Hermes jms ibmmq-ssl-channel-release1
•
0 recomendaciones•1,757 vistas
This document discusses how to configure HermesJMS to connect to an SSL-enabled WebSphere MQ queue manager without mutual authentication. It involves importing the self-signed certificate of the queue manager into the Java keystore and configuring HermesJMS to use the IBM MQ provider libraries and specify SSL settings to match the queue manager configuration. Testing showed that HermesJMS could successfully retrieve data over the SSL channel after making these configuration changes.
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Recomendados
Más contenido relacionado
Destacado
Destacado (13)
BUZ HOKEYİ DÜNYA ŞAMPİYONASI ŞUTLARIN VE GOL OLAN ŞUTLARIN ANALİZİ (18 YAŞAL...

BUZ HOKEYİ DÜNYA ŞAMPİYONASI ŞUTLARIN VE GOL OLAN ŞUTLARIN ANALİZİ (18 YAŞAL...
Spor Malzemeleri Satan İşletmelerde Elektronik Ticaret Uygulamalarinin Değerl...

Spor Malzemeleri Satan İşletmelerde Elektronik Ticaret Uygulamalarinin Değerl...
Sport Rehabiliton Program After Natural Disaster, 1999 TURKEY

Sport Rehabiliton Program After Natural Disaster, 1999 TURKEY
Türkiye’deki Üniversitelerin Beden Eğitimi ve Spor Yüksekokullarının Web Sayf...

Türkiye’deki Üniversitelerin Beden Eğitimi ve Spor Yüksekokullarının Web Sayf...
A Research on Individual Innovativeness Levels of Football Referees (Kocaeli ...

A Research on Individual Innovativeness Levels of Football Referees (Kocaeli ...
Powerpoint Presentation On Animated Flipbook Ryan Mcginty

Powerpoint Presentation On Animated Flipbook Ryan Mcginty
Similar a Hermes jms ibmmq-ssl-channel-release1
Similar a Hermes jms ibmmq-ssl-channel-release1 (20)
Building Better Backdoors with WMI - DerbyCon 2017

Building Better Backdoors with WMI - DerbyCon 2017
Moving a Windows environment to the cloud - DevOps Galway Meetup

Moving a Windows environment to the cloud - DevOps Galway Meetup
VMworld 2013: ESXi Native Networking Driver Model - Delivering on Simplicity ...

VMworld 2013: ESXi Native Networking Driver Model - Delivering on Simplicity ...
VMworld 2013: VMware Horizon View Troubleshooting: Looking under the Hood

VMworld 2013: VMware Horizon View Troubleshooting: Looking under the Hood
Modern tooling to assist with developing applications on FreeBSD

Modern tooling to assist with developing applications on FreeBSD
DB proxy server test: run tests on tens of virtual machines with Jenkins, Vag...

DB proxy server test: run tests on tens of virtual machines with Jenkins, Vag...
Último
Último (20)
How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf

How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf
Secure Zero Touch enabled Edge compute with Dell NativeEdge via FDO _ Brad at...

Secure Zero Touch enabled Edge compute with Dell NativeEdge via FDO _ Brad at...
Your enemies use GenAI too - staying ahead of fraud with Neo4j

Your enemies use GenAI too - staying ahead of fraud with Neo4j
Portal Kombat : extension du réseau de propagande russe

Portal Kombat : extension du réseau de propagande russe
Collecting & Temporal Analysis of Behavioral Web Data - Tales From The Inside

Collecting & Temporal Analysis of Behavioral Web Data - Tales From The Inside
Easier, Faster, and More Powerful – Notes Document Properties Reimagined

Easier, Faster, and More Powerful – Notes Document Properties Reimagined
Microsoft CSP Briefing Pre-Engagement - Questionnaire

Microsoft CSP Briefing Pre-Engagement - Questionnaire
Tales from a Passkey Provider Progress from Awareness to Implementation.pptx

Tales from a Passkey Provider Progress from Awareness to Implementation.pptx
Long journey of Ruby Standard library at RubyKaigi 2024

Long journey of Ruby Standard library at RubyKaigi 2024
(Explainable) Data-Centric AI: what are you explaininhg, and to whom?

(Explainable) Data-Centric AI: what are you explaininhg, and to whom?
1111 ChatGPT Prompts PDF Free Download - Prompts for ChatGPT

1111 ChatGPT Prompts PDF Free Download - Prompts for ChatGPT
ASRock Industrial FDO Solutions in Action for Industrial Edge AI _ Kenny at A...

ASRock Industrial FDO Solutions in Action for Industrial Edge AI _ Kenny at A...
Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx

Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx
Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...

Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...
TEST BANK For, Information Technology Project Management 9th Edition Kathy Sc...

