Workshop on Cryptography - Frequency Analysis (basic)
•
1 recomendación•236 vistas
Substitution cyphers: why they should not be used & how to crack them
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
Similar a Workshop on Cryptography - Frequency Analysis (basic)
Similar a Workshop on Cryptography - Frequency Analysis (basic) (20)
Secret-Key-Cryptography-ppt-by-alljobs.co_.in_.pptx

Secret-Key-Cryptography-ppt-by-alljobs.co_.in_.pptx
cryptography presentation this about how cryptography works

cryptography presentation this about how cryptography works
Más de Andrea Tino
Más de Andrea Tino (20)
Master Thesis - A Distributed Algorithm for Stateless Load Balancing

Master Thesis - A Distributed Algorithm for Stateless Load Balancing
Designing an effective hybrid apps automation framework

Designing an effective hybrid apps automation framework
Último
Model Call Girl Services in Delhi reach out to us at 🔝 9953056974🔝✔️✔️ Our agency presents a selection of young, charming call girls available for bookings at Oyo Hotels. Experience high-class escort services at pocket-friendly rates, with our female escorts exuding both beauty and a delightful personality, ready to meet your desires. Whether it's Housewives, College girls, Russian girls, Muslim girls, or any other preference, we offer a diverse range of options to cater to your tastes. We provide both in- call and out-call services for your convenience. Our in-call location in Delhi ensures cleanliness, hygiene, and 100% safety, while our out-call services offer doorstep delivery for added ease. We value your time and money, hence we kindly request pic collectors, time-passers, and bargain hunters to refrain from contacting us. Our services feature various packages at competitive rates: One shot: ₹2000/in-call, ₹5000/out-call Two shots with one girl: ₹3500 /in-call, ₱6000/out-call Body to body massage with sex: ₱3000/in-call Full night for one person: ₱7000/in-call, ₱10000/out-call Full night for more than 1 person : Contact us at 🔝 9953056974🔝. for details Operating 24/7, we serve various locations in Delhi, including Green Park, Lajpat Nagar, Saket, and Hauz Khas near metro stations. For premium call girl services in Delhi 🔝 9953056974🔝. Thank you for considering us Call Girls in South Ex (delhi) call me [🔝9953056974🔝] escort service 24X7![Call Girls in South Ex (delhi) call me [🔝9953056974🔝] escort service 24X7](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Call Girls in South Ex (delhi) call me [🔝9953056974🔝] escort service 24X7](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Call Girls in South Ex (delhi) call me [🔝9953056974🔝] escort service 24X79953056974 Low Rate Call Girls In Saket, Delhi NCR
From customer value engagements to hands-on production support, our Services span across every stage of our customers digital transformation journey, to help ensure that every customer is successful in their adoption of our solutions.
• Implementation, Upgrade, Migration, and Maintenance Services
• On-Premises and On-Cloud
• COTS Training Services; On-Site and Virtual
• Software Support Services; Legacy and 3DEXPERIENCE
• Value Engagement & Blueprinting
• Specialized Consulting and Support Services
• Customized Training Services
• Automation and Configuration Services
• Technical Resource Augmentation Services
• Project Management
• Know-how Training (mentoring) and Resource AugmentationNavigating Complexity: The Role of Trusted Partners and VIAS3D in Dassault Sy...

Navigating Complexity: The Role of Trusted Partners and VIAS3D in Dassault Sy...Arindam Chakraborty, Ph.D., P.E. (CA, TX)
Último (20)
Kuwait City MTP kit ((+919101817206)) Buy Abortion Pills Kuwait

Kuwait City MTP kit ((+919101817206)) Buy Abortion Pills Kuwait
Standard vs Custom Battery Packs - Decoding the Power Play

Standard vs Custom Battery Packs - Decoding the Power Play
+97470301568>> buy weed in qatar,buy thc oil qatar,buy weed and vape oil in d...

+97470301568>> buy weed in qatar,buy thc oil qatar,buy weed and vape oil in d...
Block diagram reduction techniques in control systems.ppt

Block diagram reduction techniques in control systems.ppt
Bhubaneswar🌹Call Girls Bhubaneswar ❤Komal 9777949614 💟 Full Trusted CALL GIRL...

Bhubaneswar🌹Call Girls Bhubaneswar ❤Komal 9777949614 💟 Full Trusted CALL GIRL...
Call Girls in South Ex (delhi) call me [🔝9953056974🔝] escort service 24X7![Call Girls in South Ex (delhi) call me [🔝9953056974🔝] escort service 24X7](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Call Girls in South Ex (delhi) call me [🔝9953056974🔝] escort service 24X7](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Call Girls in South Ex (delhi) call me [🔝9953056974🔝] escort service 24X7
Double Revolving field theory-how the rotor develops torque

Double Revolving field theory-how the rotor develops torque
Design For Accessibility: Getting it right from the start

Design For Accessibility: Getting it right from the start
Navigating Complexity: The Role of Trusted Partners and VIAS3D in Dassault Sy...

