Osi
•Descargar como PPTX, PDF•
1 recomendación•298 vistas
Class Project References turned in.
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg

Networking Essentials Lesson 02 - Standards and OSI - Eric Vanderburg
INTRODUCTION TO INTERNET PROTOCOL BY SAIKIRAN PANJALA

INTRODUCTION TO INTERNET PROTOCOL BY SAIKIRAN PANJALA
Slides for protocol layering and network applications

Slides for protocol layering and network applications
Destacado
Destacado (9)
Illustrating Freedom: 'Martin Luther King and the Montgomery Story' as a Rhet...

Illustrating Freedom: 'Martin Luther King and the Montgomery Story' as a Rhet...
Similar a Osi
Similar a Osi (20)
Manish Jha- Research Scholar- Internet Basics Requriement

Manish Jha- Research Scholar- Internet Basics Requriement
presentation on TCP/IP protocols data comunications

presentation on TCP/IP protocols data comunications
Último
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Último (20)
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
CNIC Information System with Pakdata Cf In Pakistan

CNIC Information System with Pakdata Cf In Pakistan
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Spring Boot vs Quarkus the ultimate battle - DevoxxUK

Spring Boot vs Quarkus the ultimate battle - DevoxxUK
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...

Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...
Osi
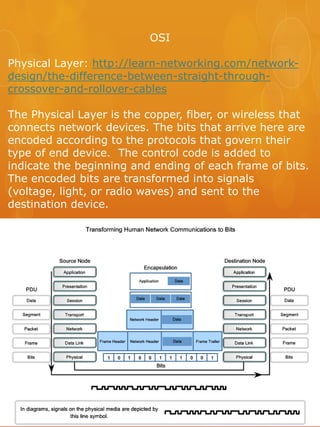
- 1. OSI Physical Layer: http://learn-networking.com/network- design/the-difference-between-straight-through- crossover-and-rollover-cables The Physical Layer is the copper, fiber, or wireless that connects network devices. The bits that arrive here are encoded according to the protocols that govern their type of end device. The control code is added to indicate the beginning and ending of each frame of bits. The encoded bits are transformed into signals (voltage, light, or radio waves) and sent to the destination device.
- 2. The Data-Link layer arranges the bits it receives into frames and provides synchronization, error control and flow control. It has two sub layers that are the logical link control and media access control. It begins the process of encapsulation and adds a trailer and header. The source and destination addresses are included along with frame check sequence values, quality of service, and type of protocol for whatever media is present. It links the hardware and software layers together.
- 3. Network Layer Translates addresses from logical to physical and visa- versa the other way. This is where addressing the networks and subnetting comes into play. Encapsulation of frames: IP header, source IP address, destination IP address. All available common network layer protocols. can’t wait! Dynamically done for me
- 4. Type of service determines the priority of the packet and looks for the Quality of Service to decide who goes first. EX: Voice transmits faster than e-mail. Time to Live ensures a packet can’t get stuck looping in to infinity. Protocol determines which type of data packet it is: ICMP, TCP, UDP The header checksum provides a security measure to make sure the data is exactly how it was from origination to destination. Packet Length is between
- 5. Routing: Carrying Data end to end:
- 9. Transport Layer: Visual Version
- 15. Source Port Address or name of remote host destination Port Connection State
- 30. The top three layers Application Layer: Is the first step to getting data onto the network. Three primary functions: 1. Coding and conversion of application layer data to ensure that data from the source device can be interpreted by the appropriate application on the destination device. 2. Compression of the data so that it can be decompressed by the destination device. 3. Encryption of the data for transmission and decryption of data by the destination device. Applications are computer programs with which the user interacts and that initiate the data transfer process at the user’s request. Services are background programs that provide the connection between the application layer and the lower layers of the networking model. The most widely-known TCP/IP Application layer protocols are those that provide for the exchange of user information. These protocols specify the format and control information necessary for many of the common Internet communication functions. Among these TCP/IP protocols are:
- 31. DNS: TCP/UDP port 53 Telnet: TCP port 23 SMTP:TCP port 25, POP:UDP port 110 DHDHCP: UDP port 67 port 80a TCP ports 20 and 21