TEST BANK For, Information Technology Project Management 9th Edition Kathy Sc...
Hermes jms ibmmq-ssl-channel-release1
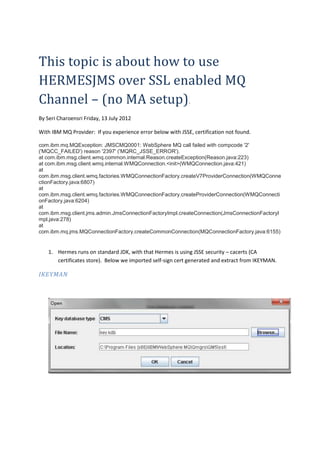
- 1. This topic is about how to use HERMESJMS over SSL enabled MQ Channel – (no MA setup). By Seri Charoensri Friday, 13 July 2012 With IBM MQ Provider: If you experience error below with JSSE, certification not found. com.ibm.mq.MQException: JMSCMQ0001: WebSphere MQ call failed with compcode '2' ('MQCC_FAILED') reason '2397' ('MQRC_JSSE_ERROR'). at com.ibm.msg.client.wmq.common.internal.Reason.createException(Reason.java:223) at com.ibm.msg.client.wmq.internal.WMQConnection.<init>(WMQConnection.java:421) at com.ibm.msg.client.wmq.factories.WMQConnectionFactory.createV7ProviderConnection(WMQConne ctionFactory.java:6807) at com.ibm.msg.client.wmq.factories.WMQConnectionFactory.createProviderConnection(WMQConnecti onFactory.java:6204) at com.ibm.msg.client.jms.admin.JmsConnectionFactoryImpl.createConnection(JmsConnectionFactoryI mpl.java:278) at com.ibm.mq.jms.MQConnectionFactory.createCommonConnection(MQConnectionFactory.java:6155) 1. Hermes runs on standard JDK, with that Hermes is using JSSE security – cacerts (CA certificates store). Below we imported self-sign cert generated and extract from IKEYMAN. IKEYMAN
- 3. ukplpzDWUJ/f7Kof6cizSxYgvVjKYD2f4fEfgKHPU8hs/4UO0czdOM6cPobLOU6k5I9zN8o4eFqm V/iuPyhswriJG1gQH4f0dA1HL0Ruv9kbvt0m46qroYXU5Ka6slc= -----END CERTIFICATE----- HermesJMS JVM C:Program Files (x86)Javajdk1.6.0_13jrelibsecuritycacerts Keytool 2. For self-sign cert from MQ, you will need to import the cert into cacerts keystore, so that HERMES can hand-shake with MQ over SSL. C:Program Files (x86)Javajdk1.6.0_13jrebin>keytool -import -trustcacerts -alias qm5 -file ..libsecurityQM12345-certQM5_cert.arm -keystore ..libsecuritycacerts Enter keystore password: changeit (default JSSE CA keystore) Owner: CN=qm5, C=US Issuer: CN=qm5, C=US Serial number: -54f5d8343411e1b8 Valid from: Fri Jul 20 21:14:59 EST 2012 until: Sun Jul 21 21:14:59 EST 2013 Certificate fingerprints: MD5: 7A:2C:20:3A:CE:94:2B:44:F0:C4:65:C8:FD:A4:17:9F SHA1: B5:D0:68:84:75:D2:6D:ED:61:AC:C6:32:87:F5:0C:69:28:AC:C0:6E Signature algorithm name: MD5withRSA Version: 3 Trust this certificate? [no]: y Certificate was added to keystore C:Program Files (x86)Javajdk1.6.0_13jrebin> HERMES JMS setting IBM MQ 7 Provider Lib: - don’t need all of those lib – I am lazy to pick just the jars required.
- 5. C:Program Files (x86)IBMWebSphere MQJavalibcom.ibm.mq.jar C:Program Files (x86)IBMWebSphere MQJavalibcom.ibm.mq.jms.Nojndi.jar C:Program Files (x86)IBMWebSphere MQJavalibcom.ibm.mq.soap.jar C:Program Files (x86)IBMWebSphere MQJavalibcom.ibm.mqjms.jar C:Program Files (x86)IBMWebSphere MQJavalibcommonservices.jar C:Program Files (x86)IBMWebSphere MQJavalibconnector.jar C:Program Files (x86)IBMWebSphere MQJavalibdhbcore.jar C:Program Files (x86)IBMWebSphere MQJavalibfscontext.jar C:Program Files (x86)IBMWebSphere MQJavalibjms.jar C:Program Files (x86)IBMWebSphere MQJavalibjndi.jar C:Program Files (x86)IBMWebSphere MQJavalibjta.jar C:Program Files (x86)IBMWebSphere MQJavalibldap.jar SSLCipherSuite SSL_RSA_WITH_3DES_EDE_CBC_SHA channel qm5_ch1 hostName 127.0.0.1 port 1418 queueManager QM5 transportType 1 IBM MQ setup On the MQ we have “TRIPLE_DES_SHA_SA” SSL setup – no client SSL (SSLCAUTH) required. Ie. Trust the MQ server only, no Mutual Authentication setup.
- 6. NOTE: we have not set the SSLCAUTH to be required, or lock down the DN name specification to only allow clients with the DN name come through. Test result We success fully retrieve data over SSL-enabled channel.
