Are Mobile Apps the Enemy?
•
0 recomendaciones•984 vistas
Over 5 billion app downloads are vulnerable to remote attacks. See how FireEye analyzes the numbers, and learn what you can do to identify and manage harmful mobile apps. Visit www.fireeye.com for more information.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
Destacado
Destacado (12)
Live Webcast: Reaching Today's Prospective Students

Live Webcast: Reaching Today's Prospective Students
Más de FireEye, Inc.
Más de FireEye, Inc. (20)
Asia Pacific & The Security Gap: Don't Stand Still

Asia Pacific & The Security Gap: Don't Stand Still
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...
[Infographic] Healthcare Cyber Security: Threat Prognosis![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Healthcare Cyber Security: Threat Prognosis
[Infographic] Email: The First Security Gap Targeted by Attackers![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Email: The First Security Gap Targeted by Attackers
5 Reasons Cyber Attackers Target Small and Medium Businesses 

5 Reasons Cyber Attackers Target Small and Medium Businesses
SANS 2013 Report: Digital Forensics and Incident Response Survey 

SANS 2013 Report: Digital Forensics and Incident Response Survey
SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...

SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...
Último
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Último (20)
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
Are Mobile Apps the Enemy?
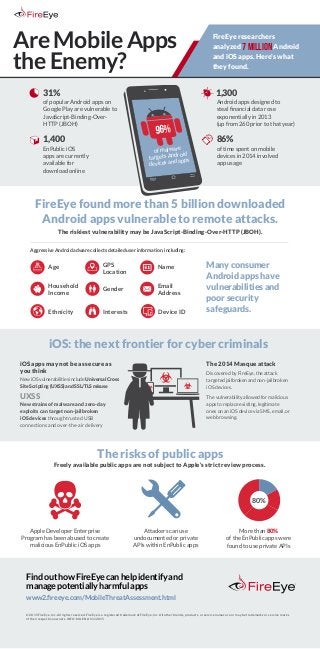
- 1. iOS: the next frontier for cyber criminals iOS apps may not be as secure as you think The risks of public apps Apple Developer Enterprise Program has been abused to create malicious EnPublic iOS apps More than 80%Attackers can use undocumented or private APIs within EnPublic apps Android apps designed to steal financial data rose exponentially in 2013 (up from 260 prior to that year) The 2014 Masque attack Discovered by FireEye, the attack targeted jailbroken and non-jailbroken iOS devices. The vulnerability allowed for malicious apps to replace existing, legitimate ones on an iOS device via SMS, email, or web browsing. New iOS vulnerabilities include Universal Cross Site Scripting (UXSS) and SSL/TLS misuse of the EnPublic apps were found to use private APIs New strains of malware and zero-day exploits can target non-jailbroken iOS devices through trusted USB connections and over-the-air delivery 1,300 Freely available public apps are not subject to Apple's strict review process. of time spent on mobile devices in 2014 involved app usage 86% EnPublic iOS apps are currently available for download online 1,400 of popular Android apps on Google Play are vulnerable to JavaScript-Binding-Over- HTTP (JBOH) 31% 80% UXSS AreMobileApps theEnemy? FireEye researchers analyzed 7 million Android and iOS apps. Here's what they found. Many consumer Android apps have vulnerabilities and poor security safeguards. FireEye found more than 5 billion downloaded Android apps vulnerable to remote attacks. The riskiest vulnerability may be JavaScript-Binding-Over-HTTP (JBOH). Aggressive Android adware collects detailed user information, including: Age Household Income Ethnicity Gender Interests GPS Location Name Email Address Device ID of malware targets Android devices and apps 96% FindouthowFireEyecanhelpidentifyand managepotentiallyharmfulapps www2.fireeye.com/MobileThreatAssessment.html © 2015 FireEye, Inc. All rights reserved. FireEye is a registered trademark of FireEye, Inc. All other brands, products, or service names are or may be trademarks or service marks of their respective owners. INFO.MA.EN.US112015
