Module 1 computer networks imtroduction,data link layer
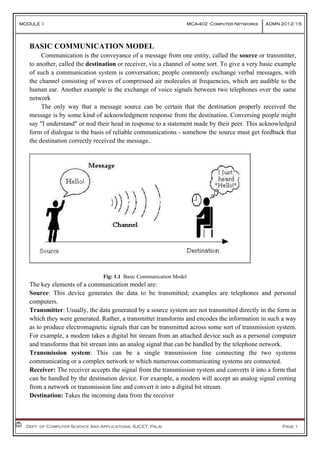
- 1. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 1 BASIC COMMUNICATION MODEL Communication is the conveyance of a message from one entity, called the source or transmitter, to another, called the destination or receiver, via a channel of some sort. To give a very basic example of such a communication system is conversation; people commonly exchange verbal messages, with the channel consisting of waves of compressed air molecules at frequencies, which are audible to the human ear. Another example is the exchange of voice signals between two telephones over the same network The only way that a message source can be certain that the destination properly received the message is by some kind of acknowledgment response from the destination. Conversing people might say "I understand" or nod their head in response to a statement made by their peer. This acknowledged form of dialogue is the basis of reliable communications - somehow the source must get feedback that the destination correctly received the message. Fig: 1.1 Basic Communication Model The key elements of a communication model are: Source: This device generates the data to be transmitted; examples are telephones and personal computers. Transmitter: Usually, the data generated by a source system are not transmitted directly in the form in which they were generated. Rather, a transmitter transforms and encodes the information in such a way as to produce electromagnetic signals that can be transmitted across some sort of transmission system. For example, a modem takes a digital bit stream from an attached device such as a personal computer and transforms that bit stream into an analog signal that can be handled by the telephone network. Transmission system: This can be a single transmission line connecting the two systems communicating or a complex network to which numerous communicating systems are connected. Receiver: The receiver accepts the signal from the transmission system and converts it into a form that can be handled by the destination device. For example, a modem will accept an analog signal coming from a network or transmission line and convert it into a digital bit stream. Destination: Takes the incoming data from the receiver
- 2. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 2 Fig: 1.2Simple Data Communication Model COMMUNICATIONS MODEL TASKS Some of the Key tasks to be performed by a Communications System are listed below: • Transmission System Utilization • Interfacing • Signal Generation • Synchronization • Exchange Management • Error detection and correction • Addressing and routing • Recovery • Message formatting • Security Transmission System Utilization: refers to the need to make efficient use of transmission facilities that are typically shared among a number of communicating devices. Various techniques (referred to as multiplexing) are used to allocate the total capacity of a transmission medium among a number of users. Interface: - A device must interface with the transmission system in order to communicate. Signal Generation: All the data that are transmitted over the transmitting system propagate as Electromagnetic signals. Hence the communicating device must be able to generate and receive these signals. Signal generation should be such that the resultant signal is capable of being propagated through the transmission medium and interpretable as data at the receiver. Synchronization: Unless the receiver and transmitter are in Synchronization the receiver will not be able to make sense out of received signals. Receiver should know when the transmission of data starts, when it ends.
- 3. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 3 Exchange Management: For meaningful data transaction there should be some kind management of data being exchanged. Both the transmitter and receiver should adhere to some common convention about the format of data, amount of data that can be sent at a time and so on. This requires a prior definition of message formatting. Error Detection and Correction: In any communication system transmitted data is prone to error. Either it is because of transmitted signal getting distorted in the transmission medium leading to misinterpretation of signal or errors introduced by the intermediate devices. Error detection and Correction is required in cases where there is no scope for error in the data transaction. We can think of file transfer between two computers where there is a need for this. But in some cases it may not be very important as in the case of telephonic conversation. Addressing And Routing: When more than two devices share a transmission facility, a source system must indicate the identity (or address) of the intended destination. The transmission system must assure that the destination system, and only that system, receives the data. Further, the transmission system may itself be a network through which various paths may be taken. A specific route through this network must be chosen. Recovery is a concept distinct from that of error correction. Recovery techniques are needed in situations in which an information exchange, such as a database transaction or file transfer, is interrupted due to a fault somewhere in the system. The objective is either to be able to resume activity at the point of interruption or at least to restore the state of the systems involved to the condition prior to the beginning of the exchange Message Formatting has to do with an agreement between two parties as to the form of the data to be exchanged or transmitted, such as the binary code for characters. Security: It is important to provide some measure of security in a data communications system. The sender of data may wish to be assured that only the intended receiver actually receives the data and the receiver of data may wish to be assured that the received data have not been altered in transit and that the data actually come from the purported sender Network Management: Data communications facility is a complex system that cannot create or run itself. Network management capabilities are needed to configure the system, monitor its status, react to failures and overloads, and plan intelligently for future growth. DATA COMMUNICATION MODEL Data Communication is a process of exchanging data or information between two devices via some form of transmission medium such as a wire cable. The word data refers to any information which is presented in a form that is agreed and accepted upon by its creators and users. For data communication to occur, the communicating devices should be part of a communication system made up of a combination of hardware and software. The hardware part involves the sender and receiver devices and the intermediate devices through which the data passes. The software part involves certain rules which specify what is to be communicated, how it is to be communicated and when. It is also called as a Protocol. The effectiveness of any data communications system depends upon the following four fundamental characteristics: Delivery: The data should be delivered to the correct destination and correct user. Accuracy: The communication system should deliver the data accurately, without introducing any errors. The data may get corrupted during transmission affecting the accuracy of the delivered data.
- 4. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 4 Timeliness: Audio and Video data has to be delivered in a timely manner without any delay; such a data delivery is called real time transmission of data. Jitter: It is the variation in the packet arrival time. Uneven Jitter may affect the timeliness of data being transmitted. There may be different forms in which data may be represented. Some of the forms of data used in communications are as follows: Text: Text includes combination of alphabets in small case as well as upper case. It is stored as a pattern of bits. Prevalent encoding system : ASCII, Unicode Numbers: Numbers include combination of digits from 0 to 9. It is stored as a pattern of bits. Prevalent encoding system : ASCII, Unicode Images: In computers images are digitally stored. A Pixel is the smallest element of an image. To put it in simple terms, a picture or image is a matrix of pixel elements. The pixels are represented in the form of bits. Depending upon the type of image (black n white or color) each pixel would require different number of bits to represent the value of a pixel. The size of an image depends upon the number of pixels (also called resolution) and the bit pattern used to indicate the value of each pixel. Audio: Data can also be in the form of sound which can be recorded and broadcasted. Example: What we hear on the radio is data or information. Audio data is continuous, not discrete. Video: Video refers to broadcasting of data in form of picture or movie DATA COMMUNICATION NETWORK A communication network, in its simplest form, is a set of equipment and facilities that provides a communication service: the transfer of information between users located at various geographical points. Examples of such networks include telephone networks, computer networks, television broadcast networks, cellular telephone networks, and the Internet. The ability of communication network to transfer information at extremely high speeds allows users to gather information in large volumes, nearly instantaneously and, with the aid of computers, to almost immediately exercise action at a distance. These two unique capabilities form the basis for many existing services and an unlimited number of future network-based services In its simplest form, data communication takes place between two devices that are directly connected by some form of point-to-point transmission medium. Often, however, it is impractical for two devices to be directly, point-to-point connected. This is so for one (or both) of the following contingencies: • The devices are very far apart. It would be inordinately expensive, for example, to string a dedicated link between two devices thousands of miles apart. • There is a set of devices, each of which may require a link to many of the others at various times. Examples are all of the telephones in the world and all of the terminals and computers owned by single organization. Except for the case of a very few devices, it is impractical to provide a dedicated wire between each pair of devices. The solution to this problem is to attach each device to a communications network like Wide Area Network (WAN) or Local Area Network (LAN).
