La1 131209040938-phpapp02
•
0 recomendaciones•884 vistas
This document provides the criteria and instructions for a group presentation on the impact of information and communication technology (ICT) on society. Students must: 1. Locate information from more than one source on one of seven topics related to ICT and society. 2. Present the information in a 5-10 slide presentation covering the topic, content, and conclusions. 3. Submit a soft or hard copy of the presentation and display cooperation by including the names of group members or getting verbal confirmation from them.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (9)
Top Seven Risks of Enterprise Mobility - How to protect your business

Top Seven Risks of Enterprise Mobility - How to protect your business
Is the financial services industry vulnerable to constant cyber attacks

Is the financial services industry vulnerable to constant cyber attacks
IRJET - System to Identify and Define Security Threats to the users About The...

IRJET - System to Identify and Define Security Threats to the users About The...
Four Network Security Challenges for the Cloud Generation

Four Network Security Challenges for the Cloud Generation
Destacado
Destacado (20)
Similar a La1 131209040938-phpapp02
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updatesBriskinfosec Technology and Consulting
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updatesBriskinfosec Technology and Consulting
Similar a La1 131209040938-phpapp02 (20)
Security researchers participate in conferences such as DefCon t.docx

Security researchers participate in conferences such as DefCon t.docx
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates
2013 Italian Report on Cyber Security - Critical Infrastructure and other sen...

2013 Italian Report on Cyber Security - Critical Infrastructure and other sen...
Assignment 2 CybersecurityWe use computers and electronic systems.docx

Assignment 2 CybersecurityWe use computers and electronic systems.docx
CSE 2016 Future of Cyber Security by Matthew Rosenquist

CSE 2016 Future of Cyber Security by Matthew Rosenquist
G. Gritsai, A. Timorin, Y. Goltsev, R. Ilin, S. Gordeychik, and A. Karpin, “S...

G. Gritsai, A. Timorin, Y. Goltsev, R. Ilin, S. Gordeychik, and A. Karpin, “S...
UNDERSTANDING TRAFFIC PATTERNS OF COVID-19 IOC IN HUGE ACADEMIC BACKBONE NETW...

UNDERSTANDING TRAFFIC PATTERNS OF COVID-19 IOC IN HUGE ACADEMIC BACKBONE NETW...
STIX, TAXII, CISA: Impact of the Cybersecurity Information Sharing Act of 2015

STIX, TAXII, CISA: Impact of the Cybersecurity Information Sharing Act of 2015
Más de cikgushaharizan
Más de cikgushaharizan (17)
Último
Mattingly "AI & Prompt Design: Structured Data, Assistants, & RAG"

Mattingly "AI & Prompt Design: Structured Data, Assistants, & RAG"National Information Standards Organization (NISO)
“Oh GOSH! Reflecting on Hackteria's Collaborative Practices in a Global Do-It...

“Oh GOSH! Reflecting on Hackteria's Collaborative Practices in a Global Do-It...Marc Dusseiller Dusjagr
Organic Name Reactions for the students and aspirants of Chemistry12th.pptx

Organic Name Reactions for the students and aspirants of Chemistry12th.pptxVS Mahajan Coaching Centre
Último (20)
Z Score,T Score, Percential Rank and Box Plot Graph

Z Score,T Score, Percential Rank and Box Plot Graph
Separation of Lanthanides/ Lanthanides and Actinides

Separation of Lanthanides/ Lanthanides and Actinides
Call Girls in Dwarka Mor Delhi Contact Us 9654467111

Call Girls in Dwarka Mor Delhi Contact Us 9654467111
A Critique of the Proposed National Education Policy Reform

A Critique of the Proposed National Education Policy Reform
Beyond the EU: DORA and NIS 2 Directive's Global Impact

Beyond the EU: DORA and NIS 2 Directive's Global Impact
Mattingly "AI & Prompt Design: Structured Data, Assistants, & RAG"

Mattingly "AI & Prompt Design: Structured Data, Assistants, & RAG"
“Oh GOSH! Reflecting on Hackteria's Collaborative Practices in a Global Do-It...

“Oh GOSH! Reflecting on Hackteria's Collaborative Practices in a Global Do-It...
TataKelola dan KamSiber Kecerdasan Buatan v022.pdf

TataKelola dan KamSiber Kecerdasan Buatan v022.pdf
Organic Name Reactions for the students and aspirants of Chemistry12th.pptx

Organic Name Reactions for the students and aspirants of Chemistry12th.pptx
Privatization and Disinvestment - Meaning, Objectives, Advantages and Disadva...

Privatization and Disinvestment - Meaning, Objectives, Advantages and Disadva...
La1 131209040938-phpapp02
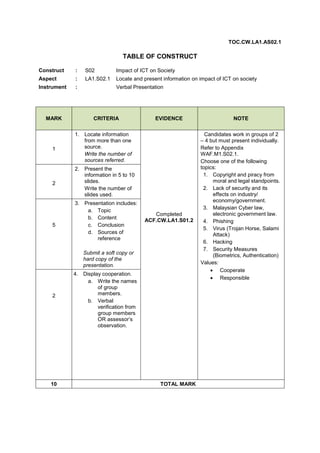
- 1. TOC.CW.LA1.AS02.1 TABLE OF CONSTRUCT Construct : S02 Impact of ICT on Society Aspect : LA1.S02.1 Locate and present information on impact of ICT on society Instrument : MARK Verbal Presentation CRITERIA 1 NOTE Completed ACF.CW.LA1.S01.2 SCandidates work in groups of 2 – 4 but must present individually. Refer to Appendix WAF.M1.S02.1. Choose one of the following topics: 1. Copyright and piracy from moral and legal standpoints. 2. Lack of security and its effects on industry/ economy/government. 3. Malaysian Cyber law, electronic government law. 4. Phishing 5. Virus (Trojan Horse, Salami Attack) 6. Hacking 7. Security Measures (Biometrics, Authentication) Values: Cooperate Responsibleuggested anti-spyware software: Lavasoft Ad-Aware SE Personal. 1. Locate information from more than one source. Write the number of sources referred. 2 EVIDENCE 2. Present the information in 5 to 10 slides. Write the number of slides used. 5 3. Presentation includes: a. Topic b. Content c. Conclusion d. Sources of reference Submit a soft copy or hard copy of the presentation. 2 4. Display cooperation. a. Write the names of group members. b. Verbal verification from group members OR assessor’s observation. Print screen can be used to display scan summary. If no spyware is detected, criterion four is considered done. Write “No action taken”. Values: Confident Responsible 10 TOTAL MARK