Master Thread and Worker Thread with Spin Locks and Realloc
•
0 recomendaciones•189 vistas
This document discusses several topics related to threads, memory allocation, and software vulnerabilities: 1) It mentions master threads, worker threads, and synchronization primitives like spin locks and conditional variables that are used for communication between threads. 2) It discusses issues like user-after-free vulnerabilities that can occur if memory is freed and reallocated without proper synchronization between threads. 3) It provides an example of how reallocating memory could potentially cause problems if the memory address changes or if too many reallocations exhaust available memory. Precautions are needed to avoid security issues or denial of service attacks in multithreaded programs.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Más contenido relacionado
La actualidad más candente
La actualidad más candente (20)
Tips on how to improve the performance of your custom modules for high volume...

Tips on how to improve the performance of your custom modules for high volume...
XPDS14 - osstest, Xen's Automatic Testing Facility - Ian Jackson, Citrix

XPDS14 - osstest, Xen's Automatic Testing Facility - Ian Jackson, Citrix
Manageable data pipelines with airflow (and kubernetes) november 27, 11 45 ...

Manageable data pipelines with airflow (and kubernetes) november 27, 11 45 ...
Similar a Master Thread and Worker Thread with Spin Locks and Realloc
Similar a Master Thread and Worker Thread with Spin Locks and Realloc (20)
Automated reduction of attack surface using call graph enumeration

Automated reduction of attack surface using call graph enumeration
Davide Berardi - Linux hardening and security measures against Memory corruption

Davide Berardi - Linux hardening and security measures against Memory corruption
FØCAL Boston AiR - Computer Vision Tracing and Hardware Simulation

FØCAL Boston AiR - Computer Vision Tracing and Hardware Simulation
OpenWorld 2018 - Common Application Developer Disasters

OpenWorld 2018 - Common Application Developer Disasters
04 - I love my OS, he protects me (sometimes, in specific circumstances)

04 - I love my OS, he protects me (sometimes, in specific circumstances)
re:Invent 2019 BPF Performance Analysis at Netflix

re:Invent 2019 BPF Performance Analysis at Netflix
OSDC 2017 - Werner Fischer - Linux performance profiling and monitoring

OSDC 2017 - Werner Fischer - Linux performance profiling and monitoring
Más de Ruo Ando
Más de Ruo Ando (20)
SaaSアカデミー for バックオフィス アイドルと学ぶDX講座 ~アイドル戦略に見るDXを専門家が徹底解説~

SaaSアカデミー for バックオフィス アイドルと学ぶDX講座 ~アイドル戦略に見るDXを専門家が徹底解説~
AI(機械学習・深層学習)との協働スキルとOperational AIの事例紹介 @ ビジネス+ITセミナー 2020年11月

AI(機械学習・深層学習)との協働スキルとOperational AIの事例紹介 @ ビジネス+ITセミナー 2020年11月
Último
Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR

Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR9953056974 Low Rate Call Girls In Saket, Delhi NCR
Último (20)
Call Girls Delhi {Jodhpur} 9711199012 high profile service

Call Girls Delhi {Jodhpur} 9711199012 high profile service
Instrumentation, measurement and control of bio process parameters ( Temperat...

Instrumentation, measurement and control of bio process parameters ( Temperat...
TechTAC® CFD Report Summary: A Comparison of Two Types of Tubing Anchor Catchers

TechTAC® CFD Report Summary: A Comparison of Two Types of Tubing Anchor Catchers
INFLUENCE OF NANOSILICA ON THE PROPERTIES OF CONCRETE

INFLUENCE OF NANOSILICA ON THE PROPERTIES OF CONCRETE
Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR

Call Us -/9953056974- Call Girls In Vikaspuri-/- Delhi NCR
Decoding Kotlin - Your guide to solving the mysterious in Kotlin.pptx

Decoding Kotlin - Your guide to solving the mysterious in Kotlin.pptx
CCS355 Neural Network & Deep Learning Unit II Notes with Question bank .pdf

