E metrics san fran 2014 aurelie pols final
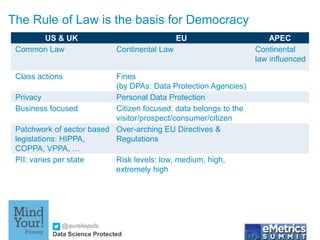
- 1. @aureliepols Data Science Protected The Rule of Law is the basis for Democracy US & UK EU APEC Common Law Continental Law Continental law influenced Class actions Fines (by DPAs: Data Protection Agencies) Privacy Personal Data Protection Business focused Citizen focused: data belongs to the visitor/prospect/consumer/citizen Patchwork of sector based legislations: HIPPA, COPPA, VPPA, … Over-arching EU Directives & Regulations PII: varies per state Risk levels: low, medium, high, extremely high
- 2. @aureliepols Data Science Protected PII list of variables & US states 2 Medical information as PII California Arkansas Missouri New Hampshire North Dakota Texas Virginia Financial information as PII Alaska North Carolina Iowa North Dakota Kansas Oregon Massachusetts South Carolina Missouri Vermont Nevada Wisconsin New York* Wyoming Passwords as PII Georgia Maine Nebraska Biometric information as PII Iowa Nebraska North Carolina Wisconsin Source: information based on current ongoing analysis (partial
- 3. @aureliepols Data Science Protected PII vs. Risk levels, US vs. EU Low Medium (profiling) High (sensitive) Risk level Data type Information Security Measures Extremely high (profiling of sensitive data) PII
- 4. @aureliepols Data Science Protected Total Privacy fines, penalties & settlements worldwide Just 6 weeks into 2014, the world total in Privacy damages has already reached half the level of last year’s record: $74 million Source: http://www.computerworld.com/s/article/9246393/Jay_Cli ne_U.S._takes_the_gold_in_doling_out_privacy_fines?ta
- 5. @aureliepols Data Science Protected EU Fines? Spain: responsible for 80% of data protection fines in the EU Source: http://i0.kym- cdn.com/photos/images/newsfeed/00 0/242/381/63a.jpg Source: http://www.mindyourprivacy.com/downlo ad/privacy-infographic.pdf
- 6. @aureliepols Data Science Protected Techno security is just 1 piece of the puzzle Data Collection Processes Resources
- 7. @aureliepols Data Science Protected MYP Information Security Framework Organizational Data Security measures CONFIDENTIALITY SECURITY PRIVACY Integrity Availability Authentication DATA LIFECYCLE RISK CLASSIFICATION Low/medium/high/extreme
- 8. @aureliepols Data Science Protected Remember! Human error causes most data breaches Source: http://www.cooldailyinfographic s.com/post/data-and-security- breaches
