mm CGEIT Best Practices and Concepts
•
2 recomendaciones•737 vistas
CGEIT: Best Practices and Concepts
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Cybersecurity using NIST Cybersecurity Framework and COBIT 5Diskusi buku: Securing an IT Organization through Governance, Risk Management...

Diskusi buku: Securing an IT Organization through Governance, Risk Management...Sarwono Sutikno, Dr.Eng.,CISA,CISSP,CISM,CSX-F
Recomendados
Cybersecurity using NIST Cybersecurity Framework and COBIT 5Diskusi buku: Securing an IT Organization through Governance, Risk Management...

Diskusi buku: Securing an IT Organization through Governance, Risk Management...Sarwono Sutikno, Dr.Eng.,CISA,CISSP,CISM,CSX-F
Usulan SNI pada Komisi Teknik 35-01 Teknologi Informasi, bagian Kelompok Kerja Keamanan Informasi WG1 dan bagian Kelompok Kerja Manajemen Layanan dan Tata Kelola Teknologi Informasi WG2, Program Nasional Penetapan Standar BSN KemkominfoUsulan untuk wg1 dan wg2 pada pnps2015 rapat awal pt35-01 - 9 april 2015

Usulan untuk wg1 dan wg2 pada pnps2015 rapat awal pt35-01 - 9 april 2015Sarwono Sutikno, Dr.Eng.,CISA,CISSP,CISM,CSX-F
Más contenido relacionado
Destacado
Destacado (17)
пр Что ожидают работодатели от молодых специалистов

пр Что ожидают работодатели от молодых специалистов
UEBA – поведенческий анализ, а не то, что Вы подумали

UEBA – поведенческий анализ, а не то, что Вы подумали
Similar a mm CGEIT Best Practices and Concepts
Usulan SNI pada Komisi Teknik 35-01 Teknologi Informasi, bagian Kelompok Kerja Keamanan Informasi WG1 dan bagian Kelompok Kerja Manajemen Layanan dan Tata Kelola Teknologi Informasi WG2, Program Nasional Penetapan Standar BSN KemkominfoUsulan untuk wg1 dan wg2 pada pnps2015 rapat awal pt35-01 - 9 april 2015

Usulan untuk wg1 dan wg2 pada pnps2015 rapat awal pt35-01 - 9 april 2015Sarwono Sutikno, Dr.Eng.,CISA,CISSP,CISM,CSX-F
Kualitas Data adalah inti dasar informasi sebagai lifeline selain keuangan dalam jaman cyber. Seri ISO 8000 akan sebanding dengan seri ISO 9000 Sistem Manajemen Kualitas (QMS). Seri ISO 8000 baru berkembang dan akan menjadi arus utama dalam waktu dekat dan akan menjadi dasar pengolahan informasi untuk pengambilan keputusan.Usulan untuk wg1 dan wg2 serta kualitas data pada pnps2015 rapat ke-2 pt35-...

Usulan untuk wg1 dan wg2 serta kualitas data pada pnps2015 rapat ke-2 pt35-...Sarwono Sutikno, Dr.Eng.,CISA,CISSP,CISM,CSX-F
Similar a mm CGEIT Best Practices and Concepts (20)
Usulan untuk wg1 dan wg2 pada pnps2015 rapat awal pt35-01 - 9 april 2015

Usulan untuk wg1 dan wg2 pada pnps2015 rapat awal pt35-01 - 9 april 2015
Usulan untuk wg1 dan wg2 serta kualitas data pada pnps2015 rapat ke-2 pt35-...

Usulan untuk wg1 dan wg2 serta kualitas data pada pnps2015 rapat ke-2 pt35-...
Qwr iso20000 auditor m04 implementing audit and tooling us 06 apr14

Qwr iso20000 auditor m04 implementing audit and tooling us 06 apr14
CMMI for Services v2.0 Changes, Practice Areas, Appraisals

CMMI for Services v2.0 Changes, Practice Areas, Appraisals
How Your Organization Can Become ISO Certified...It's easier than you think

How Your Organization Can Become ISO Certified...It's easier than you think
Más de Andrey Prozorov, CISM, CIPP/E, CDPSE. LA 27001
NIST Cybersecurity Framework (CSF) 2.0: What has changed?NIST Cybersecurity Framework (CSF) 2.0: What has changed?

