How to Create a Successful Corporate-Liable Mobility Program
•
0 recomendaciones•1,600 vistas
Frost & Sullivan research shows that more and more companies are going mobile - providing smart phones, tablets, and apps for their end users in record numbers. But when deploying mobile devices to their end users, many companies do not have a clear picture of the total costs or of the value of enabling a mobile workforce. This infographic explores the cost considerations and the value of a corporate-liable mobility program and examines the top mobile apps that businesses deploy as well as the top mobile app drivers. In addition, the infographic covers the key considerations for planning a mobile deployment and the capabilities to look for in a corporate-liable mobility program partner.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Groveport Madison School District near Columbus, Ohio isn’t a wealthy school district. But with its small IT department, it wanted to provide a more one-on-one learning experience with a blended learning platform. The district needed a cost effective one-to-one technology solution that could be implemented and managed by the district. Read this case study to find out how the district has rolled out more than 2,500 Samsung Chromebooks together with Google Apps for Education.Groveport Madison School District; Digital Learning Engages Students, Empower...

Groveport Madison School District; Digital Learning Engages Students, Empower...Samsung Business USA
Recomendados
Groveport Madison School District near Columbus, Ohio isn’t a wealthy school district. But with its small IT department, it wanted to provide a more one-on-one learning experience with a blended learning platform. The district needed a cost effective one-to-one technology solution that could be implemented and managed by the district. Read this case study to find out how the district has rolled out more than 2,500 Samsung Chromebooks together with Google Apps for Education.Groveport Madison School District; Digital Learning Engages Students, Empower...

Groveport Madison School District; Digital Learning Engages Students, Empower...Samsung Business USA
Más contenido relacionado
Más de Samsung Business USA
Más de Samsung Business USA (20)
6 ways Samsung’s Interactive Display powered by Android changes the classroom

6 ways Samsung’s Interactive Display powered by Android changes the classroom
10 reasons to choose Galaxy Tab S9 for work on the go

10 reasons to choose Galaxy Tab S9 for work on the go
13 things you didn’t know you could do with the S Pen

13 things you didn’t know you could do with the S Pen
8 ways ViewFinity monitors set the standard for professionals

8 ways ViewFinity monitors set the standard for professionals
5 Ways Smart Hospital Rooms Can Improve The Patient Experience

5 Ways Smart Hospital Rooms Can Improve The Patient Experience
INFOGRAPHIC_10-field-ready-features-of-the-Tab-Active4_FINAL.pdf

INFOGRAPHIC_10-field-ready-features-of-the-Tab-Active4_FINAL.pdf
The best monitors for teachers: 5 features every educator needs

The best monitors for teachers: 5 features every educator needs
6 smart ways Samsung's 85-inch Interactive Display changes the classroom

6 smart ways Samsung's 85-inch Interactive Display changes the classroom
13 things you didn't know you could do with the S Pen

13 things you didn't know you could do with the S Pen
10 reasons to choose Galaxy Tab S8 for work on the go

10 reasons to choose Galaxy Tab S8 for work on the go
9 benefits of mobilizing patient care with hospital technology

9 benefits of mobilizing patient care with hospital technology
6 ways Samsung Kiosk gives retailers an all-in-one self-service solution

6 ways Samsung Kiosk gives retailers an all-in-one self-service solution
How does mobile strategy influence your customer journey?

How does mobile strategy influence your customer journey?
Último
Último (20)
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Navi Mumbai Call Girls 🥰 8617370543 Service Offer VIP Hot Model

