DDoS Attack & Defense Infographic
•
0 recomendaciones•514 vistas
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Joseph Salowey, Tableau Software
Transport Layer Security (TLS) 1.3 is almost here. The protocol that protects most of the Internet secure connections is getting the biggest ever revamp, and is losing a round-trip. We will explore differences between TLS 1.3 and previous versions in detail, focusing on the performance and security improvements of the new protocol as well as some of the challenges we face around securely implementing new features such as 0-RTT resumption.
BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...

BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...BlueHat Security Conference
The stealthy Blackshades Remote Access Tool makes it all too easy for malicious actors to infect computer with a powerful and multifeatured trojan. Once infected, attackers can monitor audio and video, look through webcams, capture screens, log keystrokes, and a wide variety of other dangerous features. Learn how you can protect your computer and your sensitive information from this severe cybersecurity threat in this short slide presentation.State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation

State of-the-internet-web-security-threat-advisory-blackshades-rat-presentationState of the Internet
Más contenido relacionado
La actualidad más candente
Joseph Salowey, Tableau Software
Transport Layer Security (TLS) 1.3 is almost here. The protocol that protects most of the Internet secure connections is getting the biggest ever revamp, and is losing a round-trip. We will explore differences between TLS 1.3 and previous versions in detail, focusing on the performance and security improvements of the new protocol as well as some of the challenges we face around securely implementing new features such as 0-RTT resumption.
BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...

BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...BlueHat Security Conference
La actualidad más candente (7)
07182013 Hacking Appliances: Ironic exploits in security products

07182013 Hacking Appliances: Ironic exploits in security products
BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...

BlueHat v17 || TLS 1.3 - Full speed ahead... mind the warnings - the great, t...
Debugging applications with network security tools

Debugging applications with network security tools
Destacado
Destacado (8)
D:\Pc Zombie, Spim, Ransomware, Spam, Phishing Y Scam

D:\Pc Zombie, Spim, Ransomware, Spam, Phishing Y Scam
Pc zombie, spim, ranzomware, spam, phishing y scam

Pc zombie, spim, ranzomware, spam, phishing y scam
An Optimal Risk- Aware Mechanism for Countering Routing Attacks in MANETs

An Optimal Risk- Aware Mechanism for Countering Routing Attacks in MANETs
Más de State of the Internet
The stealthy Blackshades Remote Access Tool makes it all too easy for malicious actors to infect computer with a powerful and multifeatured trojan. Once infected, attackers can monitor audio and video, look through webcams, capture screens, log keystrokes, and a wide variety of other dangerous features. Learn how you can protect your computer and your sensitive information from this severe cybersecurity threat in this short slide presentation.State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation

State of-the-internet-web-security-threat-advisory-blackshades-rat-presentationState of the Internet
Más de State of the Internet (7)
State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation

State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation
Q3 2013 Global DDoS Attacks | DDoS Attack Statistics

Q3 2013 Global DDoS Attacks | DDoS Attack Statistics
Último
Making communications land - Are they received and understood as intended? webinar
Thursday 2 May 2024
A joint webinar created by the APM Enabling Change and APM People Interest Networks, this is the third of our three part series on Making Communications Land.
presented by
Ian Cribbes, Director, IMC&T Ltd
@cribbesheet
The link to the write up page and resources of this webinar:
https://www.apm.org.uk/news/making-communications-land-are-they-received-and-understood-as-intended-webinar/
Content description:
How do we ensure that what we have communicated was received and understood as we intended and how do we course correct if it has not.Making communications land - Are they received and understood as intended? we...

Making communications land - Are they received and understood as intended? we...Association for Project Management
Último (20)
Interdisciplinary_Insights_Data_Collection_Methods.pptx

Interdisciplinary_Insights_Data_Collection_Methods.pptx
Beyond_Borders_Understanding_Anime_and_Manga_Fandom_A_Comprehensive_Audience_...

Beyond_Borders_Understanding_Anime_and_Manga_Fandom_A_Comprehensive_Audience_...
Python Notes for mca i year students osmania university.docx

Python Notes for mca i year students osmania university.docx
Sensory_Experience_and_Emotional_Resonance_in_Gabriel_Okaras_The_Piano_and_Th...

Sensory_Experience_and_Emotional_Resonance_in_Gabriel_Okaras_The_Piano_and_Th...
ICT role in 21st century education and it's challenges.

ICT role in 21st century education and it's challenges.
Jual Obat Aborsi Hongkong ( Asli No.1 ) 085657271886 Obat Penggugur Kandungan...

Jual Obat Aborsi Hongkong ( Asli No.1 ) 085657271886 Obat Penggugur Kandungan...
ICT Role in 21st Century Education & its Challenges.pptx

ICT Role in 21st Century Education & its Challenges.pptx
Kodo Millet PPT made by Ghanshyam bairwa college of Agriculture kumher bhara...

Kodo Millet PPT made by Ghanshyam bairwa college of Agriculture kumher bhara...
Making communications land - Are they received and understood as intended? we...

Making communications land - Are they received and understood as intended? we...
This PowerPoint helps students to consider the concept of infinity.

This PowerPoint helps students to consider the concept of infinity.
DDoS Attack & Defense Infographic
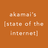
- 1. DDoS Attacks & Defense MOTIVATION Hacktivism • Extortion • Retaliation By Competitors Angry Employees or Customers • Hacker Experiments DDoS ATTACKS IDENTIFY TARGET Web Servers • DNS Servers • Email Servers FTP Servers • Network Devices INVESTIGATE TARGET Footprint Network • Port Scan LAUNCH DDoS ATTACK • Attack too big • Attack too complex Prolexic DDoS Protection 50 Gbps Malicious Traffic 50 Gbps • Monitoring/alerting • 15-minute mitigation SLA • 1.5 Tbps cloud platform • 24/7 SOC Clean Traffic Clean Traffic www.prolexic.com DDoS DEFENSE No Protection, Appliance, CDN, Telco, ISP Use tool to specify: • Target • Port • Attack Types (Layer 3, 4 & 7) • Attack Vectors (DNS, UDP, SYN, etc.) • Duration