- 5. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 5 Fig. 1.3 Simplified Network model COMPUTER NETWORKS A computer network is simply a collection of computers or other hardware devices that are connected together, either physically or logically, using special hardware and software, to allow them to exchange and share information. Networking is the term that describes the processes involved in designing, implementing, upgrading, managing and otherwise working with networks and network technologies. Three criteria necessary for an effective and efficient network are: Performance: Performance of the network depends on number of users, type of transmission medium, and the capabilities of the connected h/w and the efficiency of the s/w. Reliability: Reliability is measured by frequency of failure, the time it takes a link to recover from the failure and the network’s robustness in a catastrophe. Security: Network security issues include protecting data from unauthorized access, protecting data from damage and development, and implementing policies and procedures for recovery from breaches and data losses. APPLICATIONS 1. Resource Sharing(Hardware & Software) 2. Information Sharing Easy accessibility from anywhere (files, databases) Search Capability (WWW) 3. Communication Email
- 6. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 6 Message broadcast 4. Remote computing 5. Distributed processing (GRID Computing) CLASSIFICATION OF NETWORKS Computers connected to a network are broadly categorized as servers or workstations. Servers are generally not used by humans directly, but rather run continuously to provide "services" to the other computers (and their human users) on the network. Services provided can include printing and faxing, software hosting, file storage and sharing, messaging, data storage and retrieval, complete access control (security) for the network's resources, and many others. Workstations are called such because they typically do have a human user which interacts with the network through them. Workstations were traditionally considered a desktop, consisting of a computer, keyboard, display, and mouse, or a laptop, with integrated keyboard, display, and touchpad. Every computer on a network should be appropriately configured for its use. Classification criteria’s are given below. 1. By Size or Scale 2. By Structure / Functional Relationship 3. By Topology / Physical Connectivity Depending upon the size or scale network is divided as Personal Area Networks(PAN) Local Area Networks(LAN) Wide Area Networks(WAN) Metropolitan Area Networks(MAN) Internetworks PERSONAL AREA NETWORK (PAN) Very small scale network Range is less than 2 meters Cell phones, PDAs, MP3 players LOCAL AREA NETWORK (LAN) Contains printers, servers and computers Systems are close to each other Contained in one office or building Organizations often have several LANS The most common use of LANs is for linking personal computers within a building or office to share information and expensive peripheral devices such as laser printers. Most local area networks are built with relatively inexpensive hardware such as Ethernet cables, network adapters, and hubs. The defining characteristics of LANs, in contrast to WANs (wide area networks), include their higher data transfer rates, smaller geographic range, and lack of a need for leased telecommunication lines METROPOLITAN AREA NETWORK Large network that connects different organizations Shares regional resources Ex:Cable television network The term Metropolitan Area Network (MAN) is typically used to describe a network that spans a citywide area or a town. It is confined to a larger area than a LAN and can range from 10km to a few
- 7. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 7 100km in length. MANs are larger than traditional LANs and predominantly use high-speed media, such as fiber optic cable, for their backbones. MANs are common in organizations that need to connect several smaller facilities together for information sharing. This is often the case for hospitals that need to connect treatment facilities, outpatient facilities, doctor's offices, labs, and research offices for access to centralized patient and treatment information WIDE AREA NETWORK Two or more LANs connected over a large geographic area Typically use public or leased lines(Phone lines,)Satellite The Internet is a WAN WAN can range from 100krn to 1000krn and the speed between cities can vary from l.5 Mbps to 2.4 Gbps. typically, a WAN consists of two or more local-area networks (LANs) or MANs. They can connect networks across cities, states or even countries. Computers connected to a wide-area network are often connected through public networks, such as the telephone system. They can also be connected through leased lines or satellites. Typically, a WAN consists of a number of interconnected switching nodes. Transmission from any one device is routed through these internal nodes to the specified destination device. These nodes (including the boundary nodes to which the devices are connected) are not concerned with the content of the data; rather, their purpose is to provide a switching facility that will move the data from node to node until they reach their destination. Traditionally, WANs have been implemented using one of two technologies: circuit switching and packet switching. More recently, frame relay and ATM networks have assumed major roles. THE INTERNET A collection of interconnected networks. global computer network Internet is evolved from the ARPANET, which was developed in 1969 by the Advanced Research Projects Agency (ARPA) of the U.S. Department of Defense. It was the first operational packet-switching network whose main aim was to connect stand-alone research computers. It was the first operational packet-switching network whose main aim was to connect stand-alone research computers. The Internet is an example of a network that connects many WANs, MANs, and LANs into the world's largest global network. Internet Service Providers (ISPs) are responsible for maintaining the integrity of the Internet while providing connectivity between WANs, MANs, and LANs throughout the world. ISPs provide customers with access to the Internet through the use of points-of-presence (POP), also called network access points (NAP), in cities throughout the world. Customers are provisioned access to POPs from their own WANs, MANs, and LANs to Internet access to their users. By Structure / Functional Relationship, LAN is divided as Client / Server Peer to Peer (P2PN) Client/Server network Nodes and servers share data Nodes are called clients Servers are used to control access Server is the most important computer
- 8. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 8 Fig. 1.4 Client/Server Peer to peer networks (P2PN) All nodes are equal Nodes access resources on other nodes Each node controls its own resources Most modern OS allow P2PN Distributed computing is a form By Topology / Physical Connectivity LAN is divided as BUS STAR RING MESH TREE BUS Also called linear bus One wire connects all nodes Advantages Easy to setup Small amount of wire Disadvantages Slow Easy to crash Fig. 1.4 Bus Topology
- 9. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 9 STAR Most common topology All nodes connect to a hub Packets sent to hub Hub sends packet to destination Advantages Easy to setup One cable cannot crash network Disadvantages One hub crashing downs entire network Uses lots of cable Fig. 1.6 Star Topology RING Nodes connected in a circle Tokens used to transmit data Nodes must wait for token to send Advantages No data collisions Disadvantages Slow Lots of cable Single ring – All the devices on the network share a single cable. Dual ring – The dual ring topology allows data to be sent in both directions. Fig 1.7 Single Ring Fig 1.8 Dual Ring
