Security Threats in IT Infographic
•
0 recomendaciones•473 vistas
NTT's breadth and scope allowed it to analyse three billion IT Security attacks in 2013, the results was combined to produce the Global Threat Intelligence Report. This infographic is an extract from the Global Threat Intelligence Report.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
To meet the demands of tomorrow’s information, St Edmunds needed to ensure its students would have reliable and fast access to technology for years to come. After a competitive tender for solutions and implementation partners St Edmund’s established a partnership with NTT Communications ICT Solutions (NTT ICT).St Edmund's College prepares it's students for the future with NTT Communicat...

St Edmund's College prepares it's students for the future with NTT Communicat...NTT Communications ICT Solutions
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Meeting consumer needs, now and in the future - Digital Futures 2025

Meeting consumer needs, now and in the future - Digital Futures 2025
10 Top Newsworthy Tech Industry Headlines Of 2020 | Other Than COVID

10 Top Newsworthy Tech Industry Headlines Of 2020 | Other Than COVID
CIS 2015 Security Without Borders: Taming the Cloud and Mobile Frontier - And...

CIS 2015 Security Without Borders: Taming the Cloud and Mobile Frontier - And...
Data Con LA 2018 Keynote - The secret to your big data success by Tim Eusterman

Data Con LA 2018 Keynote - The secret to your big data success by Tim Eusterman
Digital Trend Study 2019 - "How to Survive in Digital 2019" - Teaser

Digital Trend Study 2019 - "How to Survive in Digital 2019" - Teaser
Presentación Alessander Firmino - eCommerce Day Bogotá 2015 

Presentación Alessander Firmino - eCommerce Day Bogotá 2015
SEMPL 19: SNEHA NAGESH, Global Search Business Director, PHD Global Business UK

SEMPL 19: SNEHA NAGESH, Global Search Business Director, PHD Global Business UK
Innovation & Business Acquisitions of Smart Security

Innovation & Business Acquisitions of Smart Security
Destacado
To meet the demands of tomorrow’s information, St Edmunds needed to ensure its students would have reliable and fast access to technology for years to come. After a competitive tender for solutions and implementation partners St Edmund’s established a partnership with NTT Communications ICT Solutions (NTT ICT).St Edmund's College prepares it's students for the future with NTT Communicat...

St Edmund's College prepares it's students for the future with NTT Communicat...NTT Communications ICT Solutions
Destacado (15)
St Edmund's College prepares it's students for the future with NTT Communicat...

St Edmund's College prepares it's students for the future with NTT Communicat...
Retro Responsive: From Fixed-Width to Flexible in 55 Minutes

Retro Responsive: From Fixed-Width to Flexible in 55 Minutes
InnoYouth kursus om innovation i AT (Almen Studieforberedelse) på Maribo Gymn...

InnoYouth kursus om innovation i AT (Almen Studieforberedelse) på Maribo Gymn...
Content as strategy: creating value throughout the consumer’s journey

Content as strategy: creating value throughout the consumer’s journey
LSN Lead System Network Presentation 100% Commisions

LSN Lead System Network Presentation 100% Commisions
Create new kinds of multiuser experiences using hydna and Unity

Create new kinds of multiuser experiences using hydna and Unity
Similar a Security Threats in IT Infographic
The 10 Fastest Growing Cyber Security Companies of 2017The 10 Fastest Growing Cyber Security Companies of 2017

The 10 Fastest Growing Cyber Security Companies of 2017Insights success media and technology pvt ltd
Similar a Security Threats in IT Infographic (20)
Deception Technology Market – Overview of advancements in innovation 2025

Deception Technology Market – Overview of advancements in innovation 2025
The 10 Fastest Growing Cyber Security Companies of 2017

The 10 Fastest Growing Cyber Security Companies of 2017
Cost of Cybercrime Study in Financial Services: 2019 Report

Cost of Cybercrime Study in Financial Services: 2019 Report
Pat Pather- Cyber Security Unchartered: Vigilance, Innovation and Adaptability

