Advanced IT and Cyber Security for Your Business
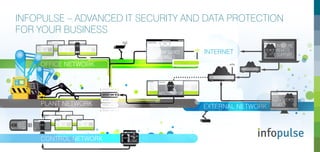
- 1. OK PLANT NETWORK CONTROL NETWORK EXTERNAL NETWORK OFFICE NETWORK LOGIC PLC INSECURE REMOTE SUPPORT MODEMS 3-RD PARTY ISSUES OK OK OK OK OK OK OK OK OK MISCONFIGURED FIREWALLS USB KEYS INTERNET OK OKOKINFECTED LAPTOP WIRELESS OK INFOPULSE – ADVANCED IT SECURITY AND DATA PROTECTION FOR YOUR BUSINESS
- 2. RISK MANAGEMENT CONT INUITY BUS INESS D ATA PROT ECTION SE CURITY COMP LIANCE COMPETITIVE ADVANTAGE FINANCE PROTECTION REPUTATION PROTECTION WHO WE ARE Delivering world-class services in Software Engineering, IT Operations and Information Security, Infopulse has built a 20 years reputation as a trusted full-service solution provider, working globally with local presence across Europe. Our mission is to provide clients with an all-in-one package: quality services, well-educated and talented people, proper technologies, and comprehensive expertise – tailored around the customer – to deliver benefits, perform exceptionally, solve problems, and fill the needs. Infopulse provides security services that are designed to deliver financial, technical and strategic benefits. Our service portfolio can meet any organization’s compliance, security and assessment requirements, and helps to identify, evaluate, and improve the enterprise security system. BUSINESS VALUE
- 3. PAS 99 ISO 9001 ISO/IEC27001 ISO 14001 ISAE 3402 OUR STRENGTHS • Complete understanding of today’s security challenges • Experience in all technical related business requirements of most key domains • Full-cycle process support (assessment design development implementation support) • Implementing complex solution, modular applicable and flexible balanced • Strong project management • 20+ years of experience CERTIFICATIONS Company: • Security Management ISO 27001 • Quality Management ISO 9001 • Environmental Management ISO 14001 • Integrated Management System PAS 99 • Assurance Engagements ISAE 3402 • PCI: Qualified Security Assessor (QSA)* & Approved Scanning Vendor (ASV)* Specialists: • Certified Information Systems Security Professional (CISSP) • Certified Information Systems Auditor (CISA) • Certified Ethical Hacker (CEH) • And more * Provided by Infopulse Partner BMS Consulting LLC
- 4. ASSESS M ENT AN ALYSIS SOLU TION IMPLEMEN TATION OUR APPROACH We take our customers' IT landscape to the desired state of the security robustness with our understanding of cyber security through the whole organization, from strategy, to tactical decisions and operational management. Assessment • Review business goals, requirements and constraints • Execute audit and collect findings on processes, IT infrastructure or security controls
- 5. Analysis • Classify the findings • Identify dependencies Map to the needs Define gaps • Balance costs and measures Implementation • Consulting: assistance with guidelines, process design, knowledge transfer and project review • Security Project Management • Full Scope Implementation Solution Strategic Packaged Single Service Strategic Solutions • Optimization of business processes • Improvement of IT infrastructure • Improvement of Security System Package Solutions • Infrastructure, Cloud Security • Application security • Endpoint security • Industrial IT security • Compliance audits and management • Business continuity management • Risk management • Identity&Accessmanagement
- 6. INFRASTRUCTURE AND CLOUD SECURITY Service Components • Infrastructure planning and design • Virtualization • Network security (AntiDOS, IPS, IDS, Proxy, SSL, Wireless) • Vulnerability and Patch Management • Backup management • Antivirus, Anti-SPAM • Logging and Monitoring (SIEM) • Mobile security Service Outcome • High-level policies, strategies, architectures • Cost-efficient infrastructure • Implemented secure and fault-tolerant systems • Recommendations for vulnerability mitigation • Implemented security services • Improved system manageability Business Value • Reducing operating and capital expenditures • Reducing storage costs • Protecting business from disruption • Protecting corporate secrets • Reputation