- 10. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 10 MESH • All computers connected together • Internet is a mesh network • Advantage - Data will always be delivered - Disadvantages - Lots of cable - Hard to setup Fig 1.9 Mesh Network TREE Hierarchal Model extended star topology Advantages Scalable Easy Implementation Easy Troubleshooting Fig. 1.10 Tree Network PROTOCOLS In computer networks, communication occurs between entities in different systems. An entity is anything capable of sending or receiving information. However, two entities cannot simply send bit streams to each other and expect to be understood. For communication to occur, the entities must agree on a protocol. A protocol is a set of rules that govern data communications. A protocol defines what is
- 11. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 11 communicated, how it is communicated, and when it is communicated. The key elements of a protocol are syntax, semantics, and timing. Syntax:The term syntax refers to the structure or format of the data, meaning the order in which they are presented. For example, a simple protocol might expect the first 8 bits of data to be the address of the sender, the second 8 bits to be the address of the receiver, and the rest of the stream to be the message itself. Semantics: The word semantics refers to the meaning of each section of bits. How is a particular pattern to be interpreted, and what action is to be taken based on that interpretation? For example, does an address identify the route to be taken or the final destination of the message? Timing: The term timing refers to two characteristics: when data should be sent and how fast they can be sent. For example, if a sender produces data at 100 Mbps but the receiver can process data at only 1 Mbps, the transmission will overload the receiver and some data will be lost. Principles of Protocol Architecture Layered structure Protocol stack Each layer provides services to upper layer; expect services from lower one Layer interfaces should be well-defined Peer entities communicate using their own protocol peer-to-peer protocols independent of protocols at other layers if one protocol changes, other protocols should not get affected Data are not directly transferred from layer-n on one computer to layer-n on another computer. Rather, each layer passes data and control information to the layer directly below until the lowest layer is reached. Below layer-1 (the bottom layer), is the physical medium (the hardware) through which the actual transaction takes place. Logical communication is shown by a broken-line arrow and physical communication by a solid-line arrow.Between every pair of adjacent layers is an interface. The interface is a specification that determines how the data should be passed between the layers. ]t defines what primitive operations and services the lower layer should offer to the upper layer. One of the most important considerations when designing a network is to design clean-cut interfaces between the layers. To create such an interface between the layers would require each layer to perform a specific collection of well understood functions. A clean-cut interface makes it easier to replace the implementation of one layer with another implementation because all that is required of the new implementation is that, it offers, exactly the same set of services to its neighboring layer above as the old implementation did. Protocol architecture is the layered structure of hardware and software that supports the exchange of data between systems. At each layer of protocol architecture, one or more common protocols are implemented in communicating systems. Each protocol provides a set of rules for the exchange of data between systems. It acts as a blue print that guides the design and implementation of networks and there by enables to divide the workload and to simplify the systems design. The specification of architecture must contain enough information to allow an implementer to write the program or build the hardware for each layer so that it will correctly obey the appropriate protocol. Neither the details of the implementation nor the specification of the interfaces is part of the architecture because these are hidden away inside the machines and not visible from the outside. THE OSI REFERENCE MODEL
- 12. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 12 This model is based on a proposal developed by the International Standards Organization (ISO) as a first step toward international standardization of the protocols used in the various layers. It was revised in 1995. The Open Systems Interconnection (OS1) reference model describes how information from a software application in one computer moves through a network medium to a software application in another computer. The OSI reference model is a conceptual model composed of seven layers each specifying particular network functions and into these layers are fitted the protocol standards developed by the ISO and other standards bodies. provides a general framework for standardization defines a set of layers with specific services one or more protocols can be developed for each layer The OSI model divides the tasks involved with moving information between networked computers into seven smaller, more manageable task groups. A task or group of tasks is then assigned to each of the seven OSI layers. Each layer is reasonably self-contained so that the tasks assigned to each layer can be implemented independently. This enables the solutions offered by one layer to be updated without affecting the other layers. The seven layers of OSI model are: • Application • Presentation • Session • Transport • Network • Data link • Physical Although, each layer of the OSI model provides its own set of functions, it is possible to group the layers into two distinct categories. The first four layers i.e., physical, data link, network, and transport layer provide the end-to-end services necessary for the transfer of data between two systems. These layers specify the protocols associated with the communications network used to link two computers together. Together, these are communication oriented. The top three layers i.e., the application, presentation, and session layers provide the application services required for the exchange of information. A message begins at the top application layer and moves down the OSI layers to the bottom physical layer. As the message descends, each successive OSI model layer adds a header to it. A header is layer-specific information that basically explains what functions the layer carried out. When formatted data passes through physical layer it is transformed into appropriate signals and transmitted. Upon reaching destination signal is transformed back into digital format. Data then moves up back through the layers and at each layer the headers and trailers are stripped off and the actions appropriate to that layer are taken. When data reaches top layer it is in a form appropriate to application and is made available to the recipient. On every sending device, each layer calls upon the service offered by the layer below it. On every receiving device, each layer calls upon the service offered by the layer above it.
