Ransomware: Are you Protected?
•
4 recomendaciones•1,137 vistas
Ransomware has quickly emerged as one of the most dangerous cyber threats facing both organizations and consumers, with global losses now likely running to hundreds of millions of dollars. Adopting the Veritas multilayered strategy approach to security minimizes the chance of infection.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
We began to see renewed innovation in the threat actor space in mid to late 2018. This trend has continued to surface in 2019. Threat actors (black hat hackers) have increasingly leveraged prior attacks, data collection and mining, and likely AI to create a new type of highly targeted, very sophisticated cyber attacks. Explore this new threat technique, prevention and detection strategies, and some of the most effective strategies to balance compliance and customer requirements with practical cyber security. 2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...

2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...Internetwork Engineering (IE)
Más contenido relacionado
La actualidad más candente
We began to see renewed innovation in the threat actor space in mid to late 2018. This trend has continued to surface in 2019. Threat actors (black hat hackers) have increasingly leveraged prior attacks, data collection and mining, and likely AI to create a new type of highly targeted, very sophisticated cyber attacks. Explore this new threat technique, prevention and detection strategies, and some of the most effective strategies to balance compliance and customer requirements with practical cyber security. 2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...

2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...Internetwork Engineering (IE)
La actualidad más candente (6)
2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...

2019 NCLGISA Spring Cybersecurity Threats & Trends: Blended Threats and Smart...
Infographic: Ransomware is the leading form of cyber attack

Infographic: Ransomware is the leading form of cyber attack
Similar a Ransomware: Are you Protected?
Similar a Ransomware: Are you Protected? (20)
13 Ransomware Statistics That Will Make You Rethink Data Protection 

13 Ransomware Statistics That Will Make You Rethink Data Protection
Symantec Internet Security Threat Report 2014 - Volume 19

Symantec Internet Security Threat Report 2014 - Volume 19
What Are Cyber Attacks All About? | Cyberroot Risk Advisory

What Are Cyber Attacks All About? | Cyberroot Risk Advisory
13 Ransomware Statistics That Will Make You Rethink Data Protection

13 Ransomware Statistics That Will Make You Rethink Data Protection
Más de Veritas Technologies LLC
We are experiencing IT climate change. Inundated we are, daily, with a barrage of “Cloud-ready” solutions that promise to transform, supercharge or in some other way substantial improve your business. Truth is, we’ve all seen this movie before and there is no ending, only a story arch. Technologies come and go and our ability to maximize the return on these solutions is what we makes for a successful adoption. Ask yourself, with all of the promise of the public cloud, how much is hype vs. reality. More details in the presentation.
How to Extend Availability to the Application Layer Across the Hybrid Cloud -...

How to Extend Availability to the Application Layer Across the Hybrid Cloud -...Veritas Technologies LLC
The joint presentation session on Get trust and confidence to manage your data in hybrid-IT environments! with Mr Matsumoto, VP Fujitsu Cloud Service, Mr Takenoshita who is our end user, and Ryuta Takai, Director, Technology Sales of Veritas at Fujitsu Forum 2019 Tokyo on 17 May 2019. Get trust and confidence to manage your data in hybrid it environments japanese

Get trust and confidence to manage your data in hybrid it environments japaneseVeritas Technologies LLC
This presentation from the Gartner IT Infrastructure Operations & Cloud Strategies Conference is about the rise of the modern workload. Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...

Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...Veritas Technologies LLC
This includes two presentations on 360 data management, as well as how to take control over the most valuable asset in your enterprise - data. VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...

VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...Veritas Technologies LLC
Más de Veritas Technologies LLC (20)
Veritas Vision Solution Day 2020, Istanbul, Turkey

Veritas Vision Solution Day 2020, Istanbul, Turkey
Experience Data Management Clarity with Veritas - VMworld 2019 Presentation

Experience Data Management Clarity with Veritas - VMworld 2019 Presentation
How to Extend Availability to the Application Layer Across the Hybrid Cloud -...

How to Extend Availability to the Application Layer Across the Hybrid Cloud -...
Get trust and confidence to manage your data in hybrid it environments japanese

Get trust and confidence to manage your data in hybrid it environments japanese
VSD Paris 2018: Vertical Use Case - Telco Services

VSD Paris 2018: Vertical Use Case - Telco Services
VSD Paris 2018: Vertical Use Case - Banking, Finance, Insurance

VSD Paris 2018: Vertical Use Case - Banking, Finance, Insurance
Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...

Gartner IT Infrastructure Operations & Cloud Strategies Conference 2018: Rise...
VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...