- 7. APPLICATION SECURITY Service Components • Governance • Risk assessment • Process integration (architecture, development lifecycle) • Analysis of business requirements • Code review (automated, manual) • Penetration testing • SAP security Service Outcome • High-level policies, strategies, architectures • Customized risks treatment plans • Security requirements for specific technology • Application vulnerabilities identified and remediated prior to deployment • Recommendations for application hardening and vulnerability mitigation Business Value • Reducing costs of application security – decrease incidents • Ensuring application quality to support reputation and competitive advantage • Ensuring business continuity and application sustainability
- 8. ENDPOINT SECURITY Service Components • Governance • Application Control • License Management • Internet access security (IPS, user activity control, Web filtering) • Device management • Data Leakage Prevention • Antivirus (antimalware) • Security Awareness Service Outcome • High-level policies, strategies, architectures • Recommendations for vulnerability mitigation • Implemented security systems • Security Awareness Program • Compliance reports • User activity reports Business Value • Reducing operational costs • Reducing storage costs • Protecting business from disruption • Protecting corporate secrets • Prevention of penalties • Reputation
- 9. OK INDUSTRIAL IT SECURITY Service Components • Current infrastructure audit • Industry 4.0 upgrade infrastructure audit • Security refactoring with Quality Assurance • Consulting • Physical security audit • Physical access control • Video surveillance • Physical intrusion detection systems • SCADA security Service Outcome • Detection of actual vulnerabilities • Prediction of potential vulnerabilities during the upgrade • Seamless refactoring with no impact to production • Increased personnel awareness resulting also in proper demands for suppliers • Physical security Business Value • Ensuring business continuity • Safety • Prevention of penalties • Facilitated Industry 4.0 upgrade as a competitive advantage • Profit, reputation, know-how
- 10. SCADA, NEXT-GENERATION CYBER SECURITY SOLUTIONS Main issues of modern industrial information systems are their close integration into the corporate network, the need of interconnection to other entities and the lack of attention of the security professionals. The value of information security grows tremendously since in 2011 “Industry 4.0” was introduced at the Hanover Fair. New technologies, that combine Internet of things (IoT), Big Data, Virtual Factory and distributed industry information processing are bringing new types of security threats. We understand the risks that IT managers of SCADA face today: hackers, data leaks, attacks, unauthorized access systems, and usage of monitoring and forensic tools. We perform complex security reviews and provide special security services for SCADA networks: • Network Security Assessment • SCADA White Box Penetration Testing • Vulnerability Identification and Risk Analysis • Secure Architecture of Network Interconnection • Implementing Network Access Control • Security events monitoring and attack mitigation • Security Operation Command Center implementation
- 11. 1 2 3 4 8 7 6 5 Understand risks Harden Components Document Policy and Procedures Control Access Design secure architecture Segment the Network Assess Existing System Continuously Monitor SCADA Security Operation Command Center
- 12. SAP SECURITY We fully understand the nature of enterprise application plat- form security and cover all technical layers to ensure the safety of your business. Our complex approach with a full set of SAP security services to establish your SAP ecosystem security will guarantee the pro- tection of your enterprise data and its integrity. Service details: • Concentrating on weaknesses inside systems, configuration and processes • Implementing SAP approved security tools and approaches as well as common controls • Controlling all security domains according to ISO 27001/27002 Tools: • SAP Governance-Risk-Compliance • Onapsis X1 Auditing Tool • Onapsis Security Platform • HP Fortify Results: • Revision of Corporate Security Policies • Detailed recommendations on securing your SAP installation • Report on SAP infrastructure security assessment • Action plan for applying security controls and its Implementation • Continuous monitoring, risk assessment and incident forensics