- 13. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 13 Fig. 1.11 ISO/OSI Reference Model Physical Layer Purpose Deals with the representation ,transmission and synchronization of bits Translation of bits into signals Define data rate and transmission mode Define the interface to the card Electrical Mechanical Functional Example: Pin count on the connector The physical layer is also concerned with the following: Representation of bits: The physical layer is concerned with transmission of signals from one device to another which involves converting data (1‘s & 0‘s) into signals and vice versa. It is not concerned with the meaning or interpretation of bits. Data rate: The physical layer defines the data transmission rate i.e. number of bits sent per second. It is the responsibility of the physical layer to maintain the defined data rate. Synchronization of bits: To interpret correct and accurate data the sender and receiver have to maintain the same bit rate and also have synchronized clocks. Physical topology: The physical layer defines the type of topology in which the device is connected to the network. In a mesh topology it uses a multipoint connection and other topologies it uses a point to point connection to send data. Transmission mode: The physical layer defines the direction of data transfer between the sender and receiver. Two devices can transfer the data in simplex, half duplex or full duplex mode On the sender side, the physical layer receives the data from Data Link Layer and encodes it into signals to be transmitted onto the medium. On the receiver side, the physical layer receives the signals from the transmission medium decodes it back into data and sends it to the Data Link Layer
- 14. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 14 Fig. 1.12 Physical layer in ISO/OSI Data Link Layer The data link layer is concerned with the reliable transfer of data over the communication channel provided by the physical layer. To do this, the data link layer breaks the data into data frames, transmits the frames sequentially over the channel, and checks for transmission errors by requiring the receiving end to send back acknowledgment frames. Responsibilities of the data link layer include the following: Framing: On the sender side, the Data Link layer receives the data from Network Layer and divides the stream of bits into fixed size manageable units called as Frames and sends it to the physical layer. On the receiver side, the data link layer receives the stream of bits from the physical layer and regroups them into frames and sends them to the Network layer. Physical addressing: The Data link layer appends the physical address in the header of the frame before sending it to physical layer. The physical address contains the address of the sender and receiver. In case the receiver happens to be on the same physical network as the sender; the receiver is at only one hop from the sender and the receiver address contains the receiver‘s physical address. In case the receiver is not directly connected to the sender, the physical address is the address of the next node where the data is supposed to be delivered. Flow control: The data link layer makes sure that the sender sends the data at a speed at which the receiver can receive it else if there is an overflow at the receiver side the data will be lost. The data link layer imposes flow control mechanism over the sender and receiver to avoid overwhelming of the receiver. Error control: The data link layer imposes error control mechanism to identify lost or damaged frames, duplicate frames and then retransmit them. This is achieved by specifying error control information is present in the trailer of a frame. Fig. 1.13 Data Link Layer In ISO/OSI
- 15. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 15 Subdivided into two 1. MAC (Media Access Control) Gives data to the NIC Controls access to the media through :CSMA/CD and Token passing 2. LLC (Logical Link Layer) Manages the data link interface or Service Access Points (SAPs)) Can detect some transmission errors using a CRC Network Layer The network layer is concerned with the routing of data across the network from one end to another. To do this, the network layer converts the data into packets and ensures that the packets are delivered to their final destination, where they can be converted back into the original data. In order to route the data through multiple networks, network layer relies on two things: Logical Addressing & Routing Logical addressing: The network layer uses logical address commonly known as IP address to recognize devices on the network. The header appended by the network layer contains the actual sender and receiver IP address. The network layer of intermediate nodes checks for a match of IP address in the header. If no match is found the packet passes to the data link layer and it is forwarded to next node Routing: The network layer divides data into units called packets of equal size and bears a sequence number for rearranging on the receiving end. Each packet is independent of the other and may travel using different routes to reach the receiver hence may arrive out of turn at the receiver. Hence every intermediate node which encounters a packet tries to compute the best possible path for the packet. The best possible path may depend on several factors such as congestion, number of hops, etc. This process of finding the best path is called as Routing. It is done using routing algorithms. Fig. 1.14 Network Layer in ISO/OSI Transport Layer The aim of the transport layer is to isolate the upper three layers from the network, so that any changes to the network equipment technology will be confined to the lower three layers. It provides a network independent, reliable message interchange service to the top three application-oriented layers. This layer acts as an interface between the bottom and top three layers. The lower data link layer (layer 2) is only responsible for delivering packets from one node to another, where as the transport layer is responsible for overall end-to-end validity and integrity of the transmission i.e., it ensures that data is successfully sent and received between two computers. A logical address at network layer facilitates the transmission of data from source to destination device. But the source and the destination both may be having multiple processes communicating with each other. To ensure process to process delivery the
- 16. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 16 transport layer makes use of port address (also known as Service Point Address) to identify the data from the sending and receiving process. Fig. 1.15 Transport Layer in ISO/OSI At the sending side, the transport layer receives data from the session layer, divides it into units called segments with a sequence number. These numbers enable the transport layer to reassemble the message correctly upon arriving at the destination. At the receiving side, the transport layer receives packets from the network layer, converts and arranges into proper sequence of segments and sends it to the session layer. Session Layer Purpose Oversee a communication session Establish Maintain Terminate Synchronization between sender and receiver Assignment of time for transmission Start time End time etc. The session layer at the sending side accepts data from the presentation layer adds checkpoints to it called syn bits to allow for fast recovery in the event of a connection failure. The checkpoints or synchronization points is a way of informing the status of the data transfer. At the receiving end the session layer receives data from the transport layer removes the checkpoints inserted previously and passes the data to the presentation layer. Fig 1.16 Session Layer in ISO/OSI
- 17. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 17 Presentation Layer Purpose Formats data for exchange between points of communication Protocol conversion Data translation Encryption Translation: The sending and receiving devices may run on different platforms (hardware, software and operating system). Hence it is important that they understand the messages that are used for communicating. Presentation layer provides a translation service which converts the message into a common format supported by both sender and receiver. Compression: Data compression reduces the number of bits contained in the information and there by ensures faster data transfer. The data compressed at sender has to be decompressed at the receiving end, both performed by the Presentation layer. Encryption: It is the process of transforming the original message to change its meaning before sending it. The reverse process called decryption has to be performed at the receiving end to recover the original message from the encrypted message. The encryption and decryption services which ensures privacy of sensitive data The presentation layer at sending side receives the data from the application layer adds header which contains information related to encryption and compression and sends it to the session layer. At the receiving side, the presentation layer receives data from the session layer decompresses and decrypts the data as required and translates it back as per the encoding scheme used at the receiver. Fig. 1.17 Presentation Layer in ISO/OSI Application Layer Purpose Support for various applications Provides an interface for the end user Provides variety of protocols Ex: mail services ,Remote login, file access and transfer The application layer provides standards for supporting a variety of application-independent services. In other words application layer provides a variety of protocols that are commonly needed by users. One widely used application protocol is HTTP (Hyper Text Transfer Protocol), which is the basis
