2012 mdsp pr11 ica part 2 face recognition
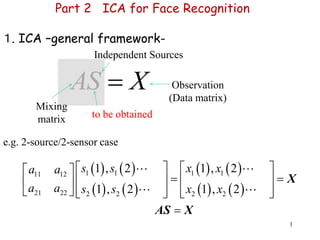
- 1. 1 Part 2 ICA for Face Recognition 1. ICA –general framework- e.g. 2-source/2-sensor case AS X Mixing matrix Independent Sources Observation (Data matrix) to be obtained 1 1 1 111 12 21 22 2 2 2 2 1 , 2 1 , 2 1 , 2 1 , 2 s s x xa a a a s s x x X AS X
- 2. 2 1 2 1 1 1 2 2 2 Data Matrix 1 2 1 2 , , 1 2 T T T N N N N x x x M x x x M x x x M x x X = x 1st image 2nd image 1st pixel 2nd pixel N-th image The last pixel N face images
- 3. as a solution which has two ambiguities on the order and the scale of the real source images ICA gives , where Permutation scale S U = WX S = PDU P D Reference [2]
- 4. 4 2. Face Recognition by ICA [Training set of face images: FERET database] For a given ensemble of N (425) training face images with M(=3000) dimensional vectors with zero mean and its data matrix X as in the first part. { , 1 }n n Nx 1 N u U WX u 1 2 Face image matrix T T T N X x x = x face 1 face 2 ICA 3000-dim. 425-dim.
- 5. 5 Remarks - Row vectors ui (i=1~N) would be as statistically independent as possible, the obtained these row vectors are the basis images to represent faces. - One problem is the number of independent images will become quite large because it is equal to the number of faces of training database. - One solution is apply PCA prior to ICA for dimensionality reduction. [Feature vector of training faces] 1 11 12 2 . . 21 22 1 1 2 2 1 2 th face: of -th face image train train N T i i i iN N train i i i iN b b b b i b b b i b b b Feature vector u u X B U u x u u u b
- 6. Reference [2] Statistically Independent Component Basis Images (25 images) which provide local features. As shown in this Figure, ICA images are local.
- 7. 7
- 8. PCA Basis Images from the same training faces as in [2]. The order of the principal components starts from left to right, top to bottom. Reference [2]
- 9. 9 1train T b z U Representation of test images z: feature vectors of test face , length-normalized evaluation test train i i test train i c b b b b test image: z 1test T U b z Identification of the test face: pattern recognition Define the similarity measure (cosine of the angle) between two faces .-th row oftrain i trainib B The best fit face image = arg Max i i c similarity measure (cosine of the angle) training images
- 10. 10 Reference [2]
- 11. 11 References (Part 2) [1] A. J. Bell and T J. Srjnowski, The “Independent Components” of Natural Scene are Edge Filters: Vision Research, Vol. 37, No. 23, pp. 3327-3338, 1997. [2] M. S. Bartlett et al. “ Face recognition by Independent Component Analysis,” IEEE. Trans on Neural Networks, Vol. 13, No. 6, Nov., 2002 [3] A. Hyvarinen et al. “Independent Component Analysis” , Wiley-InterScience, 2001 [4] B. A. Draper et al. , “Recognizing faces with PCA and ICA,” Computer Vision and Image Understanding, vol. 91, pp. 115-137, 2003. 1, Jan. 2004
- 12. 12