- 14. Mobile Application Management Mobile Content Management Entrerprise Mobility Management Mobile Device Management MOBILE SECURITY Infopulse Mobile Security is the complete mo- bile security service that manages and protects all your mobile devices, privacy, and its mobile applications. Enterprise Mobility Management (EMM) solu- tions control mobile devices across multiple operating systems, provide secure access to corporate resources, allow automatic device configuration, and support selective wipe of enterprise data for both corporate and user- owned devices (BYOD). Service details: • Establish mobile device security policies and compliance rules • Securely provision mobile devices to users • Allow users to authenticate on their devices • Configure business apps and ensure they run only on authorized devices • Provide secure tunneling to the enterprise. • Distribute and delete business apps and data without compromising end-user privacy and personal information • Ensure corporate information cannot leave secured mobile devices • Establish data loss prevention (DLP) controls to maintain compliance
- 15. TWO–FACTOR STRONG AUTHENTICATION Two-factor authentication is used to increase security by requiring two different things: • “something you know” (password or PIN) • “something you have” (mobile phone or token) Implementing two-factor token or smart card based authentication will make the whole IT environment more secure and will enable new possibilities: • Boot and OS authentication • Secure email exchange • Data encryption and protection • Secure access to web and corporate apps • Digital signature for documents and apps. Service details: • Planning the architecture of a two-factor authentication system • Selection and implementation of the solution • Developing instructions for administrators and users • Training of employees
- 16. ADVANCED PERSISTENT THREAT STRESS-TESTING The way to understand what it means to be hacked: APT stress-test emulates APT activities phase-to-phase in a fully controlled manner and allows testing company’s security controls and team’s readiness. APT stress test is a type of next generation penetration test, that can show up all vulnerabilities in an IT sys- tem, software, processes and staff and helps to develop right mitigation plan and stay ready for real emergency. Service details: • Allows revealing real organization weaknesses and evaluating the risks • Involving people (social engineering) and processes • Reporting includes test objectives, scope, methods used and its results including proof (video, logs) Tools: • Rapid7 NeXpose Enterprise • Tenable Nessus • Acunetix Web Security Scanner • Burp Suite Pro • Rapid7 Metasploit Framework • Kali Linux • Social Engineering Toolkit
- 17. PR EPARATION REPORT DESIG N HY BRID TESTING DYNAMIC T ESTING STATIC TESTING PRESENTATION OF RESULTS 1 2 3 4 APPLICATION BACKDOOR ASSESSMENT Application backdoor assessment is a special type of source code audit that aims at insuring full code safety. This assessment bases on static analysis of source code with dynamic confirmation of vulnerable or dangerous parts of code. All major software development languages, classical for desktop applications, modern for mobile development as well as ERP scripting and legacy languages are supported. Service details: • Identifying and approving vulnerabilities and backdoors • Providing high-priority action plan to address critical problems • Recommendations to solute identified problems Tools: • OWASP Code Review Guide v1.1 • OWASP Testing Guide v3 • IBM Security AppScan Source • HP Fortify
- 18. SECURITY MONITORING Organizations of all sizes are facing an ever-growing landscape of security threats that are becoming more targeted and malicious in its nature. Attacks are no longer being launched in masse with the hope of snaring random victims, rather they are focused and sophisticated, de- signed to defeat tactical, reactive security tech- nologies that are in place at an organization. Whether an attack targets a network, an end- point device, an application, or a database, it is important for any organization to have visibility into how their systems are being used and by whom. Granular visibility of network activity is essential to protect against a catastrophic event such as a security breach, system outage, high- risk event, or compliance violation that results from an unintentional or unauthorized changes to these systems. Unfortunately most organizations don’t have the tools, time, or staff expertise to deal with the challenge of keeping up with the evolving threat landscape and increased sophistication of at- tack techniques.
