Black berry software ruled not safe enough for essential government work
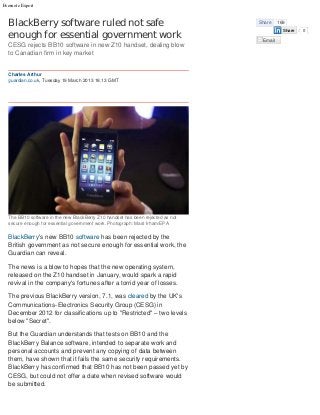
- 1. Evernote Export BlackBerry software ruled not safe Share 169 enough for essential government work Share 0 Email CESG rejects BB10 software in new Z10 handset, dealing blow to Canadian firm in key market Charles Arthur guardian.co.uk, Tuesday 19 March 2013 18.13 GMT The BB10 software in the new BlackBerry Z10 handset has been rejected as not secure enough for essential government work. Photograph: Mast Irham/EPA BlackBerry's new BB10 software has been rejected by the British government as not secure enough for essential work, the Guardian can reveal. The news is a blow to hopes that the new operating system, released on the Z10 handset in January, would spark a rapid revival in the company's fortunes after a torrid year of losses. The previous BlackBerry version, 7.1, was cleared by the UK's Communications-Electronics Security Group (CESG) in December 2012 for classifications up to "Restricted" – two levels below "Secret". But the Guardian understands that tests on BB10 and the BlackBerry Balance software, intended to separate work and personal accounts and prevent any copying of data between them, have shown that it fails the same security requirements. BlackBerry has confirmed that BB10 has not been passed yet by CESG, but could not offer a date when revised software would be submitted.
- 2. Evernote Export That is a blow because the Z10 and its upcoming keyboard- based version, the Q10, are high-priced devices intended to win back corporate customers who have begun to migrate to Apple's iPhone or to Android devices, or to replace older BlackBerry 7 phones. Nor has the company offered a clear date when it will fix the weakness. Missing out on government business could cost BlackBerry millions in lost revenues, even if rivals are unable to fill the same security space: the government and NHS are two of its biggest clients in the UK, with tens of thousands of users. Analyst reports also suggest that sales in the UK of the touchscreen Z10 handset, the first to run BB10, are slowing after an initial spurt among consumers when they went on sale in January, leaving sellers with surplus stock. The Z10 goes on sale in the US on Friday, with the company seeking to rebuild its share of the smartphone market there, which has plummeted from a high of 22% in September 2010 with 21m users to just 5.9% and 7.6m users in January according to ComScore. But James Faucette at the stockbrokers Pacific Crest, who has a "sell" rating on BlackBerry, said in a research note looking at sales in the UK and Canada that "sell-through run-rates for the Z10 have declined meaningfully in the weeks following launch. We believe carriers and third-party retailers in the UK are well above typically targeted inventory levels" and that retailers Carphone Warhouse and Phones4U have begun discounting the handsets. "We are concerned that … may ultimately push the Z10 downmarket" and hit profit margins, he told clients. He added that he thinks Canadian stores and carriers are also approaching the same point BlackBerry said in a statement: "We have a long-established relationship with CESG and we remain the only mobile solution approved for use at 'Restricted' when configured in accordance with CESG guidelines. This level of approval only comes following a process which is rigorous and absolutely necessary given the highly confidential nature of the communications being transmitted. "The current restructuring of this approval process, due to the Government Protective Marking Scheme review and the new CESG Commercial Product Assurance scheme has an impact on the timeline for BlackBerry 10 to receive a similar level of approval. The US government's FIPS 140-2 certification of
- 3. Evernote Export BlackBerry 10 and the selection of BlackBerry 10 by the German Procurement Office and Federal Office for Information Security underline how our new platform continues to set the standard for government communications. "We are continuing to work closely with CESG on the approval of BlackBerry 10 and we're confident that BlackBerry 10 will only strengthen our position as the mobile solution of choice for the UK government." • Canada's industry minister has declined to say whether he would block any attempted takeover of BlackBerry by the Chinese PC and smartphone maker Lenovo. Christian Paradis told Reuters "I hope BlackBerry will continue to be a Canadian champion in the world, that it grows organically." But, he added, "we don't know what might happen. The market is very aggressive. When you talk about the telecoms sector … this is a very, very aggressive sector." Asked whether he would block a bid from Lenovo, mooted last week in an interview with that company, Paradis said "As the industry minister, I don't want to send a signal and I don't want it to look like I prejudged a deal or not." The Canadian government could block the deal on national security grounds. Last year, the Chinese state-owned oil company CNOOC bought Canadian energy firm Nexen, but it provoked a storm. Analysts believe the US and UK governments might block a similar Chinese bid for BlackBerry because of its importance to secure email. Updated: corrected expansion of CESG.