VSD Zurich 2018: 360 Data Management and Take Control Over the Most Valuable ...
VSD Zurich 2018: The Secret to Successful Digital Transformation

VSD Zurich 2018: The Secret to Successful Digital Transformation
Take Control Over Storage Costs with Intuitive Management and Simplicity

Take Control Over Storage Costs with Intuitive Management and Simplicity
VSD Seoul 2018: VMware Cloud Foundation on "The Future of Private Cloud"

VSD Seoul 2018: VMware Cloud Foundation on "The Future of Private Cloud"
VSD Seoul 2018: a Veritas customer case with Meritz Fire Insurance

VSD Seoul 2018: a Veritas customer case with Meritz Fire Insurance
Último
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Último (20)
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Ransomware: Are you Protected?
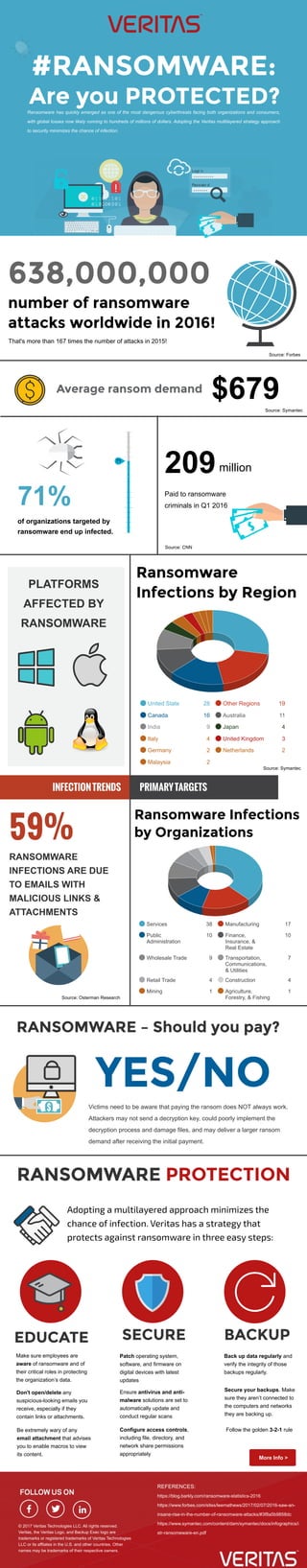
- 1. Ransomware has quickly emerged as one of the most dangerous cyberthreats facing both organizations and consumers, with global losses now likely running to hundreds of millions of dollars. Adopting the Veritas multilayered strategy approach to security minimizes the chance of infection. 71% of organizations targeted by ransomware end up infected. 209 Paid to ransomware criminals in Q1 2016 United State 28 Other Regions 19 Canada 16 Australia 11 India 9 Japan 4 Italy 4 United Kingdom 3 Germany 2 Netherlands 2 Malaysia 2 Services 38 Manufacturing 17 Public Administration 10 Finance, Insurance, & Real Estate 10 Wholesale Trade 9 Transportation, Communications, & Utilities 7 Retail Trade 4 Construction 4 Mining 1 Agriculture, Forestry, & Fishing 1 PLATFORMS AFFECTED BY RANSOMWARE Victims need to be aware that paying the ransom does NOT always work. Attackers may not send a decryption key, could poorly implement the decryption process and damage files, and may deliver a larger ransom demand after receiving the initial payment. Make sure employees are aware of ransomware and of their critical roles in protecting the organization’s data. RANSOMWARE INFECTIONS ARE DUE TO EMAILS WITH MALICIOUS LINKS & ATTACHMENTS $679 million That's more than 167 times the number of attacks in 2015! Source: CNN Source: Symantec Source: Symantec Source: Osterman Research https://blog.barkly.com/ransomware-statistics-2016 https://www.forbes.com/sites/leemathews/2017/02/07/2016-saw-an- insane-rise-in-the-number-of-ransomware-attacks/#3f8a5b9858dc https://www.symantec.com/content/dam/symantec/docs/infographics/i str-ransomeware-en.pdf REFERENCES: Patch operating system, software, and firmware on digital devices with latest updates Back up data regularly and verify the integrity of those backups regularly. Secure your backups. Make sure they aren’t connected to the computers and networks they are backing up. Follow the golden 3-2-1 ruleConfigure access controls, including file, directory, and network share permissions appropriately Ensure antivirus and anti- malware solutions are set to automatically update and conduct regular scans Don't open/delete any suspicious-looking emails you receive, especially if they contain links or attachments. Be extremely wary of any email attachment that advises you to enable macros to view its content. © 2017 Veritas Technologies LLC. All rights reserved. Veritas, the Veritas Logo, and Backup Exec logo are trademarks or registered trademarks of Veritas Technologies LLC or its affliates in the U.S. and other countries. Other names may be trademarks of their respective owners. More Info > Source: Forbes
