Ransomware
•
1 recomendación•1,283 vistas
Ransomware type of malware which restricts access to the computer system that it infects, and demands a ransom paid to the creator(s) of the malware in order for the restriction to be removed. It deliberately locks you out of your computer or your files, and then demands money to let you back in. Basic information how, why, where etc.
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Malware's Most Wanted: CryptoLocker—The Ransomware Trojan

Malware's Most Wanted: CryptoLocker—The Ransomware Trojan
How to Avoid the Spying of EEUU & other Practical Solutions Computing: Protec...

How to Avoid the Spying of EEUU & other Practical Solutions Computing: Protec...
Destacado
Destacado (20)
This is Next-Gen IT Security - Introducing Intercept X

This is Next-Gen IT Security - Introducing Intercept X
AWS Summit 2011: Designing Fault Tolerant Applicatons

AWS Summit 2011: Designing Fault Tolerant Applicatons
Alphorm.com Support Formation Sophos UTM les fonctionnalités avancées

Alphorm.com Support Formation Sophos UTM les fonctionnalités avancées
Similar a Ransomware
Similar a Ransomware (20)
Panda Adaptive Defense 360 - Cyber Extortion Guide

Panda Adaptive Defense 360 - Cyber Extortion Guide
Tutorial 09 - Security on the Internet and the Web

Tutorial 09 - Security on the Internet and the Web
End User Security Awareness - Information Security

End User Security Awareness - Information Security
When Ransomware Attacks: Emergency Measures to Save Your Business

When Ransomware Attacks: Emergency Measures to Save Your Business
Discussion Question Contrast file encryption and volume encryptio.docx

Discussion Question Contrast file encryption and volume encryptio.docx
'We Eat Cryptolocker for Breakfast' - How to Beat Ransomware Presentation

'We Eat Cryptolocker for Breakfast' - How to Beat Ransomware Presentation
Null mumbai Session on ransomware by_Aditya Jamkhande

Null mumbai Session on ransomware by_Aditya Jamkhande
Más de Deepak Kumar (D3)
Más de Deepak Kumar (D3) (20)
Último
Último (20)
HMCS Max Bernays Pre-Deployment Brief (May 2024).pptx

HMCS Max Bernays Pre-Deployment Brief (May 2024).pptx
This PowerPoint helps students to consider the concept of infinity.

This PowerPoint helps students to consider the concept of infinity.
Exploring_the_Narrative_Style_of_Amitav_Ghoshs_Gun_Island.pptx

Exploring_the_Narrative_Style_of_Amitav_Ghoshs_Gun_Island.pptx
Sensory_Experience_and_Emotional_Resonance_in_Gabriel_Okaras_The_Piano_and_Th...

Sensory_Experience_and_Emotional_Resonance_in_Gabriel_Okaras_The_Piano_and_Th...
Jual Obat Aborsi Hongkong ( Asli No.1 ) 085657271886 Obat Penggugur Kandungan...

Jual Obat Aborsi Hongkong ( Asli No.1 ) 085657271886 Obat Penggugur Kandungan...
General Principles of Intellectual Property: Concepts of Intellectual Proper...

General Principles of Intellectual Property: Concepts of Intellectual Proper...
Interdisciplinary_Insights_Data_Collection_Methods.pptx

Interdisciplinary_Insights_Data_Collection_Methods.pptx
Unit 3 Emotional Intelligence and Spiritual Intelligence.pdf

Unit 3 Emotional Intelligence and Spiritual Intelligence.pdf
Micro-Scholarship, What it is, How can it help me.pdf