Pat Pather- Cyber Security Unchartered: Vigilance, Innovation and Adaptability
Security transformation: Helping you manage digital risk

Security transformation: Helping you manage digital risk
Foro Empresarial Perú 2017 - Tendencias impactando Ciudades & Negocios

Foro Empresarial Perú 2017 - Tendencias impactando Ciudades & Negocios
What Are Cyber Attacks All About? | Cyberroot Risk Advisory

What Are Cyber Attacks All About? | Cyberroot Risk Advisory
As telcos go digital, cybersecurity risks intensify by pwc

As telcos go digital, cybersecurity risks intensify by pwc
Coronavirus Impact Assessment And Mitigation Strategies In ICT Industry Compl...

Coronavirus Impact Assessment And Mitigation Strategies In ICT Industry Compl...
Ninth Annual Cost of Cybercrime Study in Financial Services – 2019 Report

Ninth Annual Cost of Cybercrime Study in Financial Services – 2019 Report
Future Watch: Cybersecurity market in South Africa 

Future Watch: Cybersecurity market in South Africa
Último
Último (20)
20240507 QFM013 Machine Intelligence Reading List April 2024.pdf

20240507 QFM013 Machine Intelligence Reading List April 2024.pdf
Local Call Girls in Seoni 9332606886 HOT & SEXY Models beautiful and charmin...

Local Call Girls in Seoni 9332606886 HOT & SEXY Models beautiful and charmin...
best call girls in Hyderabad Finest Escorts Service 📞 9352988975 📞 Available ...

best call girls in Hyderabad Finest Escorts Service 📞 9352988975 📞 Available ...
Call girls Service in Ajman 0505086370 Ajman call girls

Call girls Service in Ajman 0505086370 Ajman call girls
Story Board.pptxrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrr

Story Board.pptxrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrrr
Top profile Call Girls In Dindigul [ 7014168258 ] Call Me For Genuine Models ...![Top profile Call Girls In Dindigul [ 7014168258 ] Call Me For Genuine Models ...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Top profile Call Girls In Dindigul [ 7014168258 ] Call Me For Genuine Models ...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Top profile Call Girls In Dindigul [ 7014168258 ] Call Me For Genuine Models ...
20240510 QFM016 Irresponsible AI Reading List April 2024.pdf

20240510 QFM016 Irresponsible AI Reading List April 2024.pdf
APNIC Policy Roundup, presented by Sunny Chendi at the 5th ICANN APAC-TWNIC E...

APNIC Policy Roundup, presented by Sunny Chendi at the 5th ICANN APAC-TWNIC E...
Ballia Escorts Service Girl ^ 9332606886, WhatsApp Anytime Ballia

Ballia Escorts Service Girl ^ 9332606886, WhatsApp Anytime Ballia
Tadepalligudem Escorts Service Girl ^ 9332606886, WhatsApp Anytime Tadepallig...

Tadepalligudem Escorts Service Girl ^ 9332606886, WhatsApp Anytime Tadepallig...
Mira Road Housewife Call Girls 07506202331, Nalasopara Call Girls

Mira Road Housewife Call Girls 07506202331, Nalasopara Call Girls
20240508 QFM014 Elixir Reading List April 2024.pdf