CCS355 Neural Network & Deep Learning Unit II Notes with Question bank .pdf
Study on Air-Water & Water-Water Heat Exchange in a Finned Tube Exchanger

Study on Air-Water & Water-Water Heat Exchange in a Finned Tube Exchanger
What are the advantages and disadvantages of membrane structures.pptx

What are the advantages and disadvantages of membrane structures.pptx
Gurgaon ✡️9711147426✨Call In girls Gurgaon Sector 51 escort service

Gurgaon ✡️9711147426✨Call In girls Gurgaon Sector 51 escort service
An introduction to Semiconductor and its types.pptx

An introduction to Semiconductor and its types.pptx
An experimental study in using natural admixture as an alternative for chemic...

An experimental study in using natural admixture as an alternative for chemic...
Master Thread and Worker Thread with Spin Locks and Realloc
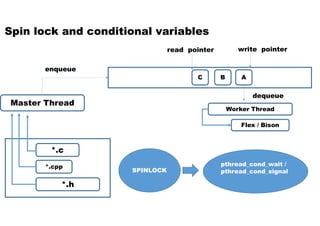
- 1. Master Thread Worker Thread Flex / Bison A enqueue write pointer *.c *.cpp *.h BC Spin lock and conditional variables dequeue read pointer SPINLOCK pthread_cond_wait / pthread_cond_signal
- 3. User-after-free (aka heap spray) : CVE-2013-4371 Xen hypervisor http://blog.tempest.com.br/breno-cunha/perspectives-on-exploit-development-and-cyber- attacks.html create() free() realloc() use() Jump to payload on heap ROP + Shellcode int *tmp = (int*)realloc(k,(N+1)*sizeof(int)); if( tmp!=NULL ){ k = tmp; puts("________realloc(k)_________"); for(i=0; i<N+1; i++){ printf("&k[%d]:%p , k[%d]=%d¥n",i,&k[i],i,k[i]); } } realloc() allocates new area if realloc() fails to expand the pointer of first argument. Consequently, the string is saved but the address is changed. If too many realloc() is invoked, DoS is enabled by adversary and an arbitrary malicious string can be executed. void* realloc (void* ptr, size_t size);
- 4. version search depth EMPTY (LEAF) EDGE version search depth EMPTY (LEAF) EDGE xen440 1 1 15xen433 1 1 7 xen440 2 6 62xen433 2 5 36 xen440 3 68 876xen433 3 74 998 xen412 1 0 8xen453 1 1 15 xen412 2 1 17xen453 2 6 65 xen412 3 10 119xen453 3 11 208 xen414 1 0 8xen432 1 1 7 xen414 2 1 17xen432 2 5 36 xen414 3 10 119xen432 3 88 1223 xen410 2 1 17xen450 1 1 15 xen410 3 10 122xen450 2 6 65 xen441 1 1 15xen450 3 11 203 xen441 2 6 62xen451 1 1 15 xen441 3 83 1068xen451 2 6 65 xen415 1 0 8xen451 3 10 201 xen415 2 1 17xen434 1 1 7 xen415 3 10 119xen434 2 5 36 xen422 1 0 8xen434 3 81 1043 xen422 2 3 36xen455 1 1 15 xen422 3 87 1525xen455 2 6 65 xen424 1 0 8xen455 3 12 217 xen424 2 3 36xen430 1 1 7 xen424 3 80 1476xen430 2 5 36 xen413 1 0 8xen430 3 62 761 xen413 2 1 17xen442 1 1 15 xen413 3 10 119xen442 2 6 62 xen425 1 0 8xen442 3 68 876 xen440 : libxl_list_cpupool : 3 : 68 : 876 psycopg2.Operational Error: FATAL: sorry, too many clients already FATAL: sorry, too many clients already xen440 : libxl_list_cpupool : 4 : 297 : 4811 xen414 : libxl_list_cpupool : 3 : 10 : 119 xen414 : libxl_list_cpupool : 4 : 10 : 123 xen414 : libxl_list_cpupool : 5 : 10 : 127 LIMITATION: Upper bound of PostgreSQL: search depth > 4 (path explotion)