NIST Cybersecurity Framework (CSF) 2.0: What has changed?Andrey Prozorov, CISM, CIPP/E, CDPSE. LA 27001
My presentation from XMind's webinar, "My 15 Years of Experience in Using Mind Maps for Business and Personal Purposes"My 15 Years of Experience in Using Mind Maps for Business and Personal Purposes

My 15 Years of Experience in Using Mind Maps for Business and Personal PurposesAndrey Prozorov, CISM, CIPP/E, CDPSE. LA 27001
ISO 27001 Implementation ToolkitISO 27001 How to use the ISMS Implementation Toolkit.pdf

ISO 27001 How to use the ISMS Implementation Toolkit.pdfAndrey Prozorov, CISM, CIPP/E, CDPSE. LA 27001
Más de Andrey Prozorov, CISM, CIPP/E, CDPSE. LA 27001 (20)
NIST Cybersecurity Framework (CSF) 2.0: What has changed?

NIST Cybersecurity Framework (CSF) 2.0: What has changed?
My 15 Years of Experience in Using Mind Maps for Business and Personal Purposes

My 15 Years of Experience in Using Mind Maps for Business and Personal Purposes
ISO 27001 How to use the ISMS Implementation Toolkit.pdf

ISO 27001 How to use the ISMS Implementation Toolkit.pdf
ISO 27001 How to accelerate the implementation.pdf

ISO 27001 How to accelerate the implementation.pdf
All about a DPIA by Andrey Prozorov 2.0, 220518.pdf

All about a DPIA by Andrey Prozorov 2.0, 220518.pdf
Último
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Último (20)
Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model

Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
mm CGEIT Best Practices and Concepts
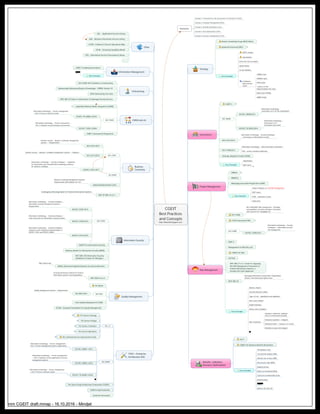
- 1. CGEIT Best Practices and Concepts http://80na20.blogspot.com Strategy Boston Consulting Group (BSG) Matrix Balanced Scorecard (BSC) Key Concepts SWOT analysis Gap Analysis Porter five forces analysis Ansoff Matrix Jo-Hari Window Continuous Improvement Cycles DMAIC Cycle DMADV Cycle PDCA Cycle 7 phases of the Implementation Life Cycle Boyd Cycle (OODA) Agility Loops Governance COBIT 5 ISO 38500 ISO/IEC 38500:2015 Information technology -- Governance of IT for the organization ISO/IEC TR 38502:2014 Information technology -- Governance of IT -- Framework and model ISO 27014:2013 Information technology -- Security techniques -- Governance of information security ISO 17998:2012 Information technology -- SOA Governance Framework SOA - service-oriented architecture Strategic alignment model (SAM) Key Concepts Stakeholders RACI charts Project Management PMBoK PRINCE2 Managing Successful Programmes (MSP) Key Concepts Project, Program, & Portfolio Management PERT charts SOW – statement of work Gantt chart Risk Management ISO 31000 ISO 31000:2009, Risk management – Principles and guidelines, provides principles, framework and a process for managing risk. COSO Framework ERM ISO 27005 ISO/IEC 27005:2011 Information technology -- Security techniques -- Information security risk management RISK IT Management of Risk (M_o_R) COBIT5 for Risk OCTAVE NIST 800-37 rev.1 Guide for Applying the Risk Management Framework to Federal Information Systems: a Security Life Cycle Approach NIST 800-39 Managing Information Security Risk: Organization, Mission, and Information System View Key Concepts Business Impact Key Risk Indicators (KRIs) Types of risk – quantitative and qualitative Root cause analysis Delphi technique Monte Carlo simulation Risk Treatments Avoidance (eliminate, withdraw from or not become involved) Reduction (optimize – mitigate) Sharing (transfer – outsource or insure) Retention (accept and budget) ... Benefits realization, Resource Optimization Val IT COBIT5 for Business Benefits Realization Key Concepts The Business Case Cost-benefit analysis (CBA) Internal rate of return (IRR) Net present value (NPV) Payback period Retorn on investment (ROI) Total Cost of Ownership (TCO) Benchmarking SMART Metrics, KPI, KGI, CSF ITSM + Enterprise Architecture (EA) ITIL v3 ITIL Service Strategy ITIL Service Design ITIL Service Transition ITIL Service Operation ITIL Continual Service Improvement (CSI) ISO 20000 ISO/IEC 20000-1:2011 Information technology -- Service management -- Part 1: Service management system requirements ISO/IEC 20000-2:2012 Information technology -- Service management -- Part 2: Guidance on the application of service management systems ISO/IEC TR 20000-4:2010 Information technology -- Service management -- Part 4: Process reference model ... The Open Group Architecture Framework (TOGAF) COBIT5 Implementation Zachman Framework Quality Management Six Sigma ISO 9001ISO 9001:2015 Quality management systems -- Requirements Total Quality Management (TQM) EFQM - European Foundation for Quality Management Information Security ISO 27001 ISO/IEC 27001:2013 Information technology -- Security techniques -- Information security management systems -- Requirements ISO/IEC 27002:2013 Information technology -- Security techniques -- Code of practice for information security controls ISO/IEC 27013:2015 Information technology -- Security techniques -- Guidance on the integrated implementation of ISO/IEC 27001 and ISO/IEC 20000-1 ... COBIT5 for Information Security Business Model for Information Security (BMIS) NIST 800-100 Information Security Handbook: A Guide for Managers SABSA (Sherwood Applied Business Security Architecture http://sabsa.org/ NIST 800-53 rev.4 Security and Privacy Controls for Federal Information Systems and Organizations Business Continuity ISO 22301 ISO 22301:2012 Societal security -- Business continuity management systems --- Requirements ISO 22313:2012 Societal security -- Business continuity management systems -- Guidance ISO/IEC 27031:2011 Information technology -- Security techniques -- Guidelines for information and communication technology readiness for business continuity BS 25999 ANSI/ASIS/BSI BCM.01.2010 Business Continuity Management Systems: Requirements with Guidance for Use NIST SP 800-34 rev.1 Contingency Planning Guide for Federal Information Systems CMMI and etc Capability Maturity Model Integration (CMMI) ISO 15504 ISO/IEC TR 20000-4:2010 Information technology -- Service management -- Part 4: Process reference model ISO/IEC 15504-3:2004 Information technology -- Process assessment -- Part 3: Guidance on performing an assessment COBIT 5 Assessment Programme Outsoursing ISO 37500-2014 Guidance on outsourcing Outsourcing Professional Body of Knowledge - OPBOK Version 10 NOA Outsourcing Life Cycle NIST 800-35 Guide to Information Technology Security Services Information Management COBIT 5 Enabling Information Key Concepts DIKW Other ASL - Application Services Library BiSL - Business Information Services Library eTOM - Enhanced Telecom Operations Map eSCM - eSourcing Capability Model ISPL - Information Services Procurement Library ... Domains Domain 1: Framework for the Governance of Enterprise IT (25%) Domain 2: Strategic Management (20%) Domain 3: Benefits Realization (16%) Domain 4: Risk Optimization (24%) Domain 5: Resource Optimization (15%) mm CGEIT draft.mmap - 16.10.2016 - Mindjet
