telephony Systems with Salesforce: Insights and Considerations, B...

Integrating Telephony Systems with Salesforce: Insights and Considerations, B...
Easier, Faster, and More Powerful – Notes Document Properties Reimagined

Easier, Faster, and More Powerful – Notes Document Properties Reimagined
Extensible Python: Robustness through Addition - PyCon 2024

Extensible Python: Robustness through Addition - PyCon 2024
Breaking Down the Flutterwave Scandal What You Need to Know.pdf

Breaking Down the Flutterwave Scandal What You Need to Know.pdf
Where to Learn More About FDO _ Richard at FIDO Alliance.pdf

Where to Learn More About FDO _ Richard at FIDO Alliance.pdf
How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf

How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf
Portal Kombat : extension du réseau de propagande russe

Portal Kombat : extension du réseau de propagande russe
Free and Effective: Making Flows Publicly Accessible, Yumi Ibrahimzade

Free and Effective: Making Flows Publicly Accessible, Yumi Ibrahimzade
Optimizing NoSQL Performance Through Observability

Optimizing NoSQL Performance Through Observability
Measures in SQL (a talk at SF Distributed Systems meetup, 2024-05-22)

Measures in SQL (a talk at SF Distributed Systems meetup, 2024-05-22)
Using IESVE for Room Loads Analysis - UK & Ireland

Using IESVE for Room Loads Analysis - UK & Ireland
A Business-Centric Approach to Design System Strategy

A Business-Centric Approach to Design System Strategy
The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf

The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf
Introduction to FDO and How It works Applications _ Richard at FIDO Alliance.pdf

Introduction to FDO and How It works Applications _ Richard at FIDO Alliance.pdf
Intro in Product Management - Коротко про професію продакт менеджера

Intro in Product Management - Коротко про професію продакт менеджера
Osi
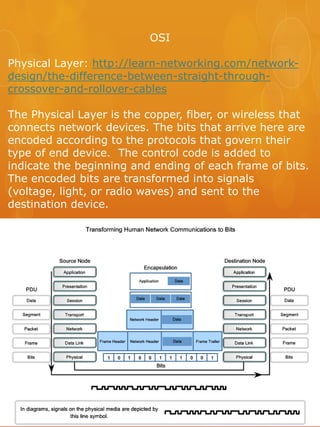
- 1. OSI Physical Layer: http://learn-networking.com/network- design/the-difference-between-straight-through- crossover-and-rollover-cables The Physical Layer is the copper, fiber, or wireless that connects network devices. The bits that arrive here are encoded according to the protocols that govern their type of end device. The control code is added to indicate the beginning and ending of each frame of bits. The encoded bits are transformed into signals (voltage, light, or radio waves) and sent to the destination device.
- 2. The Data-Link layer arranges the bits it receives into frames and provides synchronization, error control and flow control. It has two sub layers that are the logical link control and media access control. It begins the process of encapsulation and adds a trailer and header. The source and destination addresses are included along with frame check sequence values, quality of service, and type of protocol for whatever media is present. It links the hardware and software layers together.
- 3. Network Layer Translates addresses from logical to physical and visa- versa the other way. This is where addressing the networks and subnetting comes into play. Encapsulation of frames: IP header, source IP address, destination IP address. All available common network layer protocols. can’t wait! Dynamically done for me
- 4. Type of service determines the priority of the packet and looks for the Quality of Service to decide who goes first. EX: Voice transmits faster than e-mail. Time to Live ensures a packet can’t get stuck looping in to infinity. Protocol determines which type of data packet it is: ICMP, TCP, UDP The header checksum provides a security measure to make sure the data is exactly how it was from origination to destination. Packet Length is between
- 5. Routing: Carrying Data end to end:
- 9. Transport Layer: Visual Version
- 15. Source Port Address or name of remote host destination Port Connection State
- 30. The top three layers Application Layer: Is the first step to getting data onto the network. Three primary functions: 1. Coding and conversion of application layer data to ensure that data from the source device can be interpreted by the appropriate application on the destination device. 2. Compression of the data so that it can be decompressed by the destination device. 3. Encryption of the data for transmission and decryption of data by the destination device. Applications are computer programs with which the user interacts and that initiate the data transfer process at the user’s request. Services are background programs that provide the connection between the application layer and the lower layers of the networking model. The most widely-known TCP/IP Application layer protocols are those that provide for the exchange of user information. These protocols specify the format and control information necessary for many of the common Internet communication functions. Among these TCP/IP protocols are:
- 31. DNS: TCP/UDP port 53 Telnet: TCP port 23 SMTP:TCP port 25, POP:UDP port 110 DHDHCP: UDP port 67 port 80a TCP ports 20 and 21