Sorting searching
•Descargar como PPT, PDF•
0 recomendaciones•751 vistas
Denunciar
Compartir
Denunciar
Compartir
Recomendados
Recomendados
Más contenido relacionado
Destacado
Destacado (20)
The Loss of Intellectual Property in the Digital Age: What Companies can d…

The Loss of Intellectual Property in the Digital Age: What Companies can d…
Identifing And Controlling Intellectual Property Loss Exposures

Identifing And Controlling Intellectual Property Loss Exposures
Trends that will influence the future of knowledge work

Trends that will influence the future of knowledge work
Similar a Sorting searching
Similar a Sorting searching (20)
Building a Large Scale SEO/SEM Application with Apache Solr: Presented by Rah...

Building a Large Scale SEO/SEM Application with Apache Solr: Presented by Rah...
CS2: A Searchable Cryptographic Cloud Storage System

CS2: A Searchable Cryptographic Cloud Storage System
Internet-scale Real-time Code Clone Search via Multi-level Indexing

Internet-scale Real-time Code Clone Search via Multi-level Indexing
Good practices (and challenges) for reproducibility

Good practices (and challenges) for reproducibility
Geek Sync | Guide to Understanding and Monitoring Tempdb

Geek Sync | Guide to Understanding and Monitoring Tempdb
PostgreSQL worst practices, version PGConf.US 2017 by Ilya Kosmodemiansky

PostgreSQL worst practices, version PGConf.US 2017 by Ilya Kosmodemiansky
Más de ForwardBlog Enewzletter
Más de ForwardBlog Enewzletter (7)
Último
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Último (20)
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Sorting searching
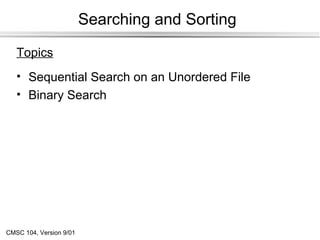
- 1. Searching and Sorting Topics • Sequential Search on an Unordered File • Binary Search CMSC 104, Version 9/01
- 2. Common Problems • There are some very common problems that we use computers to solve: o Searching through a lot of records for a specific record or set of records o Placing records in order, which we call sorting • There are numerous algorithms to perform searches and sorts. We will briefly explore a few common ones. CMSC 104, Version 9/01
- 3. Searching • A question you should always ask when selecting a search algorithm is “How fast does the search have to be?” The reason is that, in general, the faster the algorithm is, the more complex it is. • Bottom line: you don’t always need to use or should use the fastest algorithm. • Let’s explore the following search algorithms, keeping speed in mind. o Sequential (linear) search o Binary search CMSC 104, Version 9/01
- 4. Sequential Search on an Unordered File • Basic algorithm: Get the search criterion (key) Get the first record from the file While ( (record != key) and (still more records) ) Get the next record End_while • When do we know that there wasn’t a record in the file that matched the key? CMSC 104, Version 9/01
- 5. Binary Search • If we have an ordered list and we know how many things are in the list (i.e., number of records in a file), we can use a different strategy. • The binary search gets its name because the algorithm continually divides the list into two parts. CMSC 104, Version 9/01
- 6. How a Binary Search Works Always look at the center value. Each time you get to discard half of the remaining list. Is this fast ? CMSC 104, Version 9/01
- 7. How Fast is a Binary Search? • Worst case: 11 items in the list took 4 tries • How about the worst case for a list with 32 items ? o 1st try - list has 16 items o 2nd try - list has 8 items o 3rd try - list has 4 items o 4th try - list has 2 items o 5th try - list has 1 item CMSC 104, Version 9/01
- 8. How Fast is a Binary Search? (con’t) List has 250 items List has 512 items 1st try - 125 items 1st try - 256 items 2nd try - 63 items 2nd try - 128 items 3rd try - 32 items 3rd try - 64 items 4th try - 16 items 4th try - 32 items 5th try - 8 items 5th try - 16 items 6th try - 4 items 6th try - 8 items 7th try - 2 items 7th try - 4 items 8th try - 1 item 8th try - 2 items 9th try - 1 item CMSC 104, Version 9/01
- 9. What’s the Pattern? • List of 11 took 4 tries • List of 32 took 5 tries • List of 250 took 8 tries • List of 512 took 9 tries • 32 = 25 and 512 = 29 • 8 < 11 < 16 23 < 11 < 24 • 128 < 250 < 256 27 < 250 < 28 CMSC 104, Version 9/01
- 10. A Very Fast Algorithm! • How long (worst case) will it take to find an item in a list 30,000 items long? 210 = 1024 213 = 8192 211 = 2048 214 = 16384 212 = 4096 215 = 32768 • So, it will take only 15 tries! CMSC 104, Version 9/01 1
- 11. Lg n Efficiency • We say that the binary search algorithm runs in log2 n time. (Also written as lg n) • Lg n means the log to the base 2 of some value of n. • 8 = 23 lg 8 = 3 16 = 24 lg 16 = 4 • There are no algorithms that run faster than lg n time. CMSC 104, Version 9/01 1