20240508 QFM014 Elixir Reading List April 2024.pdf
Russian Escort Abu Dhabi 0503464457 Abu DHabi Escorts

Russian Escort Abu Dhabi 0503464457 Abu DHabi Escorts
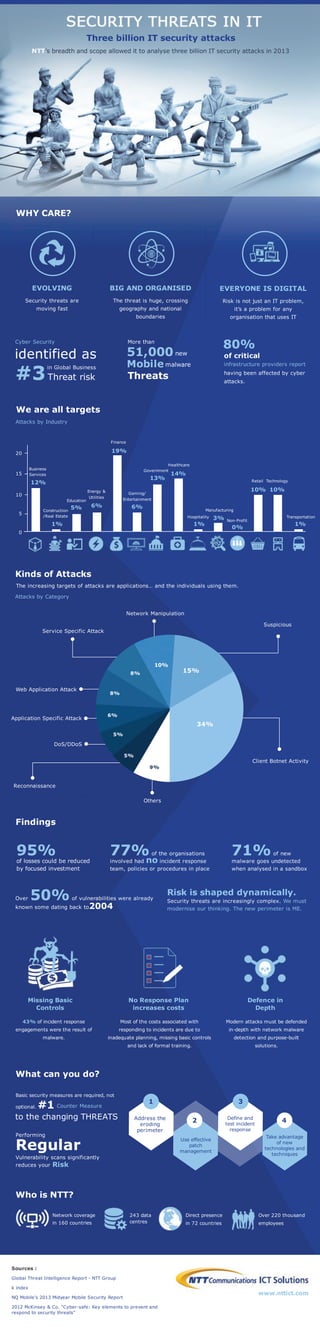
Security Threats in IT Infographic
- 1. ThreebillionITsecurityattacks WHYCARE? EVOLVING Securitythreatsare movingfast BIG AND ORGANISED Thethreatishuge,crossing geographyandnational boundaries EVERYONEISDIGITAL RiskisnotjustanITproblem, it’saproblem forany organisationthatusesIT NTT’sbreadthandscopeallowedittoanalysethreebillionITsecurityattacksin2013 CyberSecurity inGlobalBusiness Threatrisk identifiedas #3 Morethan Threats new malware 51,000 Mobile ofcritical havingbeenaffectedbycyber attacks. infrastructureprovidersreport 80% 95% oflossescouldbereduced byfocusedinvestment Wearealltargets AttacksbyIndustry 20 15 10 5 0 Education Energy& Utilities Finance Gaming/ Entertainment Government Healthcare Hospitality Manufacturing Non-Profit RetailTechnology Transportation Business Services Construction /RealEstate 12% 1% 1% 1% 0% 5% 6% 19% 6% 13% 14% 3% 10% 10% KindsofAttacks Theincreasingtargetsofattacksareapplications… andtheindividualsusingthem. AttacksbyCategory 34% 15% 10% 8% 8% 6% 5% 5% 9% ClientBotnetActivity Suspicious NetworkManipulation ServiceSpecificAttack WebApplicationAttack ApplicationSpecificAttack DoS/DDoS Reconnaissance Others Findings Basicsecuritymeasuresarerequired,not optional.#1CounterMeasure tothechangingTHREATS 77% oftheorganisations involvedhadnoincidentresponse team,policiesorproceduresinplace 71% ofnew malwaregoesundetected whenanalysedinasandbox Performing Regular Vulnerabilityscanssignificantly reducesyourRisk Over50% ofvulnerabilitieswerealready knownsomedatingbackto2004 Riskisshapeddynamically. Securitythreatsareincreasinglycomplex.Wemust moderniseourthinking.Thenew perimeterisME. MissingBasic Controls 43% ofincidentresponse engagementsweretheresultof malware. NoResponsePlan increasescosts Mostofthecostsassociatedwith respondingtoincidentsaredueto inadequateplanning,missingbasiccontrols andlackofformaltraining. x x x x x x x x Modernattacksmustbedefended in-depthwithnetworkmalware detectionandpurpose-built solutions. Defencein Depth Whatcanyoudo? Addressthe eroding perimeter Useeffective patch management 1 3 2 4Defineand testincident response Takeadvantage ofnew technologiesand techniques WhoisNTT? Networkcoverage in160countries Directpresence in72countries 243data centres Over220thousand employees Sources: GlobalThreatIntelligenceReport-NTTGroup kindex NQ Mobile’s2013MidyearMobileSecurityReport 2012McKinsey&Co.“Cyber-safe:Keyelementstopreventand respondtosecuritythreats” www.nttict.com