- 18. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 18 for the World Wide Web. When a browser wants a Web page, it sends the name of the page it wants to the server using HTTP. The server then sends the page back. Some of the functionalities provided by application layer are: File access and transfer: It allows a use to access, download or upload files from/to a remote host. Mail services: It allows the users to use the mail services. Remote login: It allows logging into a host which is remote World Wide Web (WWW): Accessing the Web pages is also a part of this layer Advantages Each layer performs a set of communication functions Each layer relies on the next lower layer to perform more primitive functions Each layer provides services to the next higher layer Changes in one layer should not require changes in other layers. Layers are entirely independent and transparent to other layers TCP/IP REFERENCE MODEL Most widely used interoperable network protocol architecture Funded by the US Defense Advanced Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the Internet and WWW Layers of TCP/IP. 1. Application Layer 2. Host to host 3. Internet Layer 4. Network Access Layer TCP/IP Reference Model is named from two of the most important protocols in it The Transmission Control Protocol (TCP) and the Internet Protocol (IP).TCP handles reliable delivery for messages of arbitrary size, and defines a robust delivery mechanism for all kinds of data across a network and IP manages the routing of network transmissions from sender to receiver, along with issues related to network and computer addresses.Some of TCP/IP Ref Model goals are: To support multiple, packet-switched pathways through the network so that transmissions can survive all conceivable failures To permit dissimilar computer systems to easily exchange data To offer robust, reliable delivery services for both short- and long-distance communications The TCP/IP model follows a layered architecture very similar to the OSI reference model. Based on the protocol standards that have been developed, we can organize the communication task for TCP/IP into four relatively independent layers: Application layer Transport layer Internet layer Network access layer
- 19. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 19 Fig. 1.18 TCP/IP Layers Network Access Layer • Exchange of data between end system and the network • Formatting the data into a unit called frame and convert that frame into electric or analog pulses. • Responsible to deliver frames reliably from hop to hop (hop could be device such as bridges or switches) • Guarantee Error Free Delivery of Data from one hop to the other • Acknowledging receipt of data frames and resending frames if ack is not received • Core protocols: Ethernet, Token-Ring Internet Layer • Packaging • Addressing • Routing • deals with end-to-end transmission • Implemented in end systems and routers as the Internet Protocol (IP) • Guarantee Error Free Delivery of Packets from one N/W to the other N/W • Core protocols: IP(Internet Protocol),ICMP(Internet Control Message Protocol),ARP(Address Resolution Protocol) Transport Layer • Guarantee Error Free Delivery of Message from source-host to the destination-host (End-to-End reliability) • Offers connection oriented and connection less services • Reliability includes: Error detection and correction, flow control, packet duplication etc… • Runs only on host not on the network Core Protocols 1. TCP(Transmission Control Protocol) 2. UDP(User Datagram Protocol)
- 20. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 20 Application Layer • Provide interface between end-user & applications • Support several users applications The most widely known Application Layer protocols are those used for the exchange of user information, some of them are: The HyperText Transfer Protocol (HTTP) is used to transfer files that make up the Web pages of the World Wide Web. The File Transfer Protocol (FTP) is used for interactive file transfer. The Simple Mail Transfer Protocol (SMTP) is used for the transfer of mail messages and attachments. Telnet, is a terminal emulation protocol, and, is used for remote login to network hosts. The process by which a TCP/IP host sends data can be viewed as a five-step process: Step 1 Create and encapsulate the application data with any required application layer headers. Step 2 Encapsulate the data supplied by the application layer inside a transport layer header. For end- user applications, a TCP or UDP header is typically used. Step 3 Encapsulate the data supplied by the transport layer inside an Internet layer (IP) header. IP defines the IP addresses that uniquely identify each computer. Step 4 Encapsulate the data supplied by the Internet layer inside a data link layer header and trailer. This is the only layer that uses both a header and a trailer. The physical layer encodes a signal onto the medium to transmit the frame. COMPARISON OF THE OSI AND TCP/IP REF. MODELS OSI 1) It has 7 layers 2) Separate presentation layer 3) Separate session layer 4) Network layer provides both Connectionless and connection Oriented services. 5) It defines the services, interfaces and protocols very clearly and makes a clear distinction between them 6) The protocol are better hidden and can be 6) it is not easy to replace the protocols easily replaced as the technology changes TCP/IP 1) Has 4 layers 2) No presentation layer, characteristics are provided by application layer 3) No session layer, characteristics are provided by transport layer 4) Network layer provides only connection less services. 5) It does not clearly distinguishes between service, interface and protocols.
- 21. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 21 7) OSI truly is a general model 7) TCP/IP cannot be used for any other apltn Fig. 1.19 TCP/IP Vs ISO/OSI A CRITIQUE OF THE OSI MODEL AND PROTOCOLS OSI Bad timing, by the time the OSI protocols appeared, the competition TCP/IP protocols were already in widespread use. Bad technology, both the model and the protocols are imperfect and very complex. Bad implementation, (poor quality) Bad politics, it was thought to be the creature of the government. TCP/IP The model does not clearly distinguish the concepts of services, interface, and protocol. It is not at all general and is poorly suited to describing any protocol stack other than TCP/IP. The host-to-network layer is not really a layer. The model does not distinguished the physical and data link layers NOVEL NETWARE Novell introduced its multiprocessing network operating system named NetWare Netware versions 1. Version 3 – popular but older User logs onto a particular server and maintains directory system 2. Version 4 allows single network login and Directory system replaced by powerful NDS database 3. Version 5
- 22. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 22 Allows to use IP protocol instead of Novell’s proprietary IPX/SPX protocols 4. Version 6 Remote manager, Native File Access , iFolder and iPrint 5. Version 6.5 Novell Networks are based on the client/server model in which at least one computer functions as a network file server, which runs all of the NetWare protocols and maintains the networks shared data on one or more disk drives. File servers generally allow users on other PC’s to access application software or data files i.e., it provides services to other network computers called clients. Novel NetWare protocol suite Novell provides a suite of protocols developed specifically for NetWare. Fig. 1.20 Novell protocol suite is illustrated here in relation to the OSI model The five main protocols used by NetWare are: Media Access Protocol. Internetwork Packet Exchange/Sequenced Packet Exchange (IPX/SPX). Routing Information Protocol (RIP). Service Advertising Protocol (SAP). NetWare Core Protocol (NCP). Media Access Protocols: The NetWare suite of protocols supports several media-access protocols, including Ethernet/IEEE 802.3, Token Ring/IEEE 802.5, Fiber Distributed Data Interface (FDDI), and Point-to-Point Protocol (PPP) IPX (Internetwork Packet Exchange protocol): Routing and networking protocol at Network layer. When a device to be communicated with is located on a different network, IPX routes the information to the destination through any intermediate networks. It datagram-based, connectionless, unreliable protocol that is equivalent to the IP
- 23. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 23 SPX (Sequenced Packet Exchange protocol): Control protocol at the transport layer (layer 3) for reliable, connection-oriented datagram transmission. SPX is similar to TCP in the TCP/IP suite. Routing Information Protocol (RIP): Facilitate the exchange of routing information on a NetWare network. In RIP, an extra field of data was added to the packet to improve the decision criteria for selecting the fastest route to a destination Service Advertisement Protocol (SAP): It is an IPX protocol through which network resources, such as file servers and print servers, advertise their addresses and the services they provide. Advertisements are sent via SAP every 60 seconds. This SAP packet contains information regarding the servers which provide services. Using these SAP packets, clients on the network are able to obtain the internetwork address of any servers they can access NetWare Core Protocol (NCP): It defines the connection control and service request encoding that make it possible for clients and servers to interact. This is the protocol that provides transport and session services. NetWare security is also provided within this protocol. DATA LINK LAYER Two Types of networks in DLL Broadcast Networks: All stations share a single communication channel Point-to-Point Networks: Pairs of hosts (or routers) are directly connected The main design issues of the data link layer are: 1. Services provided to the Network Layer 2. Framing 3. Flow Control 4. Error Control 1. Provides A Well-Defined Service Interface To The Network Layer. Principal Service Function of the data link layer is to transfer the data from the network layer on the source machine to the network layer on the destination machine. Possible Services Offered to network layer a) Unacknowledged connectionless service. b) Acknowledged connectionless service. c) Acknowledged connection-oriented service. a. Unacknowledged connectionless service. It consists of having the source machine send independent frames to the destination machine without having the destination machine acknowledge them. Example: Ethernet, Voice over IP, etc. b. Acknowledged connectionless service Each frame send by the Data Link layer is acknowledged and the sender knows if a specific frame has been received or lost. Typically the protocol uses a specific time period that if has passed without getting acknowledgment it will re-send the frame. c. Acknowledged Connection Oriented Service Source and Destination establish a connection first. Each frame sent is numbered. It guarantees that each frame is received only once and that all frames are received in the correct order.