Navigating Complexity: The Role of Trusted Partners and VIAS3D in Dassault Sy...
Cara Menggugurkan Sperma Yang Masuk Rahim Biyar Tidak Hamil

Cara Menggugurkan Sperma Yang Masuk Rahim Biyar Tidak Hamil
Hazard Identification (HAZID) vs. Hazard and Operability (HAZOP): A Comparati...

Hazard Identification (HAZID) vs. Hazard and Operability (HAZOP): A Comparati...
Workshop on Cryptography - Frequency Analysis (basic)
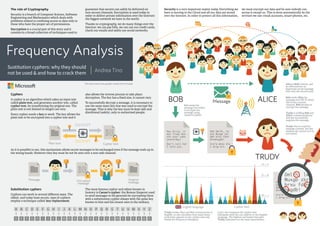
- 1. Sustitution cyphers: why they should not be used & and how to crack them Frequency Analysis Andrea Tino This document uses graphic assets from Freepik Cyphers A cypher is an algorithm which takes an input text called plain text, and generates another text, called cypher text, by transforming the priginal one. The plain text is not limited its length can vary. Every cypher needs a key to work. The key allows the plain text to be encrypted into a cypher text and it The role of Cryptography Security is a branch of Computer Science, So ware Engineering and Mathematics which deals with problems related to confining access to data only to those who have the proper set of permissions. Encryption is a crucial part of this story and it consists in a broad collection of techniques used to guarantee that secrets can safely be delivered on non-secure channels. Encryption is used today in order to deliver private information over the Internet: the biggest network we have in the world. Thanks to cryptography, we do many things over the Internet: we can pay bills, we can use our credit cards, check our emails and safely use social networks. Security is a very important ma er today. Everything we have is moving to the Cloud and all our data are stored over the Internet. In order to protect all this information, Substitution cyphers Cyphers can work in several different ways. The oldest, and today least secure, type of cyphers employ a technique called: key-replacement. also allows the reverse process to take place: decryption. The key has a fixed size, it cannot vary. To successfully decrypt a message, it is necessary to use the same exact key that was used to encrypt the message. That is why the key must be kept safe and distributed (safely), only to authorized people. The most famous cypher and oldest known in hostory is Caesar’s cypher: the Roman Emperor used to send messages to his generals by encrypting them with a substitution cypher always with the same key known to him and his closest men in the military. As it is possible to see, this mechanism allows secret messages to be exchanged even if the message ends up in the wrong hands. However they key must be not be sent over a non-safe channel. we must encrypt our data and be sure nobody can access it except us. This is done automatically by the services we use: email accounts, smart-phones, etc. A B C D E F G H I J K L M N O P Q R S T U V W X Y Z A B CD E F G H I J K L M N O P Q R S T U V W X Y Z Plain text #$%!?+0^!@ ?+0^!!?+0^ !@?+0^!?+0 ^!@?+0^!!@ #$%!!?+0^! Cypher text ENCRYPT DECRYPT ALICEBOB Message Message #$%!?+0^!@ ?+0^!!?+0^ !@?+0^!?+0 ^!@?+0^!!@ #$%!!?+0^! Encrypted message Original message TRUDY Hey Alice, it was Trudy who ate your cake yesterday! Don’t tell her I told you. Khb Dmlfh, lw zdv Wuxgb zkr dwh brxu fdnh bhvwhugdb! Grq’w whoo khu L wrog brx. Bob sends the message but before it encrypts the message using Caesar’s Cypher. Khb Dmlfh, lw zdv Wuxgb zkr dwh brxu fdnh bhvwhugdb! Grq’w whoo khu L wrog brx. Khb Dmlfh, lw zdv Wuxgb zkr dwh brxu fdnh bhvwhugdb! Grq’w whoo khu L wrog brx. Bob sends Alice the message over Wi-Fi. Since this is not a secure channel, Bob decides to encrypt the message. Trudy is sniffing Bob and Alice’s communications and she successfully acquires the message. Alice is Bob’s friend, and he will send her an important secret message that only she should read. Trudy tries to read the message content, but she realizes she cannot as it is encrypted. E F G H J MA B C DE F G I J OA B C D English language Cypher text D = A H = E M = J Trudy knows Alice and Bob communicate in English, so she calculates how many times each le er appears in the cypher-text and builds the frequency histogram. Later, she compares the cypher-text histogram with the one relative to the English language. The highest and lowest bars give Trudy indication on the main associations.
