The High Stakes of Business Security [Infographic]
•
3 recomendaciones•23,006 vistas
A look at the global trends in IT security risks and reasons why security practices and policies need to evolve in order to handle threats from disruptive technologies, cybercrime and compliance mandates. Access the full report conducted by the Ponemon Institute and sponsored by Citrix: http://buff.ly/2iXDPM3
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
Más contenido relacionado
Destacado
Destacado (12)
Shadow IT - What is it, why it happens and how to resolve

Shadow IT - What is it, why it happens and how to resolve
Unified Endpoint Management: Security & Productivity for the Mobile Enterprise

Unified Endpoint Management: Security & Productivity for the Mobile Enterprise
Más de Citrix
Más de Citrix (20)
Maximize your Investment in Microsoft Office 365 with Citrix Workspace 

Maximize your Investment in Microsoft Office 365 with Citrix Workspace
Deploying Citrix XenApp & XenDesktop Service on Google Cloud Platform

Deploying Citrix XenApp & XenDesktop Service on Google Cloud Platform
Manage Risk by Protecting the Apps and Data That Drive Business Productivity

Manage Risk by Protecting the Apps and Data That Drive Business Productivity
How do Organizations Plan to Assure Application Delivery in a Multi-Cloud World?

How do Organizations Plan to Assure Application Delivery in a Multi-Cloud World?
Workforce Flexibility Can Drive Greater Engagement & Productivity

Workforce Flexibility Can Drive Greater Engagement & Productivity
Citrix Cloud Services: Total Economic Benefits Assessment Guide

Citrix Cloud Services: Total Economic Benefits Assessment Guide
Citrix Cloud Services: Total Economic Benefits Assessment Guide

Citrix Cloud Services: Total Economic Benefits Assessment Guide
Citrix Synergy 2017: Technology Keynote Sketch Notes

Citrix Synergy 2017: Technology Keynote Sketch Notes
Citrix Synergy 2017: Malcolm Gladwell Innovation Super Session Sketch Notes

Citrix Synergy 2017: Malcolm Gladwell Innovation Super Session Sketch Notes
Synergy 2017: Colin Powell Innovation Super Session Sketch Notes

Synergy 2017: Colin Powell Innovation Super Session Sketch Notes
Enterprise Case Study: Enabling a More Mobile Way of Working 

Enterprise Case Study: Enabling a More Mobile Way of Working
Comparing traditional workspaces to digital workspaces

Comparing traditional workspaces to digital workspaces
Último
Último (20)
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
WSO2's API Vision: Unifying Control, Empowering Developers

WSO2's API Vision: Unifying Control, Empowering Developers
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
The High Stakes of Business Security [Infographic]
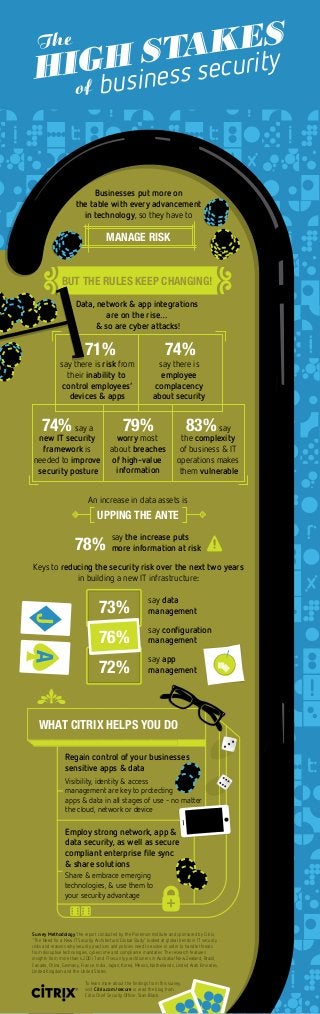
- 1. Businesses put more on the table with every advancement in technology, so they have to MANAGE RISK Regain control of your businesses sensitive apps & data Visibility, identity & access management are key to protecting apps & data in all stages of use – no matter the cloud, network or device Share & embrace emerging technologies, & use them to your security advantage Survey Methodology The report conducted by the Ponemon Institute and sponsored by Citrix, “The Need for a New IT Security Architecture: Global Study” looked at global trends in IT security risks and reasons why security practices and policies need to evolve in order to handle threats from disruptive technologies, cybercrime and compliance mandates. The research features insights from more than 4,200 IT and IT security practitioners in Australia/New Zealand, Brazil, Canada, China, Germany, France, India, Japan, Korea, Mexico, Netherlands, United Arab Emirates, United Kingdom and the United States. To learn more about the findings from this survey, visit Citrix.com/secure or read the blog from Citrix Chief Security Officer, Stan Black. 83% say the complexity of business & IT operations makes them vulnerable 79% worry most about breaches of high-value information 74% say a new IT security framework is needed to improve security posture 71% say there is risk from their inability to control employees’ devices & apps 74% say there is employee complacency about security BUT THE RULES KEEP CHANGING! Data, network & app integrations are on the rise… & so are cyber attacks! Employ strong network, app & data security, as well as secure compliant enterprise file sync & share solutions An increase in data assets is UPPING THE ANTE WHAT CITRIX HELPS YOU DO Keys to reducing the security risk over the next two years in building a new IT infrastructure: 72% 73% say data management AJ 76% say app management say configuration management 78% say the increase puts more information at risk The HIGH STAKES business security of