- 24. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 24 Examples: Satellite channel communication, 2. Framing Determines how the bits of the physical layer are grouped into frames (framing). frame header, payload and frame trailer. Fig. 1.21 Framing Three popular methods can be used to mark the start and end of each frame: Character count Flag bytes with byte stuffing Starting and ending flags, with bit stuffing Character Count It uses a field in the header to specify the number of bytes in the frame. Once the header information is being received it will be used to determine end of the frame. See figure, Destination may be able to detect that the frame is in error but it does not have a means how to correct it. Fig 1. 22 Character Count without error and with error However, problems may arise due to changes in character count value during transmission. For example, in the second frame if the character counts 5 changes to7, the destination will receive data out of synchronization and hence, it will not be able to identify the start of the next frame.
- 25. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 25 Flag bytes with byte stuffing The sender inserts a special byte (ESC-Escape Character) just before each flag byte in the data. Beginning and ending byte in the frame are called flag byte. The receiver’s link layer removes this special byte before the data are given to the network layer. Fig 1.23(a) Frame delimited by flag bytes (b) Four examples of byte sequences before and after byte stuffing. Bit stuffing Each frame starts with a flag byte “01111110”. Whenever the sender encounters five consecutive 1s in the data, it automatically stuffs a 0 bit into the outgoing bit stream. When the receiver sees five consecutive incoming 1 bits, followed by a 0 bit, it automatically deletes the 0 bit. USB uses bit stuffing. Fig 1.24 Flag Bit stuffing Figure given below shows the examples of bit stuffing Bit stuffing: (a) The original data. (b) The data as they appear on the line. (c) The data as they are stored in the receiver’s memory after destuffing.
- 26. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 26 Fig 1.25 Bit Stuffing 3. Flow Control Flow control will control the rate of frame transmission and ensure the sending entity does not overwhelm the receiving entity It uses some feedback mechanism(acknowledgement) If the frame is accepted /processed by the receiver then only will the sender send the next frame. Flow control ensures that the speed of sending the frame, by the sender, and the speed of processing the received frame by the receiver are compatible. Two methods have been developed to control flow of data across communications links: 1. Stop and Wait 2. Sliding Window Stop and wait a single frame is send at a time. Source transmits a frame. Destination receives the frame, and replies with a small frame called acknowledgement (ACK). Source waits for the ACK before sending the next frame. It will then send the next frame only after the ACK has been received. Sender keeps a copy of the frame until it receives an acknowledgement. Destination can stop the flow by not sending ACK (e.g., if the destination is busy …). Fig 1.26 Stop and wait strategy For identification, both data frames and acknowledgements (ACK) frames are numbered alternatively 0 and 1.
- 27. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 27 Sender has a control variable (S) that holds the number of the recently sent frame. (0 or 1) Receiver has a control variable R that holds the number of the next frame expected (0 or 1). The advantage of stop and- wait is simplicity: Each frame is checked and acknowledged before the next frame is sent. The disadvantage is inefficiency: In stop-and-wait, at any point in time, there is only one frame that is sent and waiting to be acknowledged. Stop-and-wait is slow. Each frame must travel all the way to the receiver and an acknowledgment must travel all the way back before the next frame can be sent. Sliding Window Idea: allow multiple frames to transmit Receiver has a buffer of W frames Transmitter can send up to W frames without receiving ACK So the link is utilized in a more efficient manner Each data frame carries a sequence number for its identification ACK includes the sequence number of the next expected frame by the receiver. All the previous data frames are assumed acknowledged on receipt of an acknowledgement The sender sends the next n frames starting with the last received sequence number that has been transmitted by the receiver (ACK Operation The idea of sliding windows is to keep track of the acknowledgements. In this mechanism we maintain two types of windows (buffer) sending window and receiving window. The sender needs buffer because it needs to keep copies of all the sent frames for which acknowledgments are yet to be received. The receiver may request for the retransmission of a data frame that is received with errors. The receiver needs buffer to store the received data frames temporarily. The frames may be received out of sequence and it must put them in sequence before processing them for retrieval of user data. The size of the s window is at most 2k – 1. Fig 1.27 Sliding window In this mechanism we maintain two types of windows: Sending window and receiving window Sending window Sending window maintains sequence numbers of frames sent out but not acknowledged and frames which are next to be transmitted. At the beginning of a transmission, the sender’s window contains n frames. As frames are sent out, the left boundary of the window moves inward, shrinking the size of the window.