Navi Mumbai Call Girls 🥰 8617370543 Service Offer VIP Hot Model
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
How to Create a Successful Corporate-Liable Mobility Program
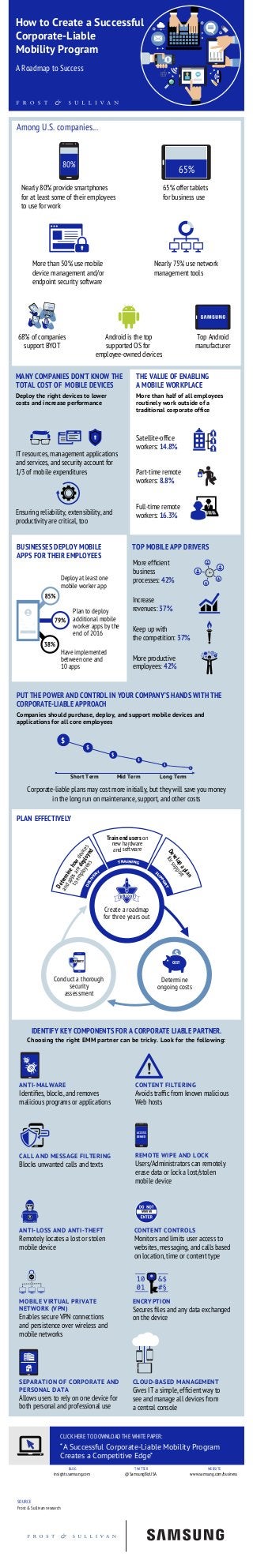
- 1. 68% of companies support BYOT Android is the top supported OS for employee-owned devices Top Android manufacturer Have implemented between one and 10 apps Plan to deploy additional mobile worker apps by the end of 2016 Deploy at least one mobile worker app How to Create a Successful Corporate-Liable Mobility Program A Roadmap to Success 80% $ 65% Frost & Sullivan research BLOG insights.samsung.com TWITTER @SamsungBizUSA WEBSITE www.samsung.com/business SOURCE CLICK HERE TO DOWNLOAD THE WHITE PAPER: “A Successful Corporate-Liable Mobility Program Creates a Competitive Edge” Nearly 80% provide smartphones for at least some of their employees to use for work Corporate-liable plans may cost more initially, but they will save you money in the long run on maintenance, support, and other costs 65% offer tablets for business use More than 50% use mobile device management and/or endpoint security software Nearly 75% use network management tools MANY COMPANIES DON’T KNOW THE TOTAL COST OF MOBILE DEVICES Deploy the right devices to lower costs and increase performance THE VALUE OF ENABLING A MOBILE WORKPLACE More than half of all employees routinely work outside of a traditional corporate office IT resources, management applications and services, and security account for 1/3 of mobile expenditures Ensuring reliability, extensibility, and productivity are critical, too Satellite-office workers: 14.8% Part-time remote workers: 8.8% Full-time remote workers: 16.3% BUSINESSES DEPLOY MOBILE APPS FOR THEIR EMPLOYEES TOP MOBILE APP DRIVERS More efficient business processes: 42% More productive employees: 42% Keep up with the competition: 37% Increase revenues: 37% PUT THE POWER AND CONTROL IN YOUR COMPANY’S HANDS WITH THE CORPORATE-LIABLE APPROACH Companies should purchase, deploy, and support mobile devices and applications for all core employees PLAN EFFECTIVELY Short Term Mid Term Long Term Conduct a thorough security assessment COST Determine ongoing costs ROLLOUT DELIVE RY S U PPORT TRAINING Create a roadmap for three years out Determinehowdevices andappsaredeployed toemployees Developaplan forsupport Train end users on new hardware and software SECURITYSECURITY IDENTIFY KEY COMPONENTS FOR A CORPORATE LIABLE PARTNER. Choosing the right EMM partner can be tricky. Look for the following: ANTI-MALWARE Identifies, blocks, and removes malicious programs or applications CONTENT FILTERING Avoids traffic from known malicious Web hosts CALL AND MESSAGE FILTERING Blocks unwanted calls and texts REMOTE WIPE AND LOCK Users/Administrators can remotely erase data or lock a lost/stolen mobile device ANTI-LOSS AND ANTI-THEFT Remotely locates a lost or stolen mobile device CONTENT CONTROLS Monitors and limits user access to websites, messaging, and calls based on location, time or content type MOBILE VIRTUAL PRIVATE NETWORK (VPN) Enables secure VPN connections and persistence over wireless and mobile networks ENCRYPTION Secures files and any data exchanged on the device SEPARATION OF CORPORATE AND PERSONAL DATA Allows users to rely on one device for both personal and professional use CLOUD-BASED MANAGEMENT Gives IT a simple, efficient way to see and manage all devices from a central console ACCESS DENIED WWW Among U.S. companies... $ $ $ $ $ $