- 19. Benefits: • Improved Risk Management (monitoring, detection and response) • Cost effective (usage of popular open source security tools) • Access to a team of certified specialists • Flexible and scalable to suit any size business • “Pay as you grow” license model Service details: • Asset Discovery • Active and Passive Network Scanning • Asset Inventory • Vulnerability Assessment • Continuous Vulnerability Monitoring • Authenticated / Unauthenticated Active Scanning • Threat Detection • Network and Wireless IDS • Host IDS • File Integrity Monitoring • Advanced Persistent Threat Detection • Behavioral Monitoring • Log Collection • Netflow Analysis • Server and Service Availability Monitoring • Security Intelligence / SIEM • SIEM Event Correlation, Log management • Incident Response
- 20. PCI DSS PCI DSS is an international standard on se- curing payment cardholders’ data, established and controlled by VISA, MasterCard, JCB, Dis- cover and AmEx. This standard consists out of 12 high-level requirements, which drills-down to more than 200 control procedures. All organizations that process, retain or transmit customer information including credit card data have an obligation to meet PCI-DSS (Payment Card Industry Data Security Stan- dards) requirements. BMS consulting, our Infopulse security partner, is Qualified Security Assessor and Approved Scanning Vendor and is providing the following services including certification: • Report on preliminary audit • Remediation implementation plan • PCI DSS Security Policies and Procedures pack • Reports on mandatory activities (ASV scan, Internal Vulnerability scan, Internal and External Penetration test, Wifi Scan, Web Vulnerabilities Scan) • Report of Compliance • Attestation of Compliance • Certificate of Compliance
- 21. Client background Raiffeisen Bank International Group, is a leading corporate and investment bank with 15 subsidiary banks in Central and Eastern Europe (CEE). Business challenge RBI Group every three years chooses in all serviced countries professional security teams to be short-listed in their global delivery register. Applicant should prove their security certification, show their level of competence and demonstrate their ability to solve complex security tasks in testing environment. The challenge is quite similar to BlackHat’s CTF (Capture the Flag) contest and is organized by RBI’s IT division in Austria. During two-months competition not more than two com- panies from one country. Solution After winning the challenge over the last 5 years we are now continuously placed in the global short-list. We have completed more than 10 penetration tests cycles for the RBI Group subsidiaries. The scope of penetration test included corporate network perimeter, internal banking information systems, mobile banking applications as well as web-banking portals. 14.8 million customers 54,500 employees RAIFFEISEN BANK INTERNATIONAL
- 22. Client background UniCredit Bank – is one of the largest multifunctional banks in Ukraine, offering its clients a full range of actual services in both individuals’ and corporate clients’ segment. The widespread network of UniCredit Bank consists of 435 branches. The bank staff are the best specialists in the country’s market and totals 6,164 employees (as of December 1, 2013). Business challenge UniCreditBank as one of the largest card acqui- ring and issuing banks has received the require- ment of PCI DSS compliance form VISA in 2008. Sience then Unicredit started it’s PCI DSS compliance program and during 2008-2009 has changed several Qualified Security Assessors. Solution Full scope of services to accomplish PCI DSS: • Preliminary audit • Scoping and Sampling • Remediation planning and implementation • Penetration testing • ASV and internal vulnerability scan, WiFi scan • Documentation development and implementation of security controls • Certification audit UNICREDITBANK Success of this project has become possible due to the usage of flexible and proven approaches by auditors and consultants, high competence of the working group, coordinated work, and focus on the results. - V.Korelov, Head of security department
- 23. Client background Piraeus Bank Group headquartered in Athens, Greece, has more than 22,000 employees in 10 countries around the world. Piraeus Bank Group offers a full range of financial products and services to approximately 6mn customers. Total assets of the Group amounted to €89 bn, net loans to €56 bn and customer deposits to €47 bn on March 31, 2015. Business challenge Pireaus Bank Ukraine faced unrevealed corpo- rate data leaks during it’s corporate transformation and growth. The board of directors was concer- ned about lack of control over corporate and client’s data distribution inside the bank's telecom- munication network and through its border. Solution We performed internal data distribution asses- sment, reviewed bank’s business processes and developed a set of policies and procedures on confidential data handling. Based on obtained information we have implemented an automated data leak prevention solution based on Syman- tec DLP. The solution includes data flow moni- toring on desktops, in the web-traffic and email messages. PIRAEUS BANK Symantec DLP implementa- tion project in our bank went quite smoothly. All the works were carried out as planned, and the system has fully met its objectives, which we included in the project documentation. Highly professional team of implemen- tation eengineers and informa- tion security consultants made possible to achieve full control over distribution of confidential information in the bank - S. Fedorov, CIO
- 24. infopulse.com CONTACT US Infopulse GmbH Kochstrasse 19, 74405 Gaildorf, Germany +49 7971 919 30 51 info@infopulse.de Infopulse LLC 24, Polyova Str., 03056 Kyiv, Ukraine +38 044 457-88-56 info@infopulse.com * p o w e r e d b y FOLLOW US facebook.com/InfopulseGlobal twitter.com/InfopulseGlobal linkedin.com/company/infopulse google.com/+Infopulse slideshare.net/Infopulse