- 28. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 28 Once an ACK arrives, the window expands to allow in a number of new frames equal to the number of frames acknowledged by that ACK. Fig 1.28 Sending Window For example, Let the window size is 7.If frames 0 through 3 have been sent and no acknowledgment has been received, then the sender's window contains three frames -4, 5, 6. Now, if an ACK numbered 3 is received by source, it means three frames (0, 1, 2) have been received by receiver and are undamaged. The sender's window will now expand to include the next three frames .At this point the sender's window will contain six frames (4, 5, 6, 7, 0, 1). Receiving window The receiver window maintains the set of frames permitted to accept. At the beginning of transmission, the receiver window contains n spaces for frames. As new frames come in, the size of the receiver window shrink As each ACK is sent out, the receiving window expands to include as many new placeholders as newly acknowledged frames Fig 1.29 receiving window For example, let the size of receiver's window is 7. It means window contains spaces for 7 frames. With the arrival of the first frame, the receiving window shrinks, moving the boundary from space 0 to 1. Now, window has shrunk by one, so the receiver may accept six more frame before it is required to send an ACK. If frames 0 through 3 have arrived but have not been acknowledged, the window will contain
- 29. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 29 three frame spaces. As receiver sends an ACK, the window of the receiver expands to include as many new placeholders as newly acknowledged frames. The window expands to include a number of new frame spaces equal to the number of the most recently acknowledged frame minus the number of previously acknowledged frame. For e.g., If window size is 7 and if prior ACK was for frame 2 & the current ACK is for frame 5 the window expands by three (5-2). Therefore, the sliding window of sender shrinks from left when frames of data are sending and expands to right when acknowledgments are received. The sliding window of the receiver shrinks from left when frames of data are received and expands to the right when acknowledgement is sent. 4. Error Control An error occurs when a bit is altered between transmission and reception. Error control in the data link layer is based on Automatic Repeat Request (ARQ), which is the retransmission of data. i. Single bit errors One bit is altered Adjacent bits are not affected ii. Burst errors A cluster of bits altered a number of bits in error More common and more difficult to deal lost message (frame) Fig. 1.30 Error Control protocols i. Stop-and-Wait ARQ Keeping a copy of the sent frame and retransmitting of the frame when the timer expires. use sequence numbers to number the frames The source station is equipped with a timer. Source transmits a single frame, and waits for an ACK, If the frame is lost…the source retransmits the frame. If receiver receives a damaged frame, discard it and the source retransmits the frame. If everything goes right, but the ACK is damaged or lost, the source will not recognize it, the source will retransmit the frame, and Receiver gets two copies of the same frame! Solution: use sequence numbers, There are four different scenarios that can happen: Normal Operation When ACK is lost When frame is lost When ACK time out occurs
- 30. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 30 Stop-and-Wait ARQ-Normal Operation Fig. 1.31 Normal Operation Sender is sending frame0 and waits for ACK1 Once it receives ACK1 in time (allotted time) it will send frame1. This process will be continuous till complete data transmission takes place. Stop-and-Wait -lost ACK frame Fig 1.32 Lost ACK Frame If the sender receives a damaged ACK, it discards it. Here, as the time expires for ACK0 it will retransmit frame1 Receiver has already received frame1 and expecting to receive frame0 (R=0). Therefore it discards the second copy of frame1. Thus the numbering mechanism solves the problem of duplicate copy of frames.
- 31. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 31 Stop-and-Wait ARQ- lost frame Fig 1.33 Lost frames If the receiver receives corrupted/damaged frame it will simply discard it and assumes that the frame was lost on the way. the sender will not get ACK The sender will be in waiting stage for ACK till its time out occurs in the system. As soon as time out occurs in the system, the sender will retransmit the same frame and the receiver will send the acknowledgment Stop-and-Wait, delayed ACK frame Fig 1.34 delayed ACK The ACK can be delayed at the receiver or due to some problem It is received after the timer for frame0 has expired.
- 32. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 32 Sender retransmitted a copy of frame0.However, R=1 means receiver expects to see frame1. Receiver discards the duplicate frame0. Sender receives 2 ACKs, it discards the second ACK. ii. Go-Back-N ARQ Based on sliding-window flow control. allowing transmission of more than one frame without waiting for acknowledgement If no error, the destination will send ACK as usual with next frame expected (positive ACK, RR: receive ready) If error, the destination will reply with rejection (negative ACK, REJ: reject) Receiver discards that frame and all future frames, until the erroneous frame is received correctly. Source must go back and retransmit that frame and all succeeding frames that were transmitted. This makes the receiver simple, but decreases the efficiency Fig 1.35 Go-Back N ARQ Damaged Frame Suppose A is sending frames to B. After each transmission, A sets a timer for the frame. In Go-Back-N ARQ, if the receiver detects error in frame i • Receiver discards the frame, and sends REJ-I • Source gets REJ-I • Source retransmits frame i and all subsequent frames Lost Frame 1 Assume receiver has received frame i-1. If frame i is lost. Source subsequently sends i+1 Receiver gets frame i+1 out of order, this means the lost of a frame! Receiver sends REJ-I, Source gets REJ-i, and so goes back to frame i and retransmits frame i, i+1,
- 33. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 33 Lost Frame 2 Assume receiver has received frame i-1 Frame i is lost and no additional frame is sent Receiver gets nothing and returns neither acknowledgement nor rejection Source times out and sends a request to receiver asking for instructions Receiver responses with RR frame, including the number of the next frame it expects, i.e., frame I Source then retransmits frame i Damaged RR Receiver gets frame i and sends RR(i+1) which is lost or damaged Acknowledgements are cumulative, so the next acknowledgement, i.e., RR(i+n) may arrive before the source times out on frame I If source times out, it sends a request to receiver asking for instructions, just like the previous example iii. Selective Repeat ARQ Pros: Only rejected frames are retransmitted Subsequent frames are accepted by the receiver and buffered Minimizes the amount of retransmissions Cons: Receiver must maintain large enough buffer, and must contain logic for reinserting the retransmitted frame in the proper sequence Also more complex logic in the source Retransmission mechanism Timer: When the timer expires, only the corresponding frame is retransmitted. NAK: Whenever an out-of-sequence frame is observed at the receiver, a NAK frame is sent with sequence number Rnext. When the transmission receives such a NAK frame, it retransmits the specific frame, Rnext. Fig 1.36 Selective Repeat
- 34. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 34 Performance More efficient than the other two protocols because it reduces number of retransmissions for noisy links The receiver and transmitter processing logic is more complex Receiver must be able to reinsert the retransmitted (lost, delayed, damaged) frame in the proper sequence after it arrives The sender should be able to send out of order frame when requested by the sender using NAK Needs more memory than Go-Back-N ARQ at the receiver side. ERROR DETECTION Error detecting codes. Include only enough redundancy (which means adding extra bits for detecting errors at the destination) to allow the receiver to deduce that an error has occurred. Fig 1.37 Error detecting codes Three types of redundancy check methods are commonly used in data transmission: Fig 1.38 Error detecting code classification i. Parity Check This is the most common and least expensive mechanism for error detection. A parity bit is added to every data unit so that the total number of 1s(including the parity bit) becomes even for even-parity check or odd for odd-parity check . • Suppose the sender wants to send the word world. In ASCII the five characters are coded as 1110111 1101111 1110010 1101100 1100100 The following shows the actual bits sent
- 35. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 35 11101110 11011110 11100100 11011000 11001001 received by the receiver without being corrupted in transmission. 11101110 11011110 11100100 11011000 11001001 The receiver counts the 1s in each character and comes up with even numbers (6, 6, 4, 4, 4). The data are accepted. Fig 1.39 simple parity check Fig 1.40 Even Parity Checking Scheme
- 36. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 36 ii. Cyclic Redundancy Check (Crc) The Cyclic Redundancy Check is the most powerful and easy to implement error detection technique. Sender • In CRC sender divides frame (data) by using a predetermined Generator Polynomial. • A generating polynomial is an industry approved bit string that is used to create cyclic checksum remainder • The reminder obtained after division is appended to the end of the original message and is transmitted over the medium. Receiver • At the destination, the incoming data unit is divided by the same generating polynomial. • If there is no remainder, the data unit is assumed to be correct and is therefore accepted • A remainder indicates that the data unit has been damaged in transmit and therefore must be rejected. Fig 1.41 CRC • Suppose a m bit message is to be transmitted and we are using a generating polynomial of length n+1 • Multiply the original message by 2n and divide it by generating polynomial • The remainder of this division process generates the n-bit (CRC) remainder which will be appended to the m-bit message producing (m+n) bit frame for transmission • On receiving the packet, the receiver divides the (m+n) bit frame by the same generating polynomial and if it produces no remainder ,no error has occured • Ex:Given Message D = 1010001101 (10 bits) Pattern P = 110101(6 bits) Remainder R =to be calculated(5 bits) Thus m= 10, n+1 = 6,n = 5. The message is multiplied by 25 yielding 101000110100000.
