IT Security for Small Businesses
•
0 recomendaciones•82 vistas
For small businesses, the importance of IT security cannot be understated. This infographic explains how putting in place proper security measures is more than just the right thing to do – its an essential step in actually building your business.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
Último
Último (7)
Salma Karina Hayat - The Ultimate Guide to Becoming a Successful Business Adv...

Salma Karina Hayat - The Ultimate Guide to Becoming a Successful Business Adv...
Bromazolam CAS 71368-80-4 high quality opiates, Safe transportation, 99% pure

Bromazolam CAS 71368-80-4 high quality opiates, Safe transportation, 99% pure
MBA 674 Final Research Paper Livengood Harnessing Entrepreneurial Spirit .pdf

MBA 674 Final Research Paper Livengood Harnessing Entrepreneurial Spirit .pdf
Proposal Qurban Ma'had Tahfizhul Qur'an Ahlus Shuffah 1445 H.pdf

Proposal Qurban Ma'had Tahfizhul Qur'an Ahlus Shuffah 1445 H.pdf
Destacado
More than Just Lines on a Map: Best Practices for U.S Bike Routes
This session highlights best practices and lessons learned for U.S. Bike Route System designation, as well as how and why these routes should be integrated into bicycle planning at the local and regional level.
Presenters:
Presenter: Kevin Luecke Toole Design Group
Co-Presenter: Virginia Sullivan Adventure Cycling AssociationMore than Just Lines on a Map: Best Practices for U.S Bike Routes

More than Just Lines on a Map: Best Practices for U.S Bike RoutesProject for Public Spaces & National Center for Biking and Walking
Destacado (20)
Content Methodology: A Best Practices Report (Webinar)

Content Methodology: A Best Practices Report (Webinar)
How to Prepare For a Successful Job Search for 2024

How to Prepare For a Successful Job Search for 2024
Social Media Marketing Trends 2024 // The Global Indie Insights

Social Media Marketing Trends 2024 // The Global Indie Insights
Trends In Paid Search: Navigating The Digital Landscape In 2024

Trends In Paid Search: Navigating The Digital Landscape In 2024
5 Public speaking tips from TED - Visualized summary

5 Public speaking tips from TED - Visualized summary
Google's Just Not That Into You: Understanding Core Updates & Search Intent

Google's Just Not That Into You: Understanding Core Updates & Search Intent
The six step guide to practical project management

The six step guide to practical project management
Beginners Guide to TikTok for Search - Rachel Pearson - We are Tilt __ Bright...

Beginners Guide to TikTok for Search - Rachel Pearson - We are Tilt __ Bright...
Unlocking the Power of ChatGPT and AI in Testing - A Real-World Look, present...

Unlocking the Power of ChatGPT and AI in Testing - A Real-World Look, present...
More than Just Lines on a Map: Best Practices for U.S Bike Routes

More than Just Lines on a Map: Best Practices for U.S Bike Routes
Ride the Storm: Navigating Through Unstable Periods / Katerina Rudko (Belka G...

Ride the Storm: Navigating Through Unstable Periods / Katerina Rudko (Belka G...
IT Security for Small Businesses
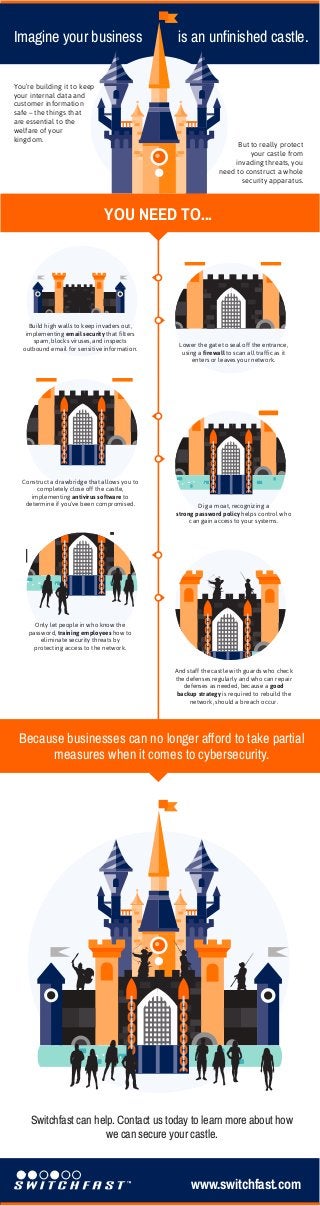
- 1. Imagine your business is an unfinished castle. You’re building it to keep your internal data and customer information safe – the things that are essential to the welfare of your kingdom. But to really protect your castle from invading threats, you need to construct a whole security apparatus. YOU NEED TO... Build high walls to keep invaders out, implementing email security that filters spam, blocks viruses, and inspects outbound email for sensitive information. Construct a drawbridge that allows you to completely close off the castle, implementing antivirus software to determine if you’ve been compromised. Lower the gate to seal off the entrance, using a firewall to scan all traffic as it enters or leaves your network. Dig a moat, recognizing a strong password policy helps control who can gain access to your systems. Only let people in who know the password, training employees how to eliminate security threats by protecting access to the network. And staff the castle with guards who check the defenses regularly and who can repair defenses as needed, because a good backup strategy is required to rebuild the network, should a breach occur. Because businesses can no longer afford to take partial measures when it comes to cybersecurity. Switchfast can help. Contact us today to learn more about how we can secure your castle. www.switchfast.com
