[Infographic] Threat Landscape: Law Firms
•
0 recomendaciones•1,228 vistas
Law firms, with all their confidential and client information, are prime targets of cyber crime. Learn how FireEye can help lead law firms through 7 steps to a stronger cyber security posture. Visit www.fireeye.com for more information.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
Más de FireEye, Inc.
Más de FireEye, Inc. (20)
Asia Pacific & The Security Gap: Don't Stand Still

Asia Pacific & The Security Gap: Don't Stand Still
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Industry Intelligence Brief] Cyber Threats to the Legal and Professional Ser...
[Infographic] Healthcare Cyber Security: Threat Prognosis![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Healthcare Cyber Security: Threat Prognosis](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Healthcare Cyber Security: Threat Prognosis
[Infographic] Email: The First Security Gap Targeted by Attackers![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Email: The First Security Gap Targeted by Attackers
5 Reasons Cyber Attackers Target Small and Medium Businesses 

5 Reasons Cyber Attackers Target Small and Medium Businesses
SANS 2013 Report: Digital Forensics and Incident Response Survey 

SANS 2013 Report: Digital Forensics and Incident Response Survey
SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...

SANS 2013 Report on Critical Security Controls Survey: Moving From Awareness ...
Último
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Último (20)
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...

Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
[Infographic] Threat Landscape: Law Firms
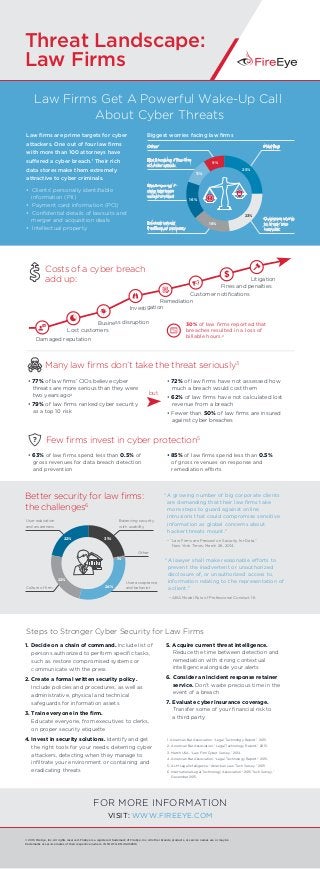
- 1. Threat Landscape: Law Firms Balancing security with usability User acceptance and behavior User education and awareness Culture of firm Law Firms Get A Powerful Wake-Up Call About Cyber Threats Law firms are prime targets for cyber attackers. One out of four law firms with more than 100 attorneys have suffered a cyber breach.1 Their rich data stores make them extremely attractive to cyber criminals. • Clients’ personally identifiable information (PII) • Payment card information (PCI) • Confidential details of lawsuits and merger and acquisition deals • Intellectual property Other A growing number of big corporate clients are demanding that their law firms take more steps to guard against online intrusions that could compromise sensitive information as global concerns about hacker threats mount.” – “Law Firms are Pressed on Security for Data,” New York Times, March 26, 2014. – ABA Model Rule of Professional Conduct 1.6 A lawyer shall make reasonable efforts to prevent the inadvertent or unauthorized disclosure of, or unauthorized access to, information relating to the representation of a client.” “ “ 22% 22% 24% 1% 31% • 63% of law firms spend less than 0.5% of gross revenues for data breach detection and prevention • 85% of law firms spend less than 0.5% of gross revenues on response and remediation efforts 30% of law firms reported that breaches resulted in a loss of billable hours.2 Better security for law firms: the challenges6 but Biggest worries facing law firms Steps to Stronger Cyber Security for Law Firms 1. American Bar Association. “Legal Technology Report.” 2015. 2. American Bar Association. “Legal Technology Report.” 2015. 3. Marsh USA. “Law Firm Cyber Survey.” 2014. 4. American Bar Association. “Legal Technology Report.” 2015. 5. ALM Legal Intelligence. “American Law Tech Survey.” 2015 6. International Legal Technology Association. “2015 Tech Survey.” December 2015. 1. Decide on a chain of command. Include list of persons authorized to perform specific tasks, such as restore compromised systems or communicate with the press 2. Create a formal written security policy. Include policies and procedures, as well as administrative, physical and technical safeguards for information assets 3. Train everyone in the firm. Educate everyone, from executives to clerks, on proper security etiquette 4. Invest in security solutions. Identify and get the right tools for your needs: deterring cyber attackers, detecting when they manage to infiltrate your environment or containing and eradicating threats 5. Acquire current threat intelligence. Reduce the time between detection and remediation with strong contextual intelligence alongside your alerts 6. Consider an incident response retainer service. Don’t waste precious time in the event of a breach 7. Evaluate cyber insurance coverage. Transfer some of your financial risk to a third party • 77% of law firms’ CIOs believe cyber threats are more serious than they were two years ago4 • 79% of law firms ranked cyber security as a top 10 risk • 72% of law firms have not assessed how much a breach would cost them • 62% of law firms have not calculated lost revenue from a breach • Fewer than 50% of law firms are insured against cyber breaches Many law firms don’t take the threat seriously3 Few firms invest in cyber protection5? Costs of a cyber breach add up: FOR MORE INFORMATION VISIT: WWW.FIREEYE.COM © 2016 FireEye, Inc. All rights reserved. FireEye is a registered trademark of FireEye, Inc. All other brands, products, or service names are or may be trademarks or service marks of their respective owners. INFO.OTA.EN.US.052516 Damaged reputation Lost customers Business disruption Investigation Remediation Customer notifications Fines and penalties Litigation $ Other Outsiders trying to break into network Not knowing if data has been compromised Not knowing if the firm is under attack 9% 25% 23% 16% 16% 11%