- 37. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 37 This product is divided by P Fig 1.42 CRC Division at sender The remainder is added to D to give T = 101000110101110, which is transmitted. If there are no errors, the receiver receives T intact. The received frame is divided by P and if there is no remainder, it is assumed that there have been no errors. Fig 1.43 CRC Division at receiver
- 38. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 38 iii. Checksum Sender Side The unit is divided into k sections, each of n bits. All sections are added together to get the sum. The sum is complemented and becomes the checksum. The checksum is sent with the data. Receiver Side The unit is divided into k sections, each of n bits. All sections are added together to get the sum. The sum is complemented. If the result is one, the data are accepted: otherwise, they are rejected. Fig 1.44 check sum method HDLC -High-Level Data Link Control It is a bit-oriented protocol developed by ISO where information is send as a sequence of bits. Frames are used as a transport mechanism to transport data from one point to another. features : i. Reliable protocol (selective repeat or go-back-N) ii. Full-duplex communication (receive and transmit at the same time) iii. Bit-oriented protocol iv. Flow control (adjust window size based on receiver capability). v. Uses physical layer clocking and synchronization to send and receive frames Basic Characteristics of HDLC To satisfy a variety of applications, HDLC defines three types of stations, two link configurations, and three data-transfer modes of operation. The three station types are: Primary station Has the responsibility of controlling the operation of data flow . Handles error recovery
- 39. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 39 Frames issued by the primary station are called commands. Secondary station, Operates under the control of the primary station. Frames issued by a secondary station are called responses. The primary station maintains a separate logical link with each secondary station. Combined station, Acts as both as primary and secondary station. The two link configurations are: i. Unbalanced Configuration: Consists of one primary and two or more secondary. ii. Balanced Configuration: Consists of two combined stations and supports both full-duplex and half-duplex transmission Fig 1.45 HDLC Stations with modes The three modes of data transfer operations are Normal Response Mode (NRM) Secondary station can send only when the primary station instruct it to do so Two common configurations Point-to-Point link (one primary and one secondary station) Multipoint link (primary station maintain different sessions with different secondary stations) Asynchronous Response Mode (ARM) More independent secondary station Can send data or control information without explicit permission to do so Asynchronous Balanced Mode (ABM) used in point-to-point links, for communication between combined stations Either stations can send data, control information and commands HDLC Frame StructureHDLC uses synchronous transmission. All transmissions are in the form of frames, and a single frame format suffices for all types of data and control exchanges. Three types of frames are used in HDLC.
- 40. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 40 Fig 1.46 HDLC frames The following depicts the structure of the HDLC frame. The flag, address, and control fields that precede the information field are known as a header. The FCS and flag fields following the data or information field are referred to as a trailer. Fig 1.47 HDLC frame format Flag: bit pattern that shows both the beginning and the end of a frame. Address: contains the address of the secondary station and identifies whether the frame is a command or response Control: Identifies the type of HDLC frame i.e..(I,S or U-frames) Information: present only in I-frames and some U-frames. Frame Check Sequence (FCS): This field contains a 16-bit, or 32-bit CRC bits which is used for error detection Operation Three phases initialization by either side, set mode & information data transfer with flow and error control using both I & S-frames disconnect when ready or fault noted LINK ACCESS PROTOCOL-BALANCED (LAPB) X.25 is a network interface defined for accessing packet-switched public networks. It is commonly used for interconnecting LANs. The X.25 defines the lowest three layers of the OSI Reference Model Physical layer, Data link Layer and Network Layer. LAPB is a bit-oriented synchronous protocol that provides complete data transparency in a full-duplex point-to-point operation. It is a data link layer protocol used to manage communication between data terminal equipment (DTE) and the data circuit-
- 41. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 41 terminating equipment (DCE) devices. Data terminal equipment devices are end systems that communicate across the X.25 network. They are usually terminals, personal computers, or network hosts, and are located on the premises of individual subscribers. DCE devices are communications devices, such as modems and packet switches. Fig 1.48 LAPB frame LAPB has been derived from HDLC and shares the same frame format, frame types, and field functions as HDLC. It differs from HDLC in the representation of address field. The address field can contain only one of two fixed (DTE or DCE) addresses. It supports a peer-to-peer link in that neither end of the link plays the role of the permanent master station. A minimum of overhead is required to ensure flow control, error detection and recovery. If data is flowing in both directions (full duplex), the data frames themselves carry all the information required to ensure data integrity. either of these, however, LAPB is restricted to the ABM transfer mode and is appropriate only for combined stations. LINKED ACCESS PROTOCOL - D CHANNEL (LAPD) ISDN emerged as an alternative to traditional dialup networking .It is a set of communication standards for simultaneous digital transmission of voice, video, data, and other network services over the traditional circuits of the public switched telephone networks. It provides a single, common interface with which to access digital communications services that are required by varying devices, while remaining transparent to the user. ISDN standards are constructed using the Open System Interconnection seven- layer reference model. Linked Access Protocol (D Channel) is a Layer 2 (data link) protocol. D channel is the data or signalling channel which is used for communications (or "signalling") between switching equipment in the ISDN network and the ISDN equipment at your site. The LAPD handle the handshaking (commands and responses), signalling, and control for all of the voice and data calls that are setup through the ISDN D channel. LAPD works in the Asynchronous Balanced Mode (ABM). This mode is totally balanced (i.e., no master/slave relationship). Each station may initialize, supervise, recover from errors, and send frames at any time. The objective of LAPD is to provide a secure, error-free connection between two end-points
- 42. MODULE I MCA-402 Computer Networks ADMN 2012-‘15 Dept. of Computer Science And Applications, SJCET, Palai Page 42 so as to reliably transport Layer 3 messages. The control field of LAPD frame is identical to HDLC, but the address field differs. Fig 1.49 LAPD frame format The first Address-field byte contains the service access point identifier (SAPI), which identifies the portal at which LAPD services are provided to Layer 3.The C/R bit indicates whether the frame contains a command or a response. The Terminal Endpoint Identifier (TEI) field identifies either a single terminal or multiple terminals compatible with the ISDN network. Example: Telephones, personal computers