Micro-Scholarship, What it is, How can it help me.pdf
Ransomware
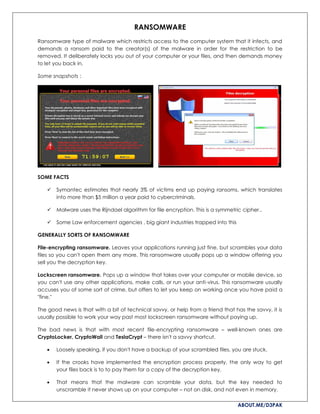
- 1. ABOUT.ME/D3PAK RANSOMWARE Ransomware type of malware which restricts access to the computer system that it infects, and demands a ransom paid to the creator(s) of the malware in order for the restriction to be removed. It deliberately locks you out of your computer or your files, and then demands money to let you back in. Some snapshots : SOME FACTS Symantec estimates that nearly 3% of victims end up paying ransoms, which translates into more than $5 million a year paid to cybercriminals. Malware uses the Rijndael algorithm for file encryption. This is a symmetric cipher.. Some Law enforcement agencies , big giant industries trapped into this GENERALLY SORTS OF RANSOMWARE File-encrypting ransomware. Leaves your applications running just fine, but scrambles your data files so you can't open them any more. This ransomware usually pops up a window offering you sell you the decryption key. Lockscreen ransomware. Pops up a window that takes over your computer or mobile device, so you can't use any other applications, make calls, or run your anti-virus. This ransomware usually accuses you of some sort of crime, but offers to let you keep on working once you have paid a "fine." The good news is that with a bit of technical savvy, or help from a friend that has the savvy, it is usually possible to work your way past most lockscreen ransomware without paying up. The bad news is that with most recent file-encrypting ransomware – well-known ones are CryptoLocker, CryptoWall and TeslaCrypt – there isn't a savvy shortcut. Loosely speaking, if you don't have a backup of your scrambled files, you are stuck. If the crooks have implemented the encryption process properly, the only way to get your files back is to to pay them for a copy of the decryption key. That means that the malware can scramble your data, but the key needed to unscramble it never shows up on your computer – not on disk, and not even in memory.
- 2. ABOUT.ME/D3PAK CONCEPT : The C&C issues a public key for the infected host and are stored with other information in values under the registry key HKEY_CURRENT_USERSoftwareCryptoLocker_0388. The public key then seeks a wide range of file extensions on the victim’s machine and further starts the encryption process. The private key that is used to decryption of the infected files is not saved on the computer, but on a C&C server. SOME ARTIFACTS : Spawns either ctfmon.exe or svchost.exe (randomly chosen) where its child process injects its injected own code & sample from %TEMP% folder. C: Documents and Settings <User> Application Data <random name>.exe C: Users <User> AppData Local <random name>.exe KEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun “CryptoLocker” HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunOnce “*CryptoLocker” HKEY_CURRENT_USERSoftwareCryptoLocker rack-core.bin .... parse and analyse the files so on WHAT TO DO? So the big question, usually left unanswered in technical discussions of ransomware, is, "Should you pay?" At a typical price point around $300 to $600 (£200 to £400), ransomware can be expensive. For better or for worse, most ransomware gangs have acquired a bit of an "honour among thieves" reputation, so that if you do pay over the money, you almost certainly will get your files back. On the other hand, law enforcement and security experts are very likely to say, "These are crooks! This is extortion! If you can possibly take it on the chin, we urge you NOT TO PAY!" But those are easy words to say if it's not your data on the line. Interestingly, one reason for not paying extortionists is that there is often no way to ensure that they won't come back to gouge you for a second payment, or a third, and so on. But, as described above, modern file-scrambling ransomware doesn't actually steal your files. The crooks don't have a copy of anything of yours, just the private key to unlock the scrambled files on your own computer.
- 3. ABOUT.ME/D3PAK In theory, then, once you've paid up, decrypted your files and disinfected the malware, you and the crooks are back on an even footing, and they can't come back for more. SOME THIRD PARTY UTILITIES, CONCEPT YOU CAN TWEAK : 1: Restart your system with safe mode 2 :At least update AV, Antimwalware etc and scan 3 :You can install : Malwarebytes Anti-Malware RogueKiller Adwcleaner or Rootkit Remover 4: Scan and delete Ransomeware or maljunks variants For ex : C:Users<YOUR USERNAME>AppDataRoamingRandomFileName.exe C:WINDOWSsystem32msctfime.ime Delete TEMP/Prefetch folders data 5 : Restore from system volume information(if enabled) SHOULD YOU PAY? We're not going to moralise about whether it's always unacceptable to support criminality by paying up, even if you are in a difficult position. We'll leave you with plainer advice, namely, "It's OK to pay, but it's much better not to." So, keep these two points in mind: Don't pay if you can possibly avoid it, even if it means some personal hassle. Take precautions today (e.g. backup, proactive anti-virus, web and email filtering) so that you avoid getting into a position where you ever need to pay. Remember: if you don't have backups and you lose your laptop, you're in the same trouble – worse, actually – than you would be with ransomware. After all, there's no-one you can pay any amount of money to in order to get your data back if your hard disk. In future if you dont want to trap from these kind of nasty stuff , then you need to strengthen your system security. Do not open suspicious e-mails or uninvited attachment Update the version and patches of your qualified antivirus program Firewalls (NIDS, IDPS), Use addons related to prevent from Drive by downloads , droppers or any automated scripts etc. Group Policy Object of the computer to restrict the registry key (syskey). In Local security policy under Software Restriction Polices define Additional Rules. Regarding research or reverse eng use isolated architecture environment. Attachment filters But beware Hackers /Crackers are much smarter. Lots of things are there so as primary Prevention is better then cure. Src: Reddit , comodo , naked security, F5 , adlice,bleeping computer -------------------------------------------------------------------------------------------------------------------------------------------- BE SMART & CREATIVE IN CYBER WORLD D3pak Kumar IT Security & Cyber-Forensic http://in.linkedin.com/in/d3pak/ C|EH , CHFi , ECSA , CCS , CCF , MCA , OPSEC , CSICS , GFSU
